Why I Use LibreOffice and ONLYOFFICE Instead of MS Office
As someone who has been using Linux for more than 12 years, I’ve often come across…
As someone who has been using Linux for more than 12 years, I’ve often come across…
A Visionary Leader in MDR See what other industry analysts are saying about CrowdStrike on our…
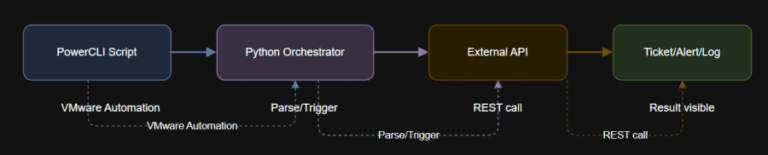
Learning Objectives $vmName = “<your-vm-name>”$outputFile = “C:Tempsnap_status.txt”if status == “FAILED”:url = “https://<your-jira-server>/rest/api/2/issue/”auth = (‘<jira-username>’, ‘<jira-api-token>’)headers =…
To solve this problem, the feature calculation code was updated to use the most recent version…
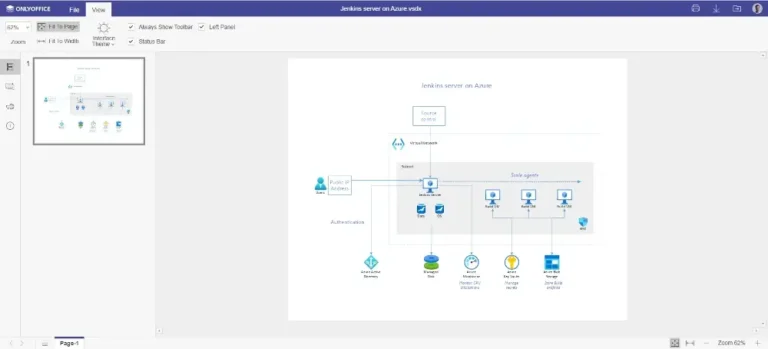
Since diagrams such as networks, organizational structures, system architectures, workflows, etc., have become an indispensable part…

Zip is a command-line utility tool used for compressing files and folders. Compression of files &…
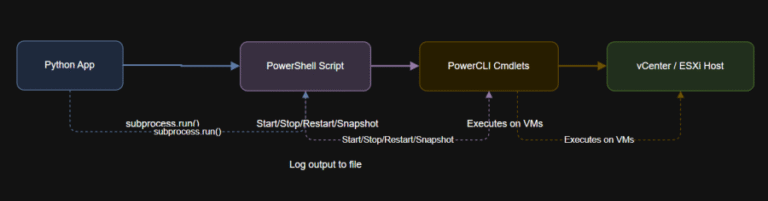
Learning Objectives # DisconnectDisconnect-VIServer -Server * -Confirm:$false Automate common VM lifecycle actions such as power on,…
Security teams today face a data crisis: Exploding volumes of security and IT telemetry are difficult…
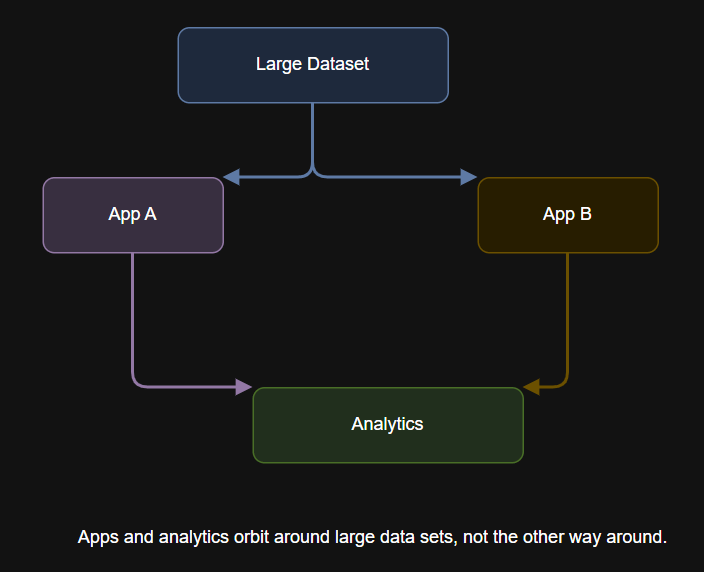
Table of Contents What Is Data Gravity? The History and Evolution of Data Gravity Why Data…
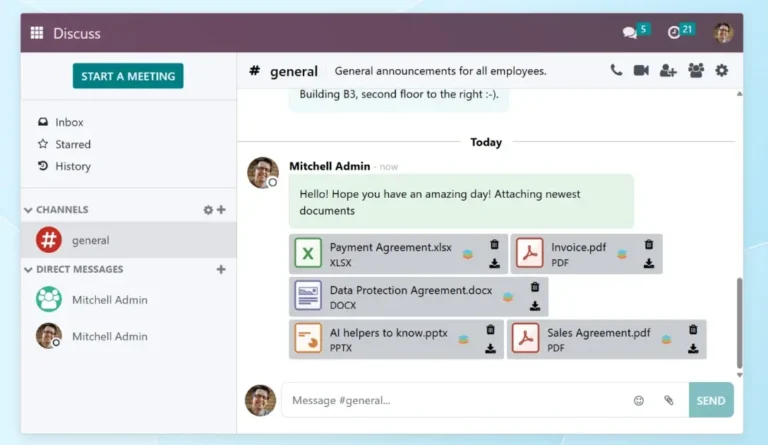
Odoo is the ideal open-source enterprise software for teams and businesses that value flexibility, data privacy,…
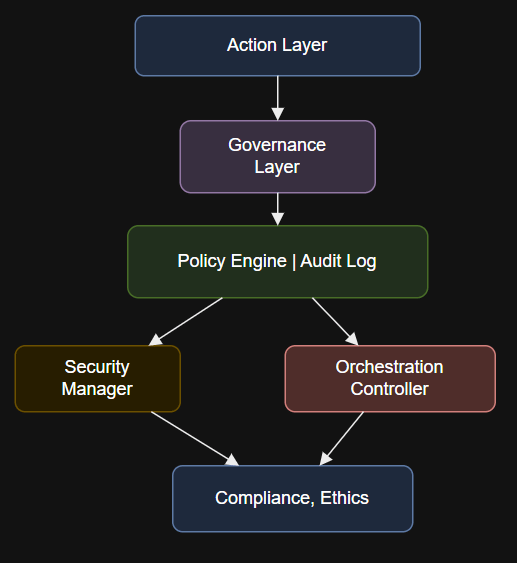
Introduction if __name__ == “__main__”:# Example: Validate if a user action is allowed by enterprise policyinput_payload…

TL;DR Inversion forces clarity: name how you’ll fail, then design your safeguards, signals, and contingencies. Copy…
Since late 2024, CrowdStrike Counter Adversary Operations has observed significant activity conducted by MURKY PANDA, a…
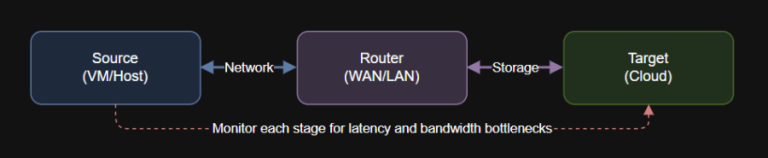
Introduction Data movement in cloud and hybrid architectures is only as fast as your slowest link….
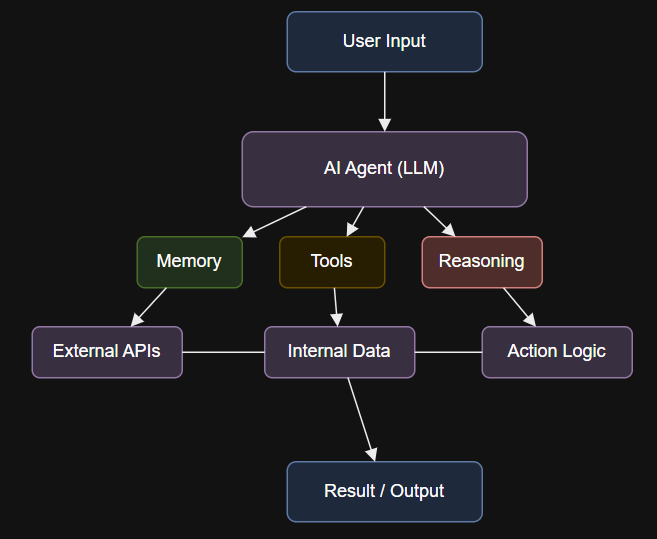
Introduction Run the agent, triggering the entire research and drafting process: What Sets AI Agents Apart?…