How to Install and Use PostgreSQL 18 on Ubuntu 24.04 LTS
PostgreSQL (Postgres in short) is an open source, powerful, advanced, high-performance, and stable relational-document database system,…
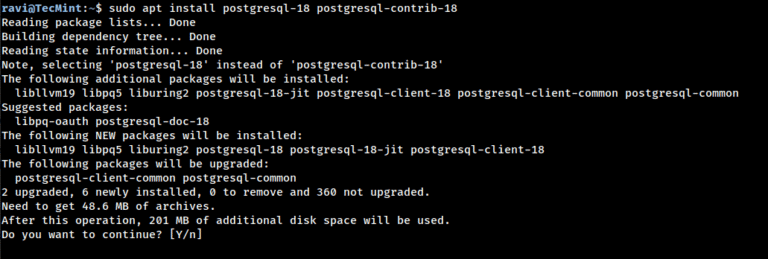
PostgreSQL (Postgres in short) is an open source, powerful, advanced, high-performance, and stable relational-document database system,…
Adversaries move fast, and so must defenders. CrowdStrike is raising the bar for ChromeOS security with…
Unsupported operating systems have historically become adversary targets. The longer a system remains unsupported, the more…

Unauthorized use of RMM tools has become especially dangerous: Throughout 2024, eCrime actors frequently used RMM…
Windows 10 End of Support Is Here There is evidence of active exploitation in the wild…
In Linux and other Unix-like operating systems, the init (initialization) process is the first process executed…
GNU Make is a development utility that determines which parts of a particular code base need…
In our previous articles, we’ve covered MySQL interview questions for beginners and intermediate users, and the…

After some investigation, via general log trawling and UI clicking, I found that on each host,…
Linux is an open-source operating system whose use is increasing these days as a result of…
The observed activity appears to begin with an HTTP POST request to /OA_HTML/SyncServlet, which initiates the…

SSH (Secure Shell) is one of the most important tools for Linux system administrators and developers,…
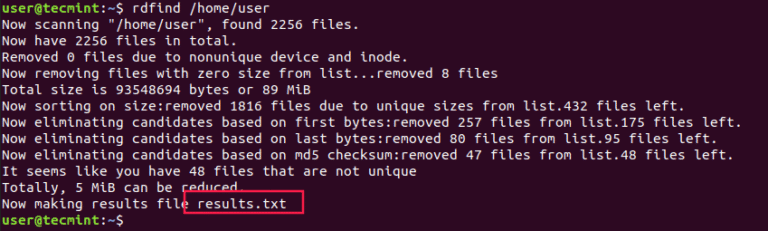
Organizing your home directory or even system can be particularly hard if you have the habit…
Charlotte AI is powered by a fully managed multi-agent architecture that orchestrates specialized agents across a…
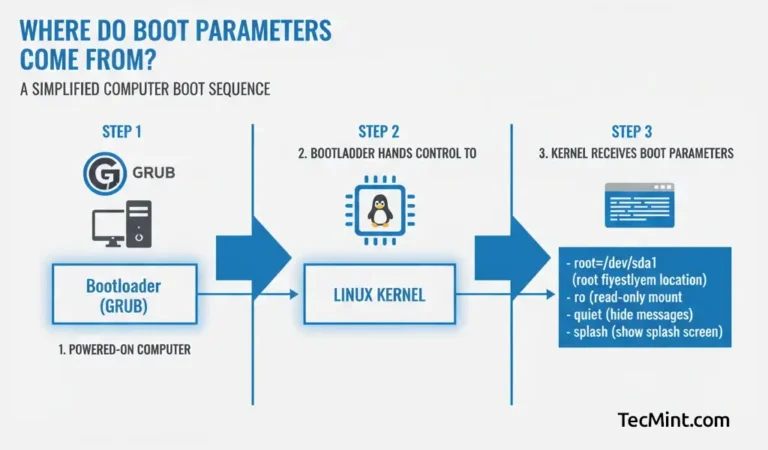
Linux booting is a complex process compared to other operating systems. The Linux Kernel accepts many…