CrowdStrike Falcon Wins AV-Comparatives Awards for EDR Detection and Mac Security
The real-world assessments conducted by respected testing authorities such as AV-Comparatives help ensure the Falcon platform…

The real-world assessments conducted by respected testing authorities such as AV-Comparatives help ensure the Falcon platform…
Customers need both Falcon Exposure Management and Falcon Next-Gen SIEM to use this capability. AI-powered Asset…
According to the IDC MarketScape: Strengths Recognized in the IDC MarketScape We believe CrowdStrike’s inclusion as…

Backups are like insurance; you don’t need them every day, but when disaster strikes, such as…

Today, I’m going to show you a simple but effective way to automatically block suspicious IPs…

If you’ve spent any time managing Linux systems, you already know how repetitive and time-consuming some…
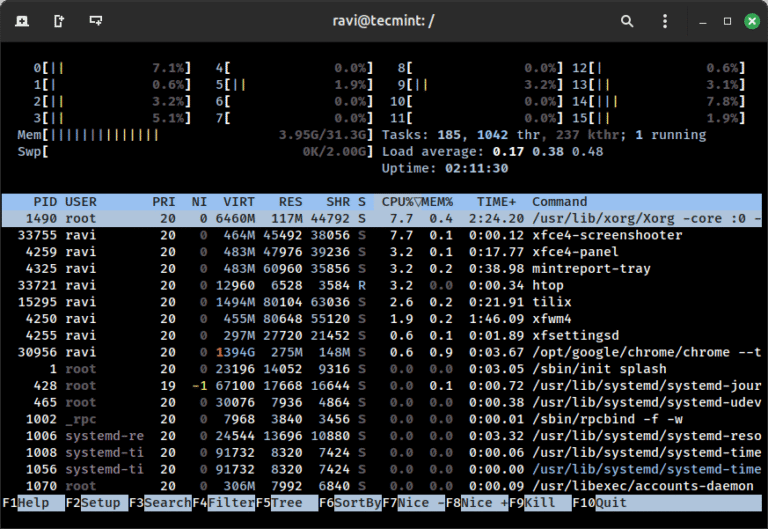
As a Linux SysAdmin working in a production environment, your daily routine is all about keeping…
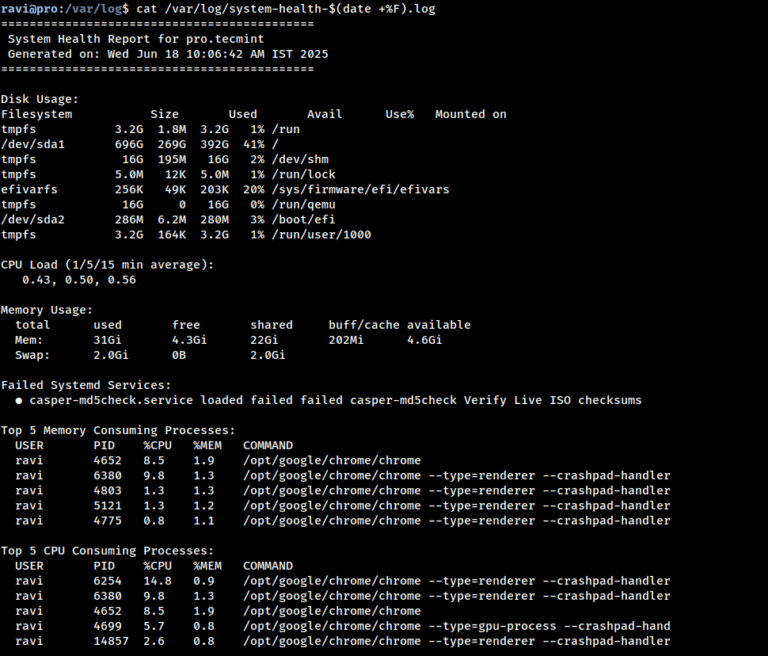
Managing Linux servers daily can be fun and stressful, especially when you’re dealing with unexpected downtimes…
However, the memory patching approach is quite noisy from an attacker perspective because it can raise…
LABYRINTH CHOLLIMA is a DPRK-nexus adversary that CrowdStrike has observed consistently targeting cloud environments.1 Below are…
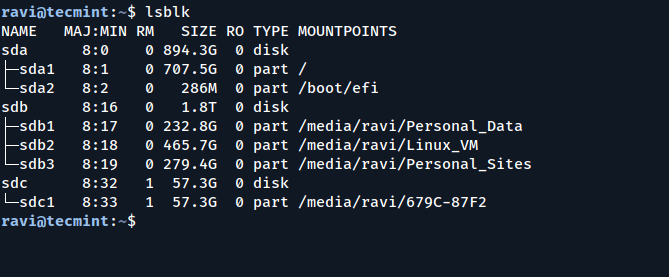
If you’ve ever plugged in a USB stick on a Linux machine and found that you…
CrowdStrike researchers have created a proof-of-concept framework that uses dynamic feedback-guided fuzzing to identify large language…
Actively Exploited Zero-Day Vulnerability in Web Distributed Authoring and Versioning While exploitation requires the attacker to…
One challenge of correlating all of the attack stages together is the events for uploading an…
Today’s adversaries have their sights set on identities. They’re using stolen credentials and social engineering techniques…