10 MySQL Interview Questions Every DBA Must Know
In our previous articles, we’ve covered MySQL interview questions for beginners and intermediate users, and the…
In our previous articles, we’ve covered MySQL interview questions for beginners and intermediate users, and the…

After some investigation, via general log trawling and UI clicking, I found that on each host,…

SSH (Secure Shell) is one of the most important tools for Linux system administrators and developers,…
The Falcon Next-Gen SIEM Correlation Rule Template Discovery dashboard provides customers with a streamlined way to…
Strengths Recognized in the Frost Radar Read the full report: 2025 Frost Radar™: Cloud Workload Protection…

Google Cloud Platform is a suite of cloud computing services that shares its running environment with…

We are living in the midst of a revolution powered by computers and among the most…

Keeping files in sync across multiple machines is a common task for Linux users. You might…

CrowdStrike is introducing real-time visibility and protection across browsers, local applications, shadow AI services, and cloud…
The Falcon platform’s console unifies fragmented data, bridges silos, and translates complex queries into natural-language conversations….
With Pangea, CrowdStrike will extend this protection into the interaction layer of AI to secure how…
Publicly Disclosed Zero-Day Vulnerability in Windows SMB CVE-2025-55226 is a Critical remote code execution vulnerability affecting…
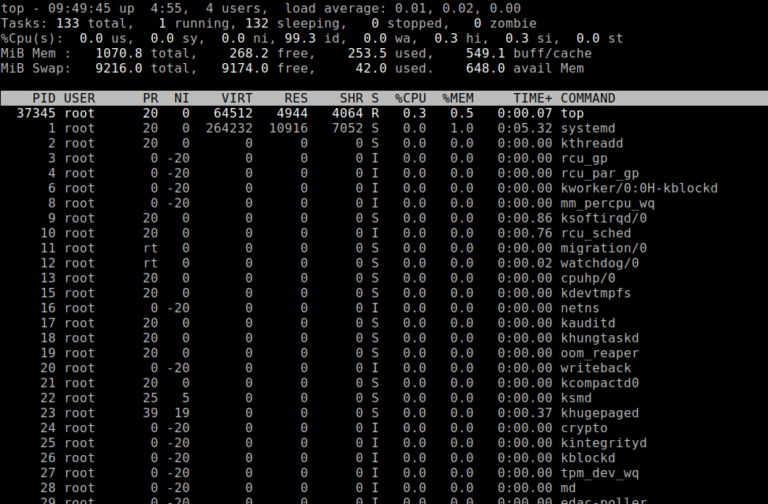
Being a System or Network administrator tasked with monitoring and debugging Linux system performance problems on…

DNS (Domain Name System) is a fundamental facilitator of several networking technologies such as mail servers,…
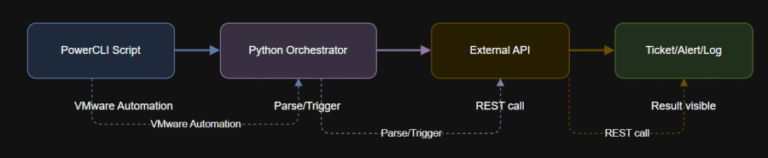
Learning Objectives $message = @{text = “VM $vmName has been powered off via automation.”} | ConvertTo-Json…