7 Best Udemy Android Development Courses in 2025
Android software development involves creating applications for devices running the Android operating system, primarily using Kotlin…

Android software development involves creating applications for devices running the Android operating system, primarily using Kotlin…

Every now and then, we check Udemy out for the most rated courses in different niches…

Keeping files in sync across multiple machines is a common task for Linux users. You might…
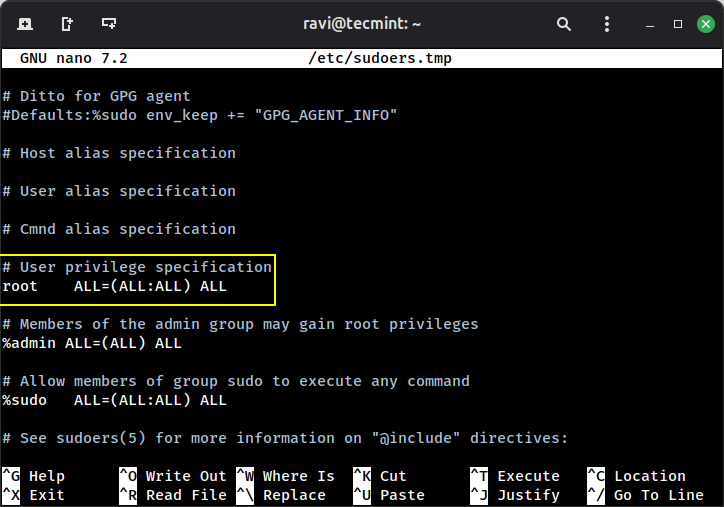
Linux is generally more secure than many other operating systems. A key part of this security…
If you’ve ever managed a hosting server, you know that cPanel & WHM is one of…

CrowdStrike is introducing real-time visibility and protection across browsers, local applications, shadow AI services, and cloud…
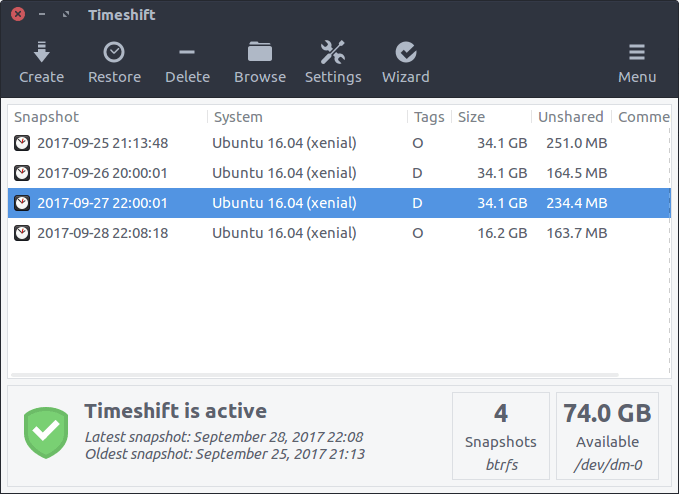
It isn’t easy to figure out which of the many Linux apps out there are actually…
With Pangea, CrowdStrike will extend this protection into the interaction layer of AI to secure how…

As a Linux user, you may eventually run into a situation where your root partition (/)…

Want to play Windows games on your Linux system but not sure where to begin? Heard…
Do you feel like your Ubuntu desktop turns messy the moment you open more than a…
Publicly Disclosed Zero-Day Vulnerability in Windows SMB CVE-2025-55226 is a Critical remote code execution vulnerability affecting…
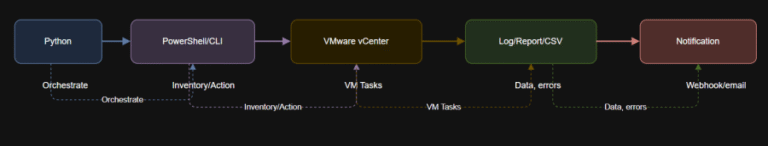
Learning Objectives VMware Repository on GitHub See how a single Python script can orchestrate inventory, lifecycle,…
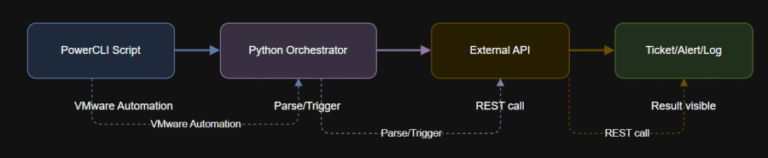
Learning Objectives $message = @{text = “VM $vmName has been powered off via automation.”} | ConvertTo-Json…
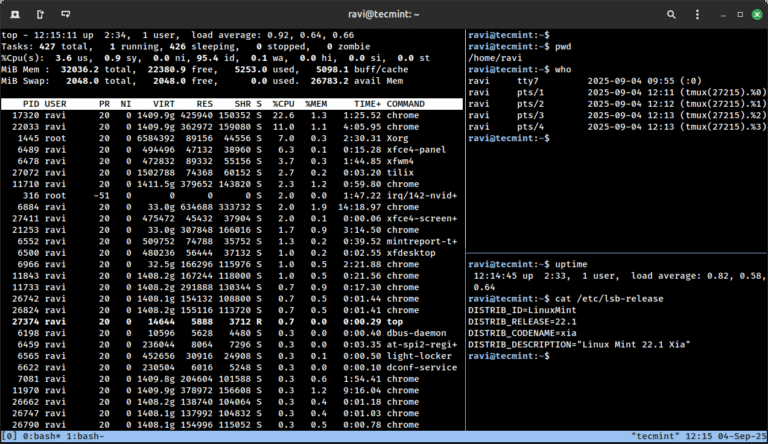
It is time once again to share a list of the best free and open-source software…