CrowdStrike Falcon Wins AV-Comparatives Awards for EDR Detection and Mac Security
The real-world assessments conducted by respected testing authorities such as AV-Comparatives help ensure the Falcon platform…

The real-world assessments conducted by respected testing authorities such as AV-Comparatives help ensure the Falcon platform…
However, the memory patching approach is quite noisy from an attacker perspective because it can raise…
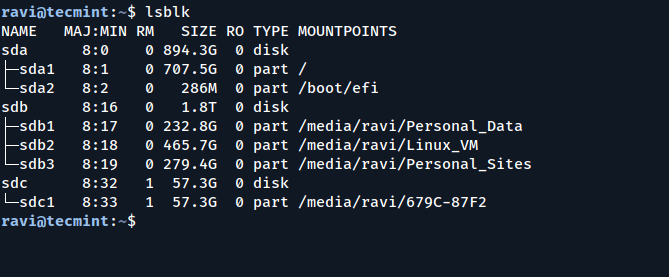
If you’ve ever plugged in a USB stick on a Linux machine and found that you…
Actively Exploited Zero-Day Vulnerability in Web Distributed Authoring and Versioning While exploitation requires the attacker to…
One challenge of correlating all of the attack stages together is the events for uploading an…
“CrowdStrike Falcon is excellent at detecting anomalous activity where traditional antivirus is otherwise incapable of detecting…

Keylogging, short for “keystroke logging” is the process of recording the keys struck on a keyboard,…

Midori is an open-source, lightweight, and fast web browser designed for people who want a simple…
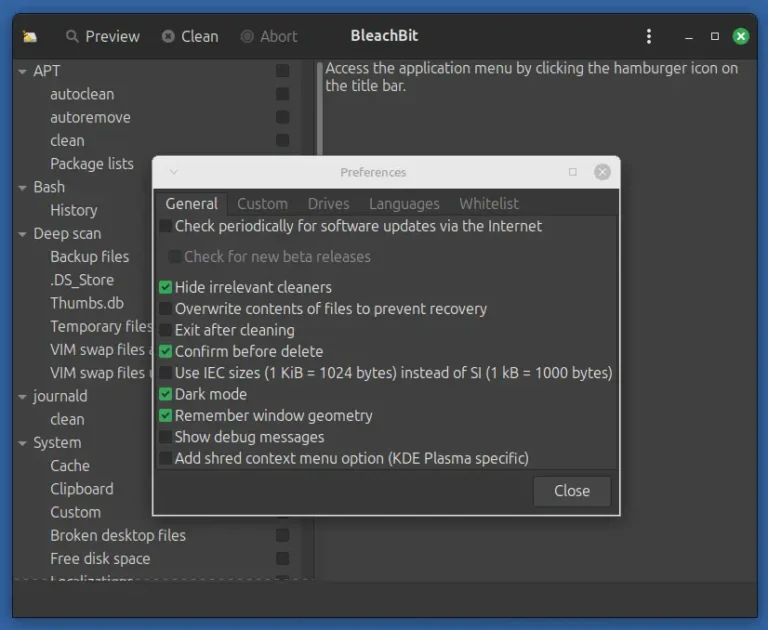
When you browse the internet, install or uninstall software, or just use your computer regularly, you…
Actively Exploited Zero-Day Vulnerabilities in Windows Common Log File System The CrowdStrike Falcon platform regularly collects…

Linux is one of the most widely used operating systems in both personal and enterprise environments….
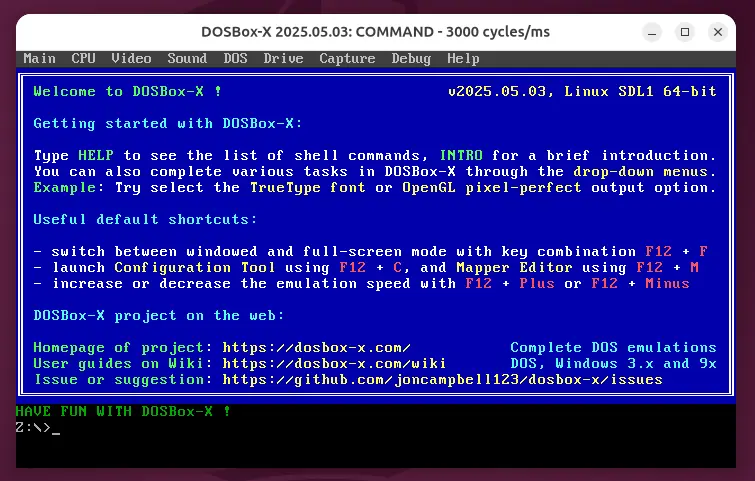
Ever wanted to play classic DOS games or run old compilers like Turbo C++ or MASM…
Ubuntu is one of the most popular Linux distributions for new users, offering an easy-to-use interface…
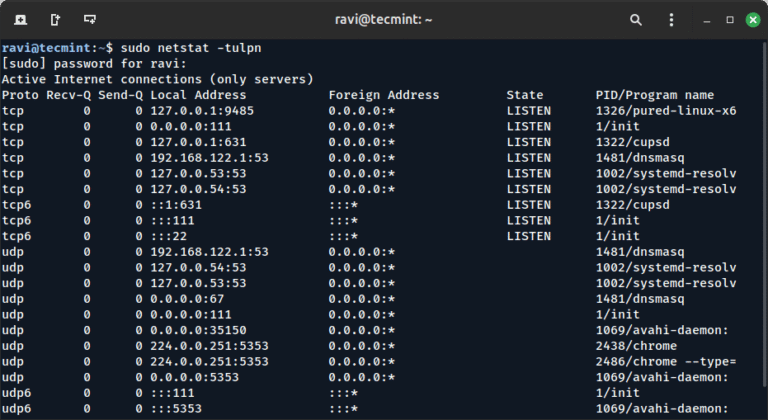
If you’re preparing for a networking, Linux system administration, DevOps, or cybersecurity interview, understanding network ports…
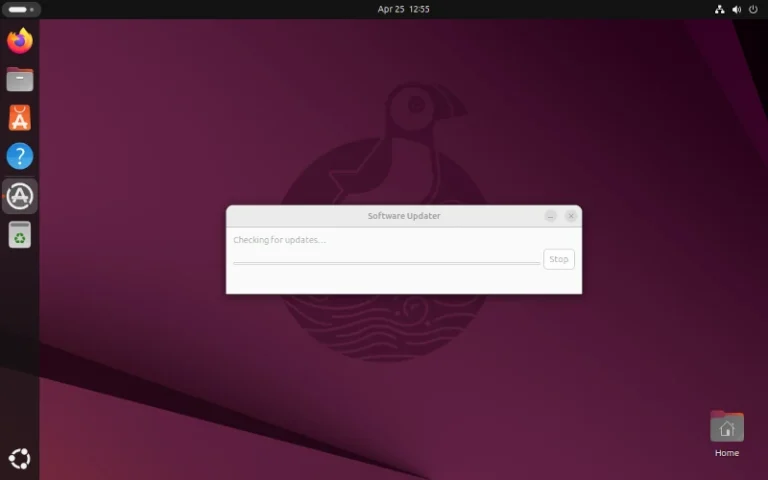
So, you’ve just installed Ubuntu 25.04 “Plucky Puffin” on your computer—congrats! I recently did the same,…