Automating VM Lifecycle Actions and Snapshots with PowerCLI and Python
Learning Objectives # DisconnectDisconnect-VIServer -Server * -Confirm:$false Automate common VM lifecycle actions such as power on,…
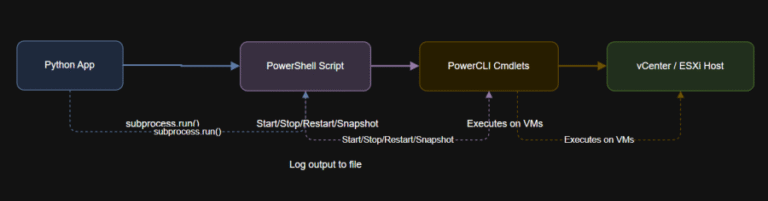
Learning Objectives # DisconnectDisconnect-VIServer -Server * -Confirm:$false Automate common VM lifecycle actions such as power on,…
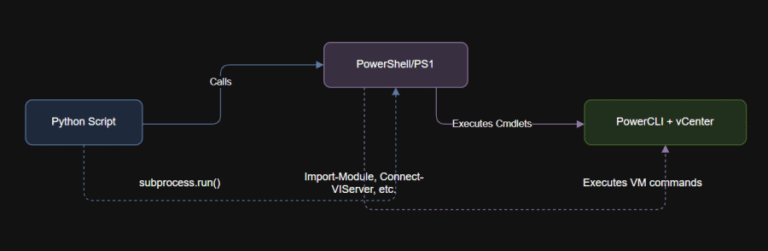
Learning Objectives Now, use Python to call that script. Here’s a basic example: Understand the differences…
Security teams today face a data crisis: Exploding volumes of security and IT telemetry are difficult…
Publicly Disclosed Zero-Day Vulnerability in Windows Kerberos As we have learned with other notable vulnerabilities, such…
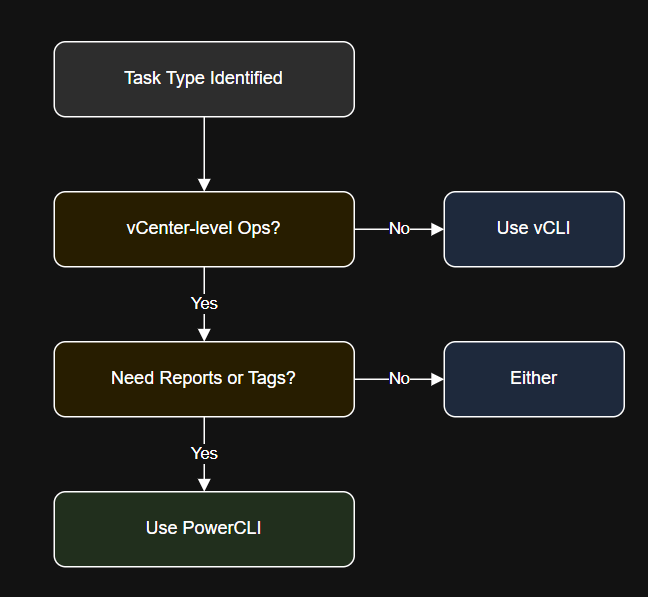
Introduction In this article, you’ll learn: Install using VMware downloads or use the VMA (vSphere Management…
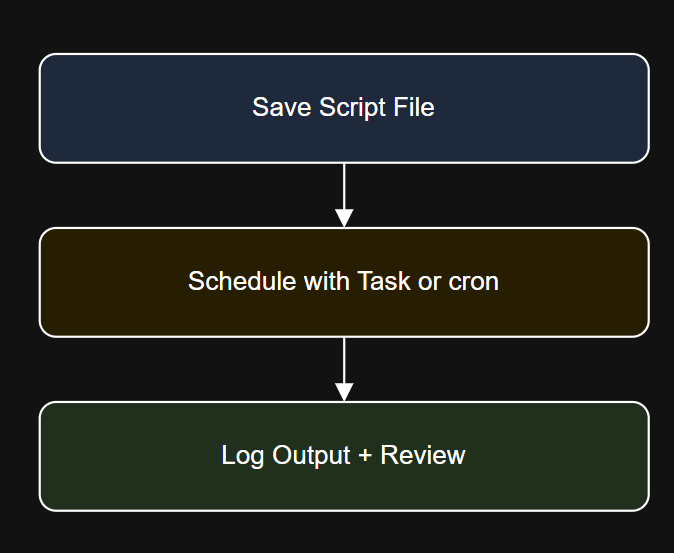
Introduction crontab -l Diagram: PowerCLI Scheduling Workflow Step 4: Use Credential Storage Securely Click OK, enter…
CD and DVD writers are a thing of the past. You are not likely to find…
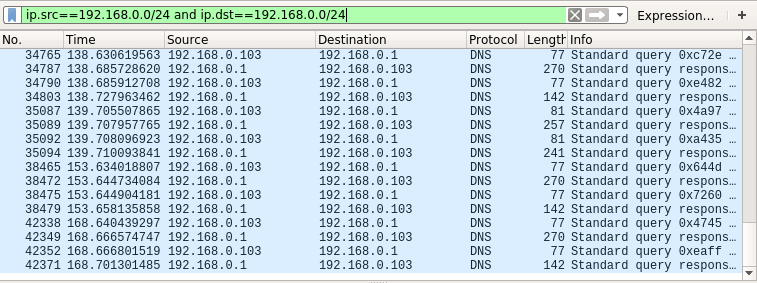
A system administrator’s routine tasks include configuring, maintaining, troubleshooting, and managing servers and networks within data…
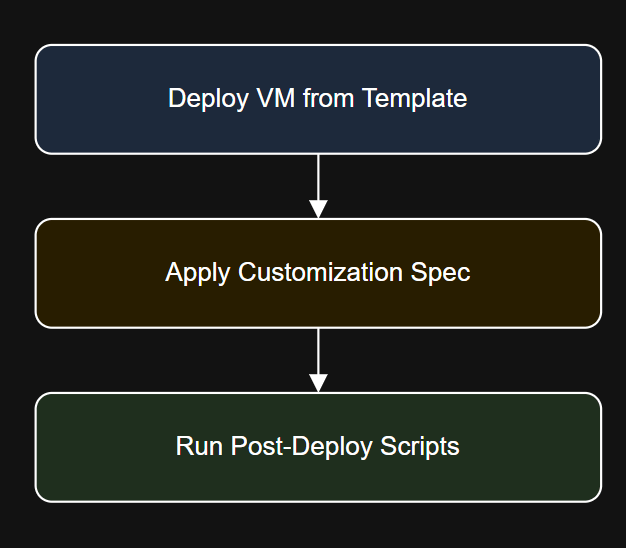
Introduction In the next article, we will cover: $servers = Import-Csv “C:ConfigsLinuxVMs.csv”You can store custom values…
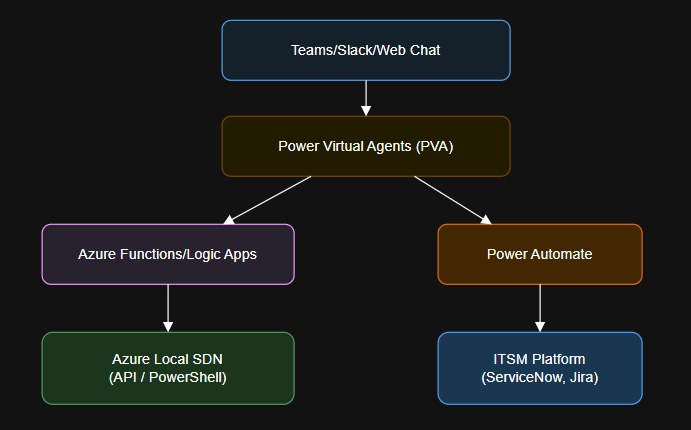
Table of Contents Introduction What Is ChatOps and Why Use It for Azure Local SDN? Architecture…
Envisioning the Future of Endpoint Protection Gartner has positioned CrowdStrike furthest right in Completeness of Vision…

These tactics are part of a broader shift. As adversaries increasingly rely on unmanaged infrastructure to…
Over the past year, we’ve expanded and strengthened the digital operations capabilities that have long supported…

Introduction Bicep Example: If you’re an architect or engineer aiming to master network automation, policy enforcement,…

OCR stands for optical character recognition, and software of this type is designed to convert images,…