Falcon for IT Redefines Vulnerability Management with Risk-based Patching
Traditional vulnerability management is broken. Security teams rely on one set of tools to find vulnerabilities;…
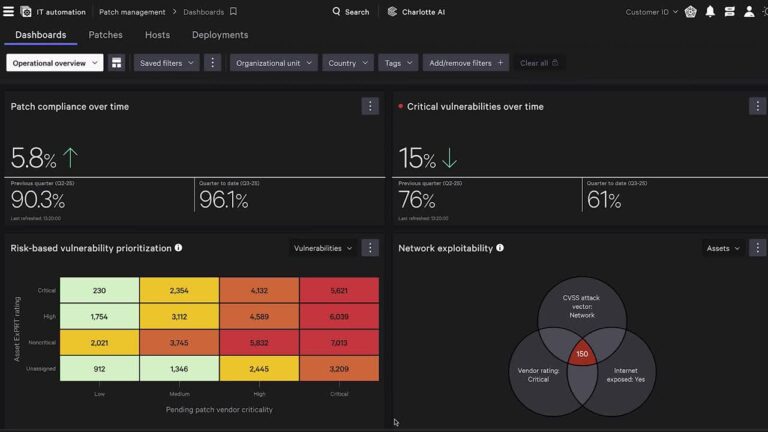
Traditional vulnerability management is broken. Security teams rely on one set of tools to find vulnerabilities;…
As enterprises adopt AI agents and embed them into SaaS workflows, visibility and governance become essential….

Many security teams struggle with threat hunting because they don’t know where to start or what…
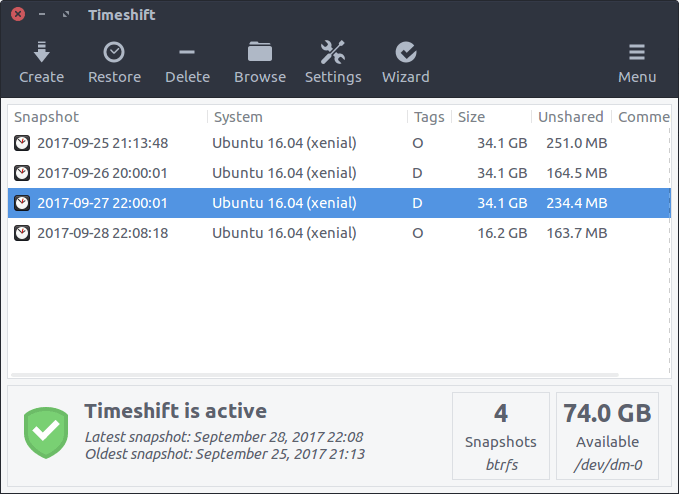
It isn’t easy to figure out which of the many Linux apps out there are actually…
The Falcon platform’s console unifies fragmented data, bridges silos, and translates complex queries into natural-language conversations….
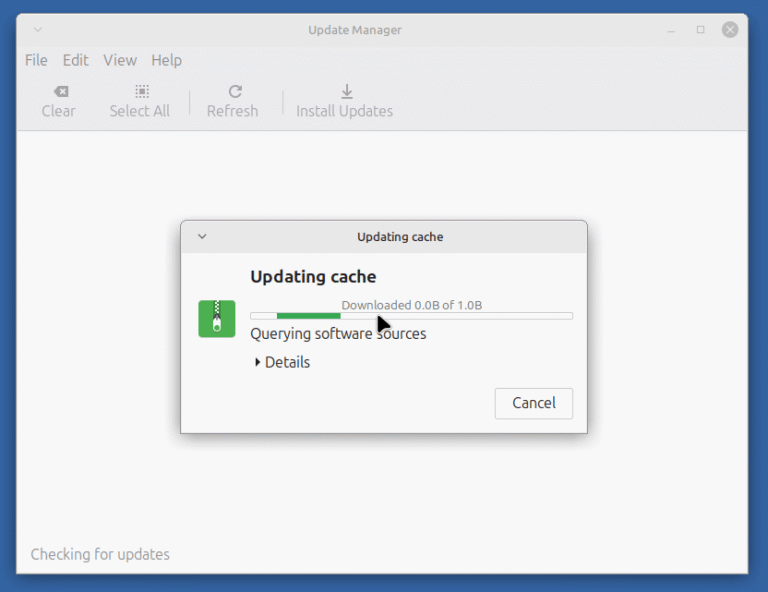
Linux Mint 22.2 (“Zara”) is the latest point release in the Linux Mint 22 series, which…
With Pangea, CrowdStrike will extend this protection into the interaction layer of AI to secure how…

As a Linux user, you may eventually run into a situation where your root partition (/)…
The Hub doesn’t just display what’s happening — it tells teams what to do about it…

Want to play Windows games on your Linux system but not sure where to begin? Heard…
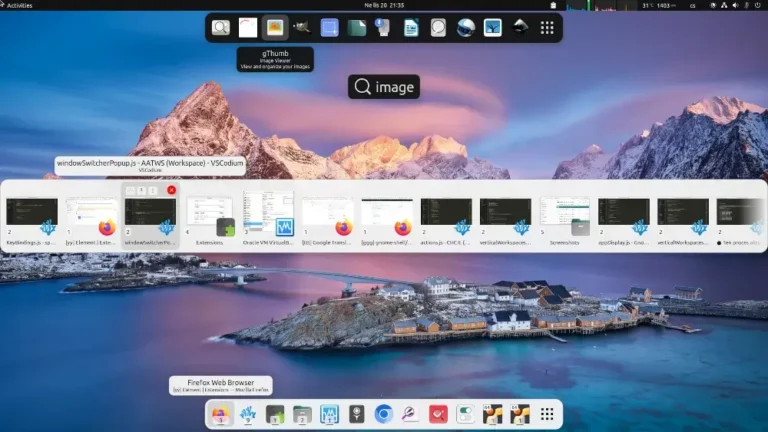
Do you feel like your Ubuntu desktop turns messy the moment you open more than a…
Publicly Disclosed Zero-Day Vulnerability in Windows SMB CVE-2025-55226 is a Critical remote code execution vulnerability affecting…

Make the process as simple as possible by offering guest checkout options, enabling auto-fill for payment…
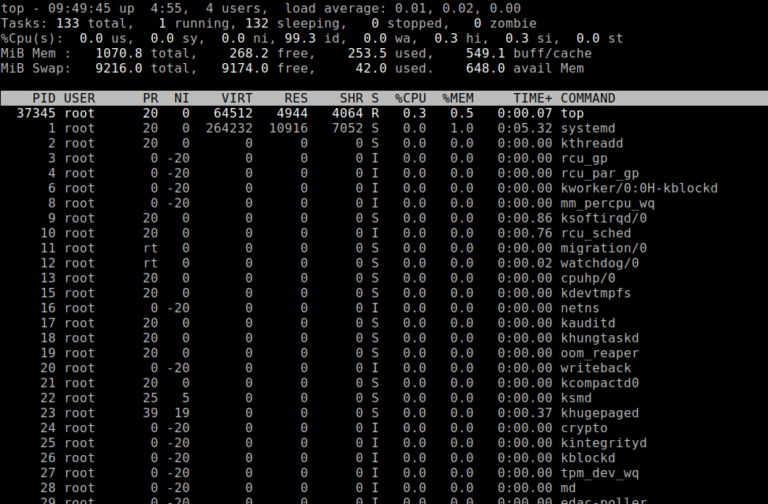
Being a System or Network administrator tasked with monitoring and debugging Linux system performance problems on…
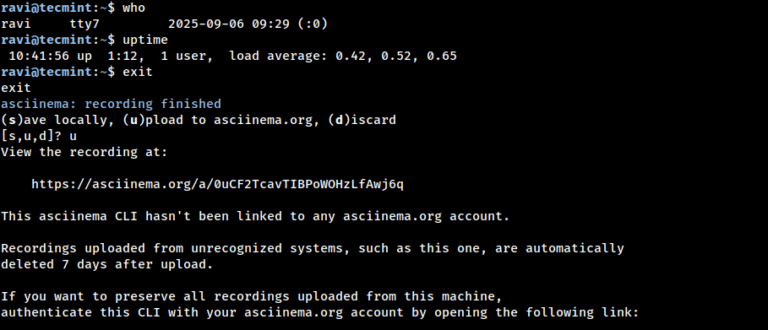
Asciinema is an open-source terminal recording tool that makes it super easy to share your command-line…