AI Tool Poisoning: How Hidden Instructions Threaten AI Agents
Types of AI Tool Poisoning Attacks Consider a scenario where an attacker publishes a tool with…
Types of AI Tool Poisoning Attacks Consider a scenario where an attacker publishes a tool with…
SGNL provides the runtime access enforcement layer that sits between modern identity providers and the SaaS…
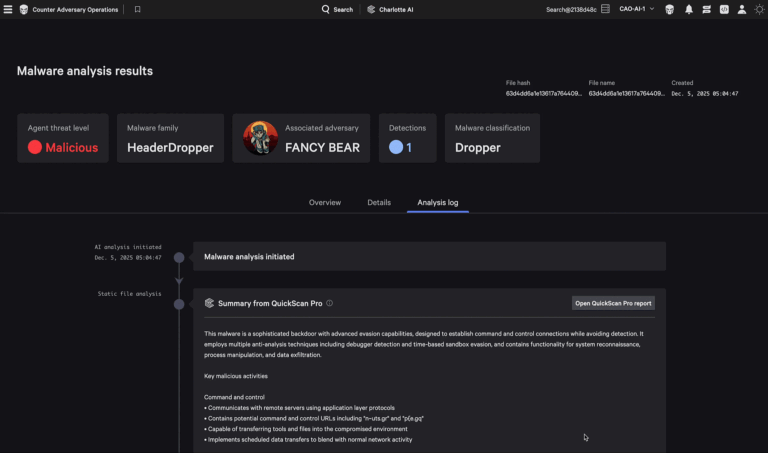
Under the Hood: How It Works Step 3: Dynamic behavioral analysis Step 5: Similar sample identification…
Rather than manually annotating thousands of queries (an expensive and time-consuming process), we leveraged NVIDIA NeMo…
These content packs span multiple categories including application resilience, file discovery, Linux device control, and asset…
In this article, we will go through the various steps to install the constituent packages in…
With the cluster infrastructure in place through the Vertex Training Cluster, we configured Slurm, the industry-standard…
Pillar #1: A Rich Corpus of Human-refined Data In cybersecurity, AI agents don’t operate in a…
The AI era is here — and it’s redefining cybersecurity. Organizations around the globe are adopting…
Organizations are under pressure to protect more devices, users, and distributed workloads than ever — while…
Traditional security tools were never built to protect AI assets across domains or the new AI…
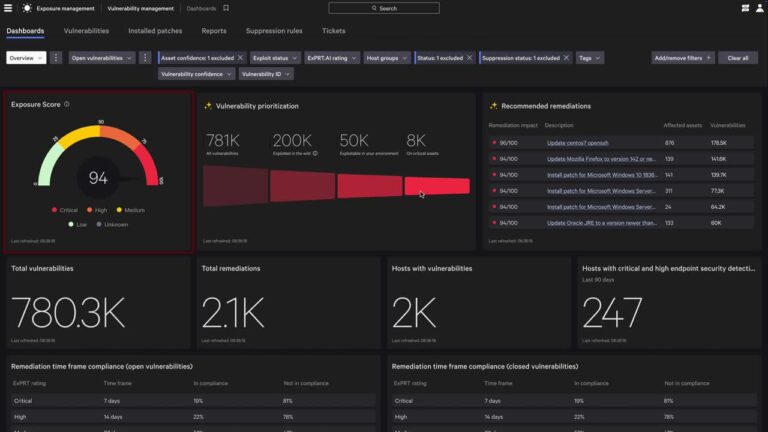
It’s fully embedded in the Falcon platform, so there’s no need to deploy a separate AI…
Consider document processing scenarios: An employee asks an AI to summarize a quarterly report, not realizing…

In the MUSTANG PANDA scenario, the adversary embedded encoded shellcode within their malware in an attempt…
Zero-Day Vulnerability in Windows Cloud Files Mini Filter Driver The CrowdStrike Falcon platform regularly collects and…