Inside the Human-AI Feedback Loop Powering CrowdStrike’s Agentic Security
The Human-AI Feedback Loop in Action Expert-Annotated Data Enables Analyst Grade AI 2 Time savings represents…
The Human-AI Feedback Loop in Action Expert-Annotated Data Enables Analyst Grade AI 2 Time savings represents…

– System Engineer, IT Services “Overall, it’s been a valuable and eye-opening experience. The tool has helped…
Indirect prompt injection significantly amplifies this risk by allowing adversaries to influence OpenClaw’s behavior through data…
As part of Falcon Cloud Security’s unified cloud-native application protection platform (CNAPP), Falcon ASPM helps organizations…

SE Labs employed both direct attacks and deep attacks. Test results and the feedback of third-party…
As AI adoption accelerated, WEX® — a global commerce platform that supports business operations primarily for…
As an example, consider a legitimate send_email tool that’s been thoroughly reviewed. An attacker publishes a…
In this guide, we feature some of the best Linux distributions that you can install on…
Christoph Bausewein is Assistant General Counsel for Data Protection and Policy at CrowdStrike.This creates a new…
– System Security Manager, Services (non-Government) IndustryThe truest assessment of the Falcon platform comes from the…
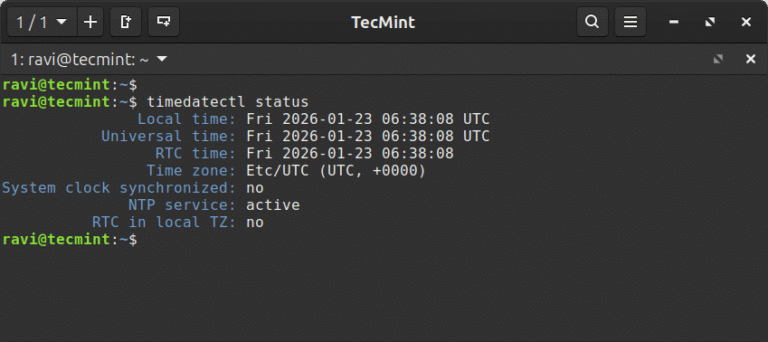
In this article, learn how to set time, timezone, and synchronize your Linux system clock with…

In this article, we show you how to encrypt files with GPG in Linux, generate key…
Precise device access: Security teams can allow, restrict, or block removable media based on device attributes,…
I’m delighted to announce CrowdStrike’s intent to acquire Seraphic, the leader in browser runtime security. With…
Actively Exploited Zero-Day Vulnerability in Windows Desktop Window Manager CVE-2026-20955 and CVE-2026-20957 are Critical remote code…