CrowdStrike 2025 APJ eCrime Landscape Report: A New Era of Threats Emerges
The eCrime threat landscape in the Asia Pacific and Japan (APJ) region is quickly evolving, driven…
The eCrime threat landscape in the Asia Pacific and Japan (APJ) region is quickly evolving, driven…
ExPRT.AI is trained to rank vulnerabilities based on how likely they are to be exploited in…
An attacker can exploit this vulnerability by crafting a Git repository including a malicious .gitmodules file…
Adversaries move fast, and so must defenders. CrowdStrike is raising the bar for ChromeOS security with…
Unsupported operating systems have historically become adversary targets. The longer a system remains unsupported, the more…

Unauthorized use of RMM tools has become especially dangerous: Throughout 2024, eCrime actors frequently used RMM…
Windows 10 End of Support Is Here There is evidence of active exploitation in the wild…
We believe our placement as a Visionary, coupled with our groundbreaking AI innovations and the acquisition…
In our previous articles, we’ve covered MySQL interview questions for beginners and intermediate users, and the…
Linux is an open-source operating system whose use is increasing these days as a result of…

SSH (Secure Shell) is one of the most important tools for Linux system administrators and developers,…

These new innovations are the essential pillars that define the agentic security platform. We are living…
Charlotte AI is powered by a fully managed multi-agent architecture that orchestrates specialized agents across a…
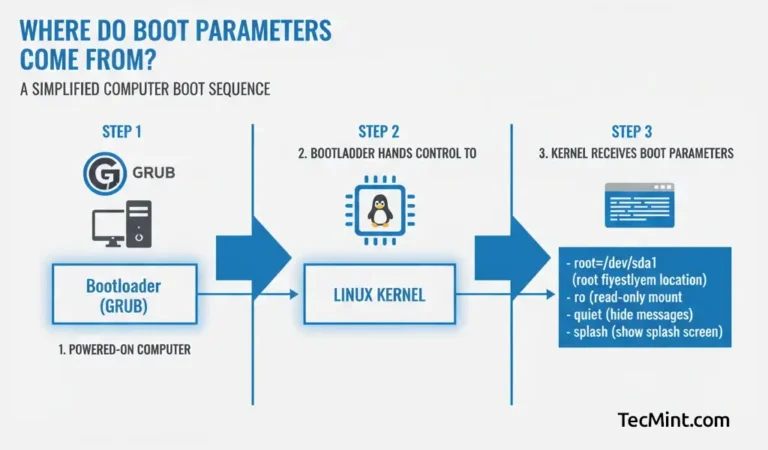
Linux booting is a complex process compared to other operating systems. The Linux Kernel accepts many…
The Falcon Next-Gen SIEM Correlation Rule Template Discovery dashboard provides customers with a streamlined way to…