How to Install Unison File Synchronizer for Two-Way File Sync on Linux
Keeping files in sync across multiple machines is a common task for Linux users. You might…

Keeping files in sync across multiple machines is a common task for Linux users. You might…
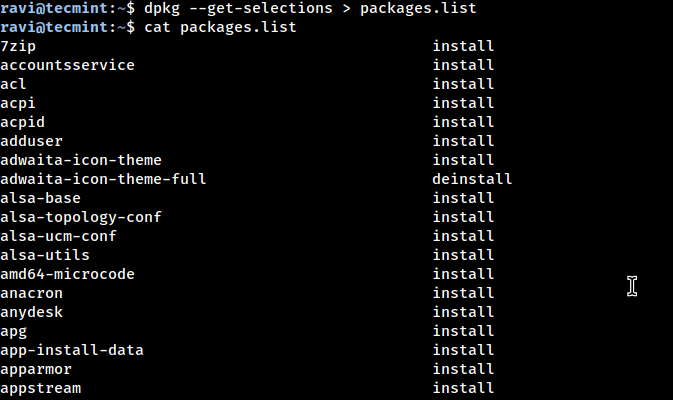
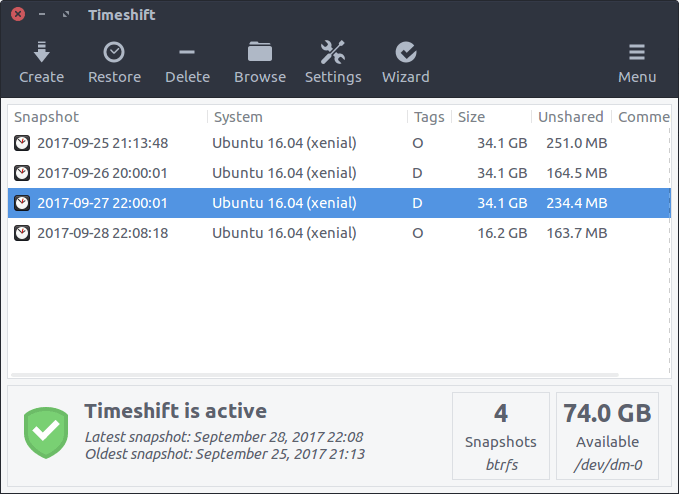
If you’ve ever reinstalled Ubuntu, you know the pain of setting everything up again, such as…
It isn’t easy to figure out which of the many Linux apps out there are actually…
Linux Mint 22.2 (“Zara”) is the latest point release in the Linux Mint 22 series, which…

As a Linux user, you may eventually run into a situation where your root partition (/)…
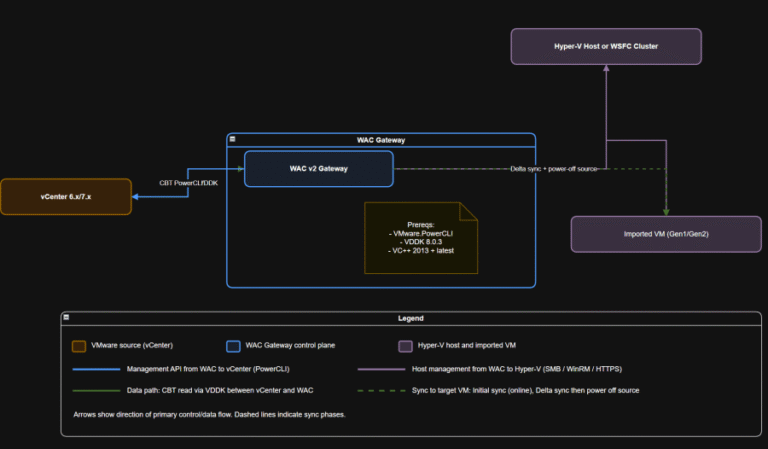
Compliance checkpoints (examples) Why this matters Bridge strategy: If you are standardizing on Windows Server and…
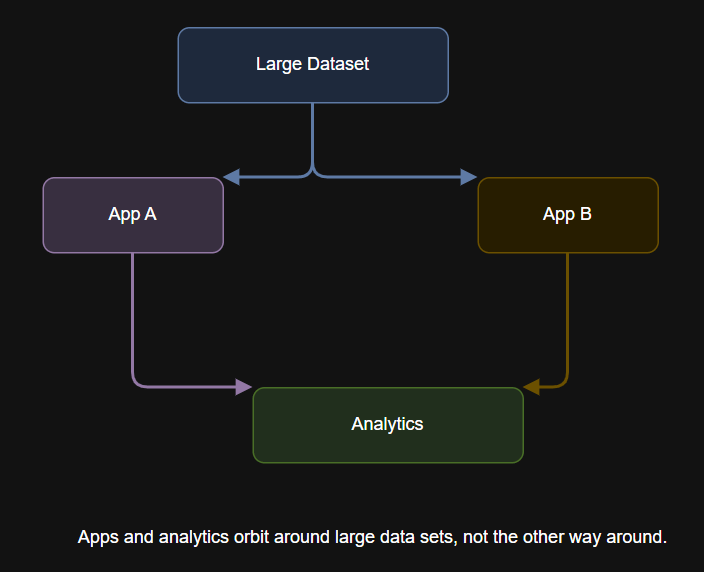
Table of Contents What Is Data Gravity? The History and Evolution of Data Gravity Why Data…

TL;DR Inversion forces clarity: name how you’ll fail, then design your safeguards, signals, and contingencies. Copy…
Since late 2024, CrowdStrike Counter Adversary Operations has observed significant activity conducted by MURKY PANDA, a…
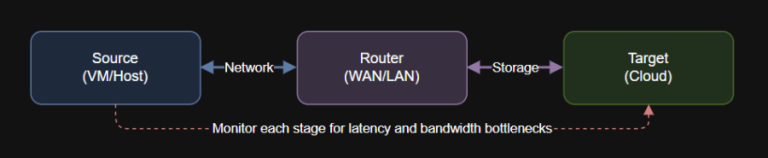
Introduction Data movement in cloud and hybrid architectures is only as fast as your slowest link….
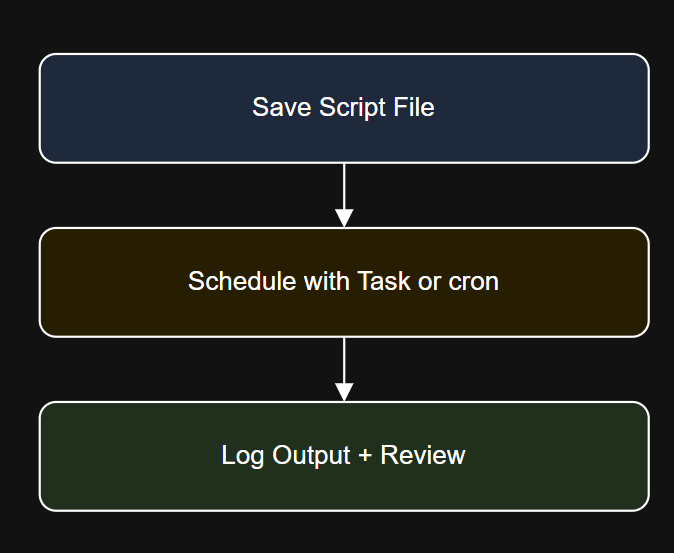
Introduction crontab -l Diagram: PowerCLI Scheduling Workflow Step 4: Use Credential Storage Securely Click OK, enter…
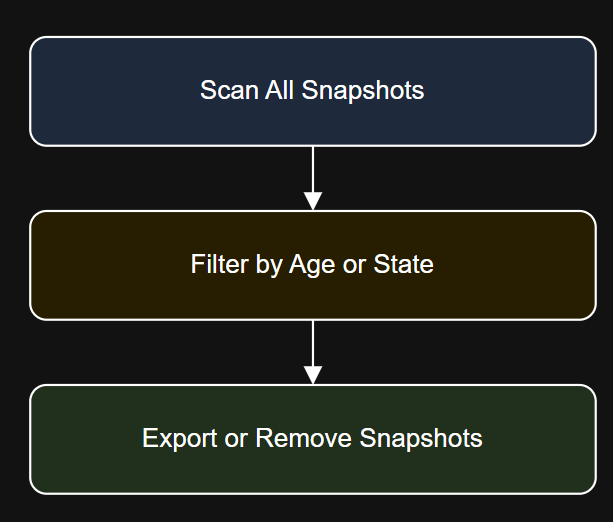
Introduction Get-VM | Where-Object {$_.PowerState -eq “PoweredOff”} | Get-Snapshot | Remove-Snapshot -Confirm:$false Diagram: Snapshot Lifecycle Workflow…

There are countless cloud storage platforms that provide safe and secure storage space for your files….
Introduction This playbook gives you complete control over Nutanix VM snapshots, ensuring consistency, compliance, and automation…