7 Best Udemy Android Development Courses in 2025
Android software development involves creating applications for devices running the Android operating system, primarily using Kotlin…

Android software development involves creating applications for devices running the Android operating system, primarily using Kotlin…

Google Cloud Platform is a suite of cloud computing services that shares its running environment with…
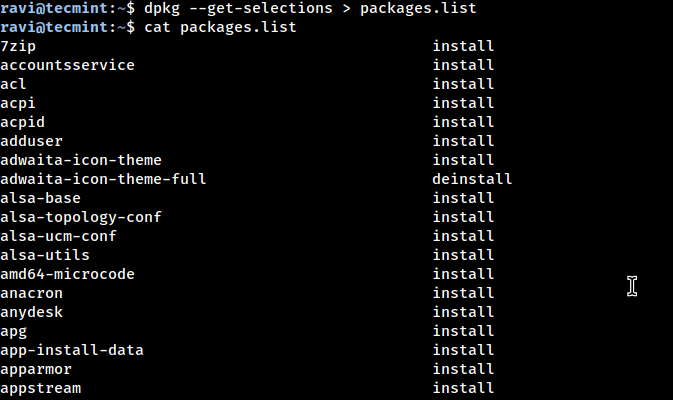
If you’ve ever reinstalled Ubuntu, you know the pain of setting everything up again, such as…
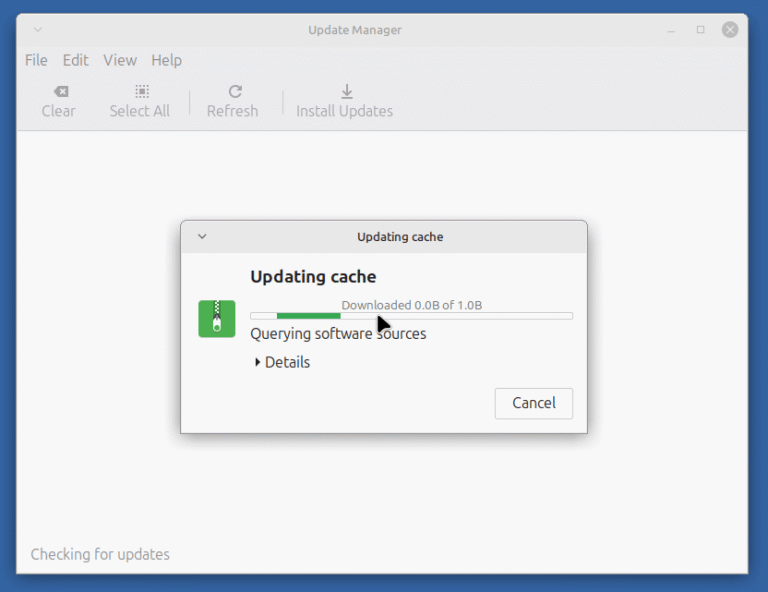
Linux Mint 22.2 (“Zara”) is the latest point release in the Linux Mint 22 series, which…
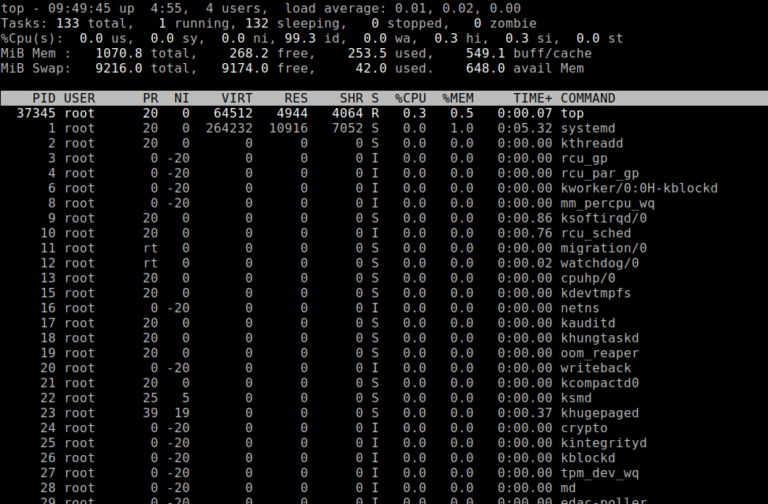
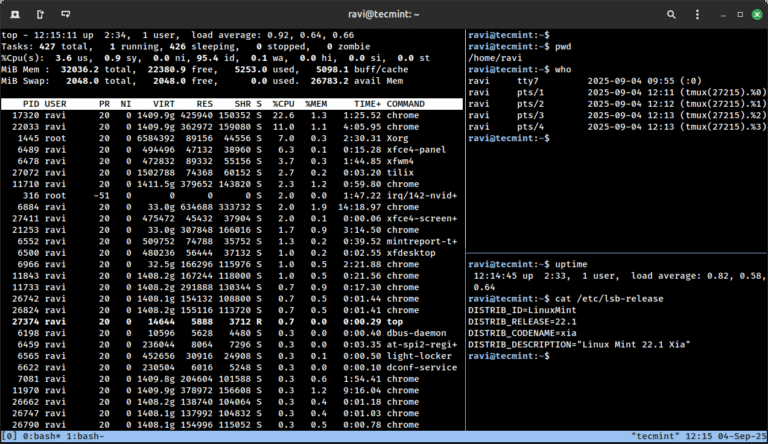
Being a System or Network administrator tasked with monitoring and debugging Linux system performance problems on…
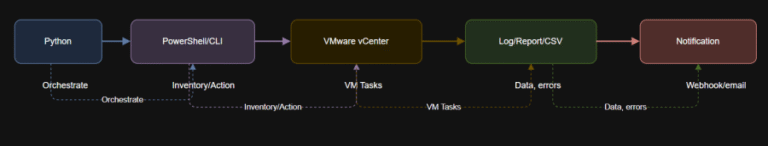
Learning Objectives VMware Repository on GitHub See how a single Python script can orchestrate inventory, lifecycle,…
It is time once again to share a list of the best free and open-source software…

Zip is a command-line utility tool used for compressing files and folders. Compression of files &…
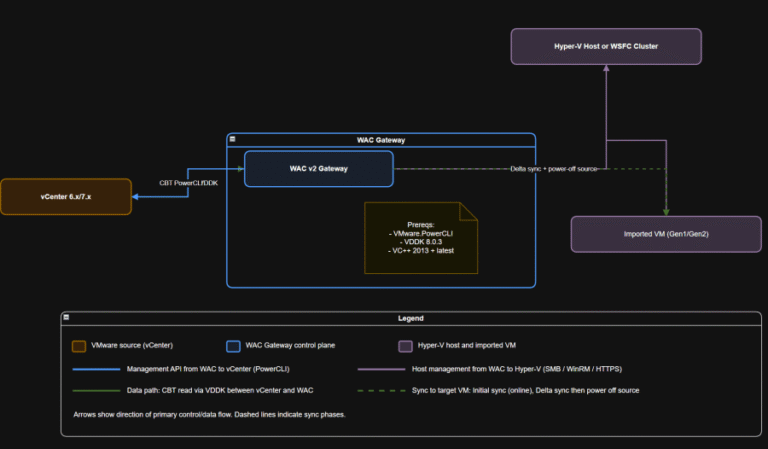
Compliance checkpoints (examples) Why this matters Bridge strategy: If you are standardizing on Windows Server and…
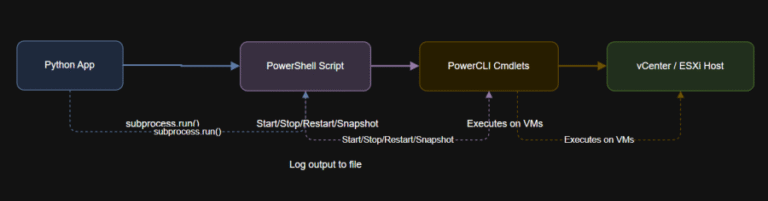
Learning Objectives # DisconnectDisconnect-VIServer -Server * -Confirm:$false Automate common VM lifecycle actions such as power on,…
Security teams today face a data crisis: Exploding volumes of security and IT telemetry are difficult…
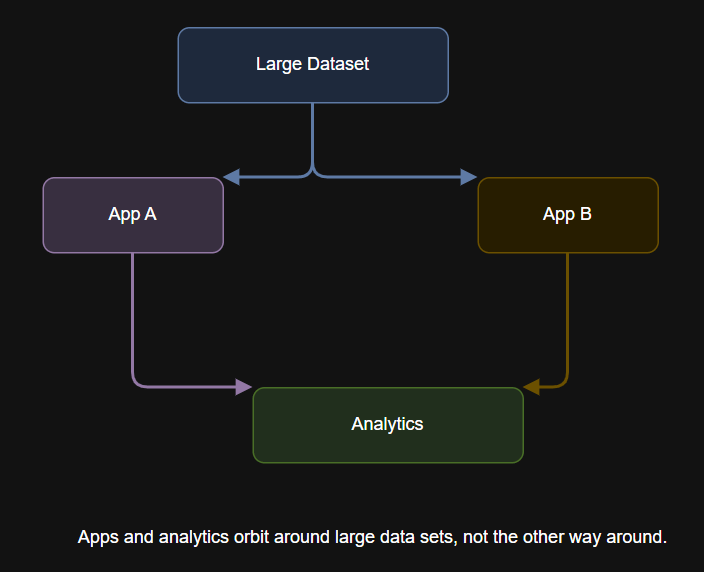
Table of Contents What Is Data Gravity? The History and Evolution of Data Gravity Why Data…
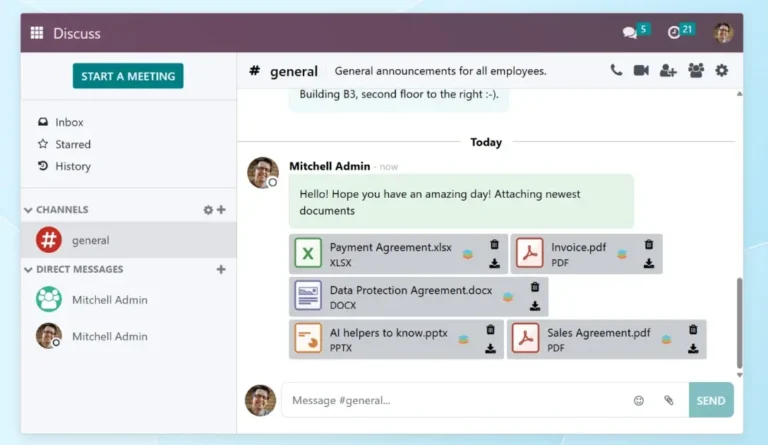
Odoo is the ideal open-source enterprise software for teams and businesses that value flexibility, data privacy,…
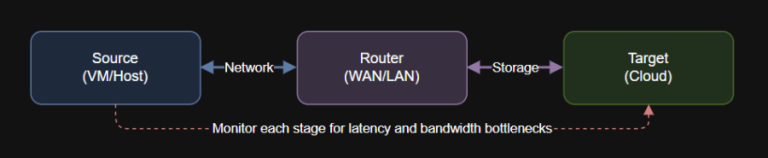
Introduction Data movement in cloud and hybrid architectures is only as fast as your slowest link….
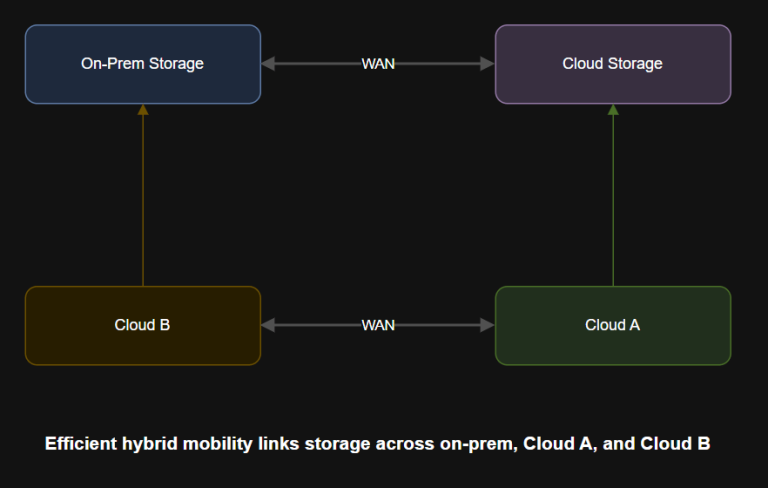
Introduction A media company needs to replicate video assets from on-prem storage to both Azure and…