How To Create an Effective Ecommerce Return Policy and Process
Conduct research on your competitors to see what types of terms they include in their return…

Conduct research on your competitors to see what types of terms they include in their return…

What are the best WordPress Security plugins and how to set them up the best way…

The Most Important Stages and Plugins for WordPress Website Development Developing a WordPress website requires careful…
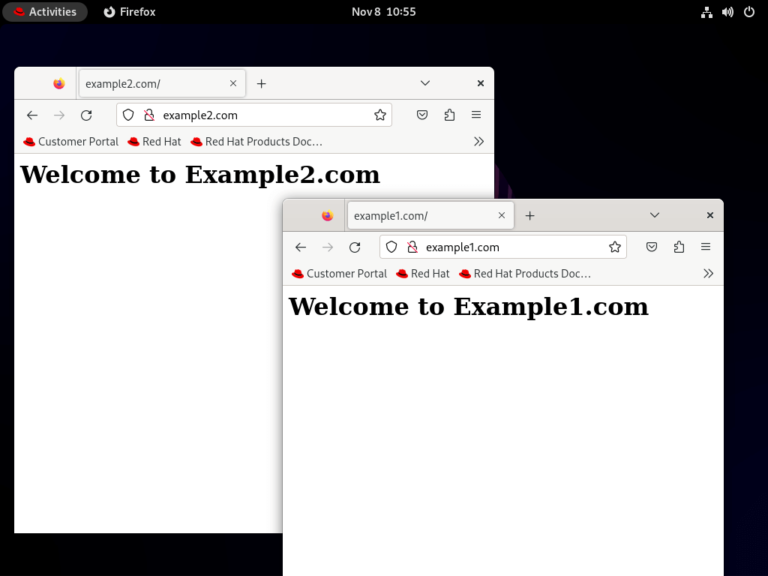
Powerful SEO Tools for WordPress Search Engine Optimisation (SEO) is essential for improving your WordPress website’s…
“The comprehensive coverage of the SaaS ecosystem fueled by solid threat prevention, detection, and response capabilities…
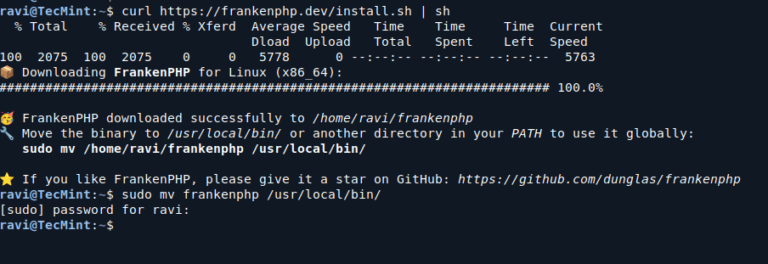
FrankenPHP is a modern application server for PHP that enhances the performance and capabilities of PHP…

Trust icons quickly communicate key value propositions and benefits in a visual way, allowing the user…

In the competitive landscape of e-commerce hosting, leveraging the right tools can be a game changer…
The log collector itself focuses exclusively on ingesting third-party and external log data, complementing native CrowdStrike…
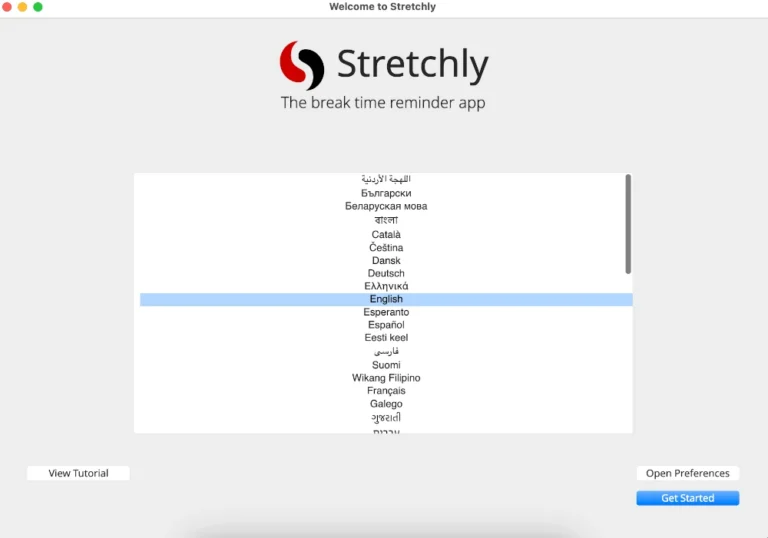
In this article, you will discover 3 excellent break reminder apps for Linux that help prevent…
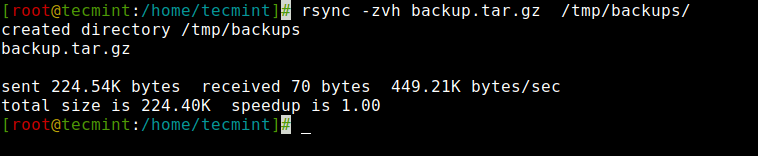
In this article, you will learn how to copy, sync, backup, and transfer files locally and…
This milestone comes as the UK places increased emphasis on cyber resilience, operational assurance, and incident…

Stopping compromised access at login is essential, but identity risk doesn’t end there. CrowdStrike acquired SGNL…
To defend themselves, security leaders need clarity on which adversaries to watch, the details of their…
Adversaries’ ability to easily establish seemingly legitimate infrastructure poses significant risks to organizations of all sizes….
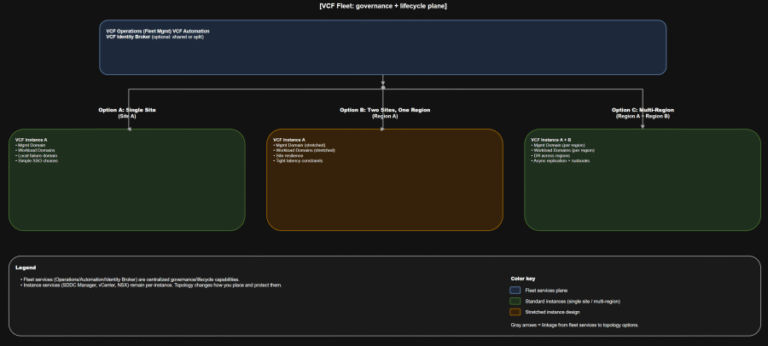
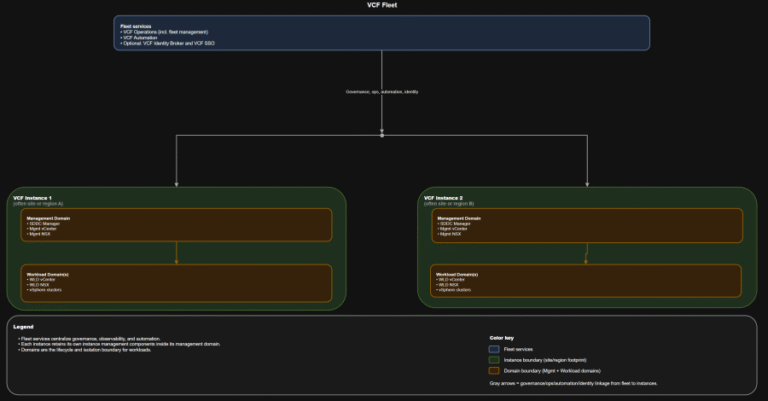
TL;DR Scope: VMware Cloud Foundation 9.0.0.0 GA (primary platform build 24703748) and the associated 9.0 GA…
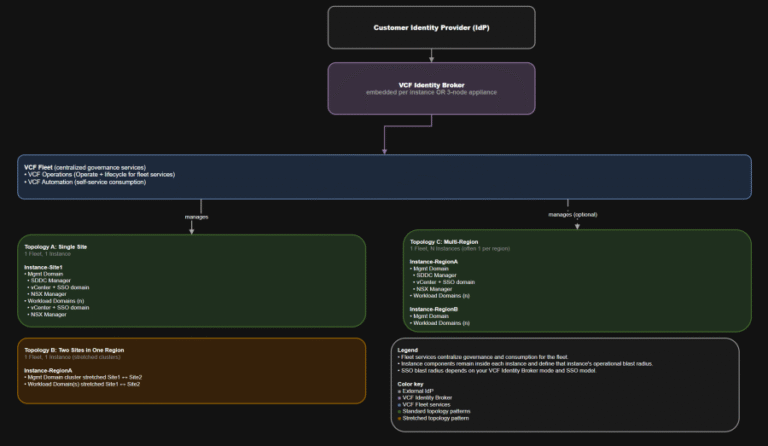
TL;DR Identity is not a “later” decision. It is a boundary decision. The hierarchy you should…
TL;DR This post targets VCF 9.0 GA only: VCF 9.0 (17 JUN 2025) build 24755599, with…
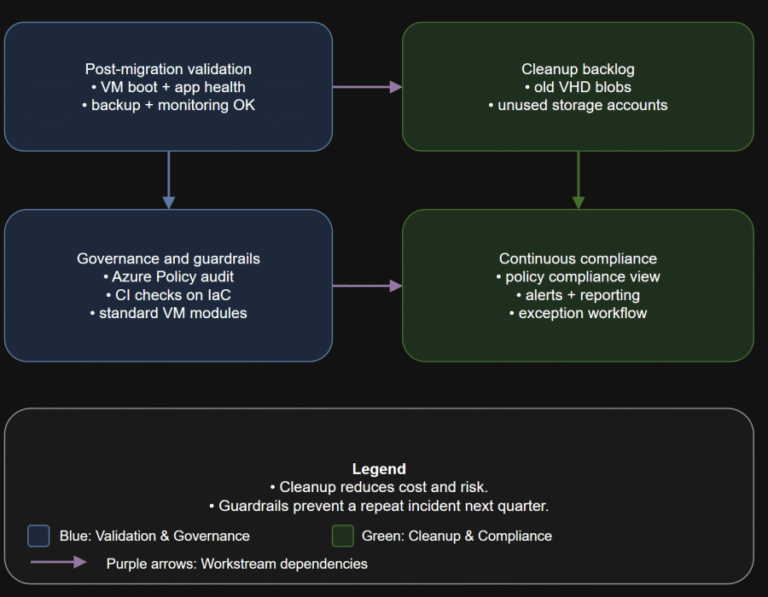
TL;DR Converting disks is not the finish line. Your real goal is a new steady state:…
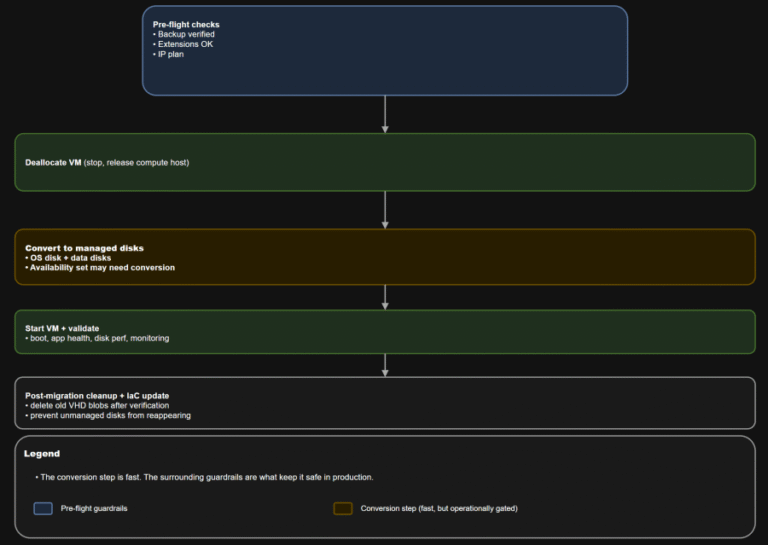
TL;DR Converting a VM to managed disks is usually operationally straightforward: deallocate, convert, start, validate. The…
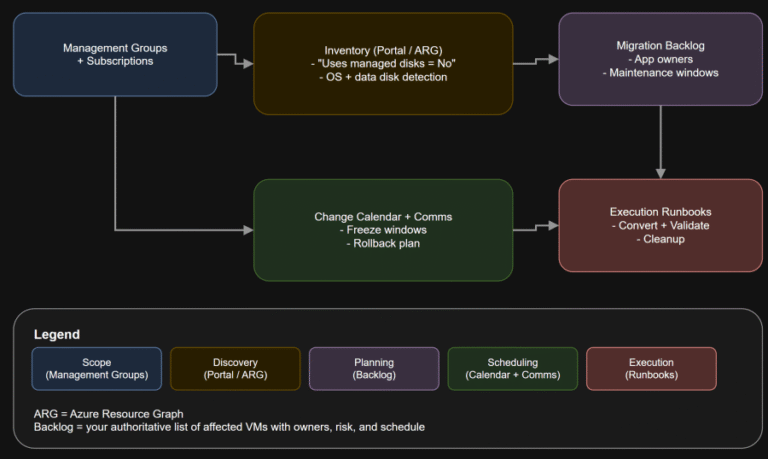
TL;DR If any Azure IaaS VM in your estate still uses unmanaged disks, it is on…
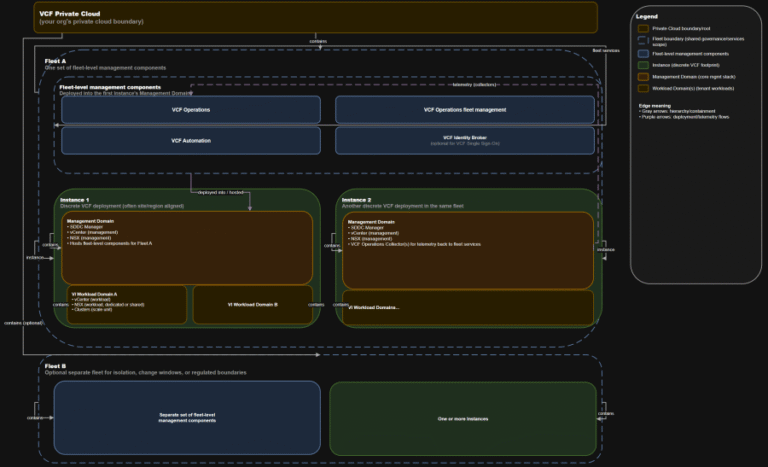
TL;DR A) One fleet, one instance, stretched where justified In VCF 9.0, identity is not a…
Insider threats pose a growing risk to organizations. Whether insiders take malicious actions, exhibit negligent behavior,…