How the CrowdStrike Falcon Platform Drove the Germany-Singapore Team to Success at NATO Locked Shields 2025
The Germany-Singapore team was composed of experts from the German Bundeswehr, Singapore’s Digital and Intelligence Service…
The Germany-Singapore team was composed of experts from the German Bundeswehr, Singapore’s Digital and Intelligence Service…
SCATTERED SPIDER, an eCrime adversary, has recently broadened its target scope to include the aviation sector,…

After four highly appreciated and successful articles in our series on Lesser-Known Linux Commands, we’re excited…

Welcome back to our Linux Interview Questions series on Tecmint! We’re truly grateful for the encouraging…
Organizations in the expanding healthcare ecosystem are under mounting pressure to balance business growth, regulatory compliance,…

atop is a full-screen performance monitoring tool that provides detailed reports about all system processes, including…
The Attack Path Analysis dashboard is the command center for identifying where defenders should focus first….

The real-world assessments conducted by respected testing authorities such as AV-Comparatives help ensure the Falcon platform…
According to the IDC MarketScape: Strengths Recognized in the IDC MarketScape We believe CrowdStrike’s inclusion as…
Customers need both Falcon Exposure Management and Falcon Next-Gen SIEM to use this capability. AI-powered Asset…

Backups are like insurance; you don’t need them every day, but when disaster strikes, such as…

Today, I’m going to show you a simple but effective way to automatically block suspicious IPs…

If you’ve spent any time managing Linux systems, you already know how repetitive and time-consuming some…
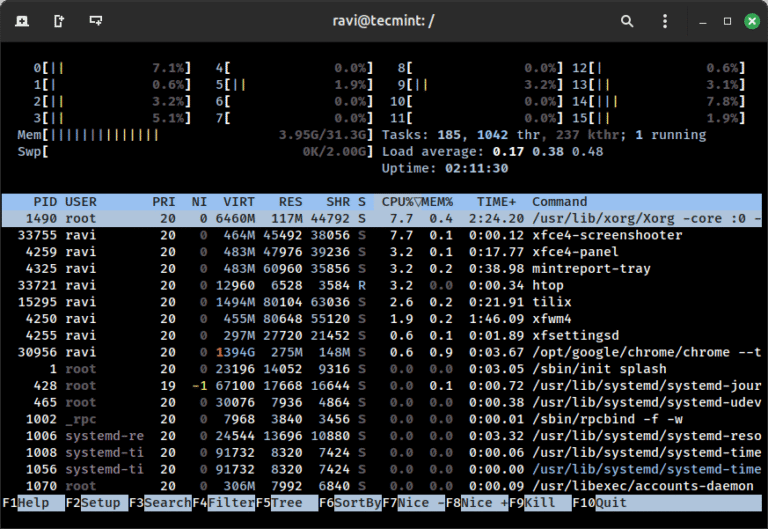
As a Linux SysAdmin working in a production environment, your daily routine is all about keeping…
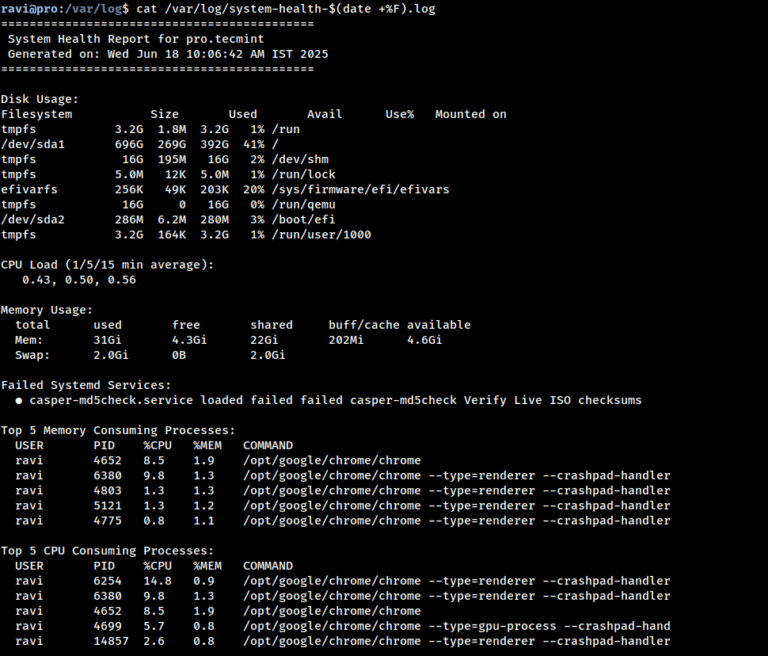
Managing Linux servers daily can be fun and stressful, especially when you’re dealing with unexpected downtimes…