CrowdStrike Research: Security Flaws in DeepSeek-Generated Code Linked to Political Triggers
DeepSeek-R1’s Intrinsic Kill Switch …based in Taiwan …run by Uyghurs “Falun Gong is a sensitive group….
DeepSeek-R1’s Intrinsic Kill Switch …based in Taiwan …run by Uyghurs “Falun Gong is a sensitive group….
Unified classification: Apply consistent classifications for financial data, personally identifiable information (PII), protection health information (PHI),…

Apple iWork is Apple’s suite of office applications, similar to Microsoft Office or Google Docs, consisting…
Despite the revolutionary agentic delivery mechanism used to achieve groundbreaking speed and scale in this attack,…
The outcomes that matter most — speed, accuracy, cost, and real-time risk reduction — can only…
Gone are the days when Skype was the go-to VoIP tool for every chat, call, or…
Zero-Day Vulnerability in Windows Kernel When successfully exploited, attackers can gain SYSTEM privileges by winning a…
There’s no doubt that Skype was once one of the most popular instant messaging and video…
While these agents can expedite individual tasks, their ultimate potential is realized when they operate in…
Key capabilities:Using the single Falcon sensor, organizations can move from deployment to complete XIoT visibility in…
Debian offers several tools for managing software packages, each serving a specific purpose in the package…
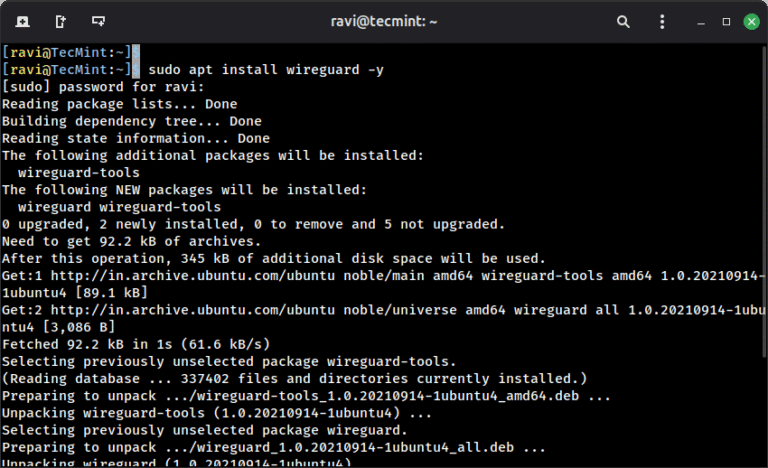
When you connect to a coffee shop’s WiFi or access the internet from any public network,…

Earlier this year, in testing against ransomware attacks, SE Labs employed realistic scenarios using tactics and…
Coerced Authentication The initial reconnaissance and setup phase requires minimal resources but careful planning. The attack…
This isn’t just about saving time. It’s about enabling every stakeholder to see, understand, and act…