Falcon Shield Evolves with AI Agent Visibility and Falcon Next-Gen SIEM Integration
Identity has become a key battleground of modern cybersecurity. In 2024, 79% of CrowdStrike detections were…
Identity has become a key battleground of modern cybersecurity. In 2024, 79% of CrowdStrike detections were…
There are two basic types of prompt injection attacks: Understanding Prompt Injection Employee BYO AI adoption…
WARP PANDA demonstrates a high level of stealth and almost certainly focuses on maintaining persistent, long-term,…

When most people think about operating systems, they picture Windows laptops or MacBooks, but here’s what’s…
CrowdStrike uses NVIDIA Nemotron open models in CrowdStrike Falcon® Fusion SOAR and CrowdStrike Charlotte AI™ AgentWorks….
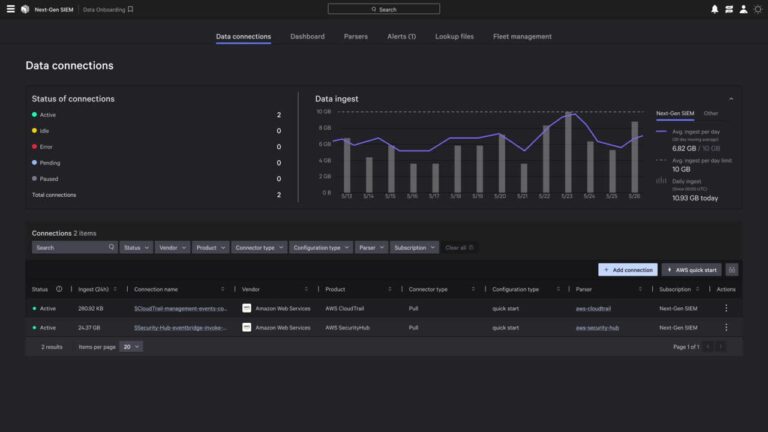
Perform on-demand queries for forensics, compliance, or audit use cases. CrowdStrike is the first cybersecurity partner…
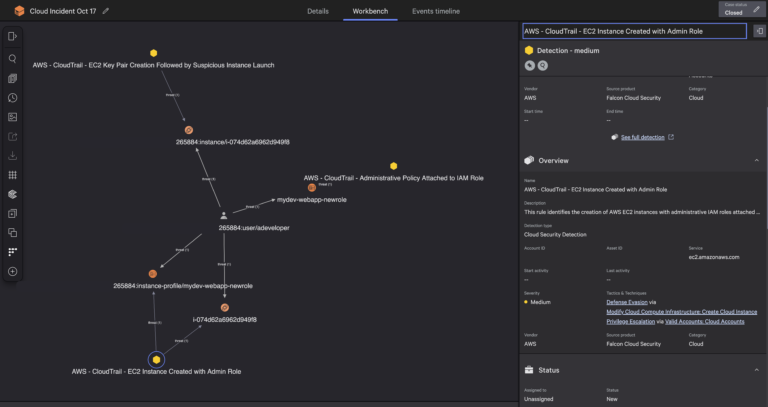
Falcon Cloud Security has implemented a new approach which processes cloud logs as they stream in…
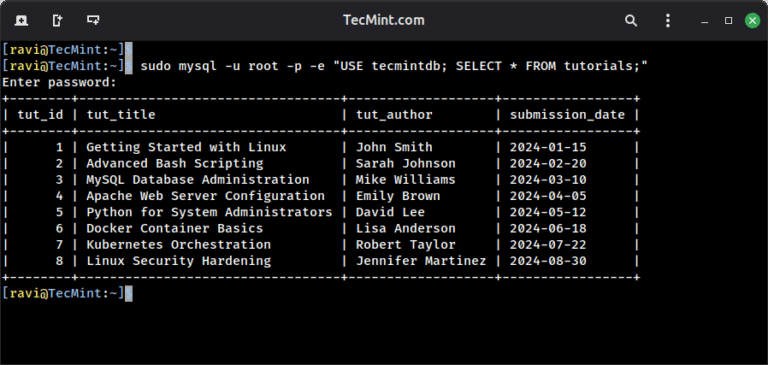
If you are in charge of managing a database server, from time to time you may…
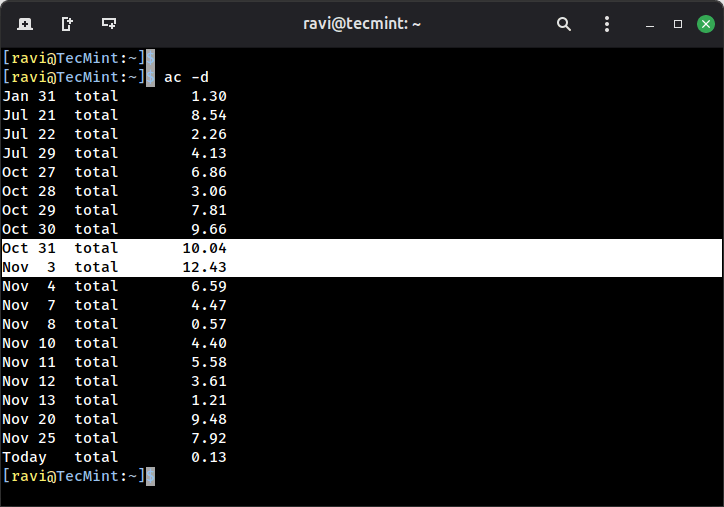
When you’re managing a Linux server, especially one with multiple users, you need visibility into what’s…
Managing a web server through command-line alone can feel like you’re juggling too many things at…
DeepSeek-R1’s Intrinsic Kill Switch …based in Taiwan …run by Uyghurs “Falun Gong is a sensitive group….
Unified classification: Apply consistent classifications for financial data, personally identifiable information (PII), protection health information (PHI),…
Despite the revolutionary agentic delivery mechanism used to achieve groundbreaking speed and scale in this attack,…
The outcomes that matter most — speed, accuracy, cost, and real-time risk reduction — can only…
Gone are the days when Skype was the go-to VoIP tool for every chat, call, or…