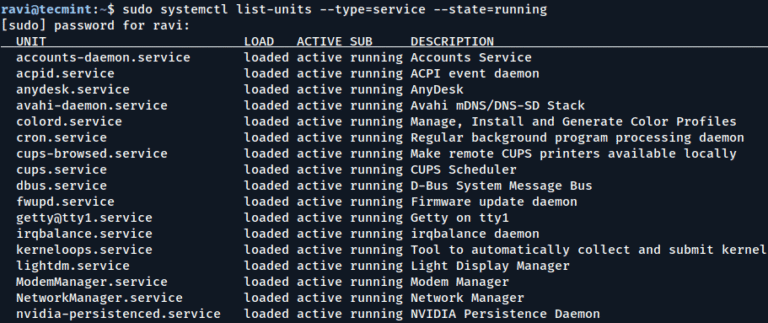
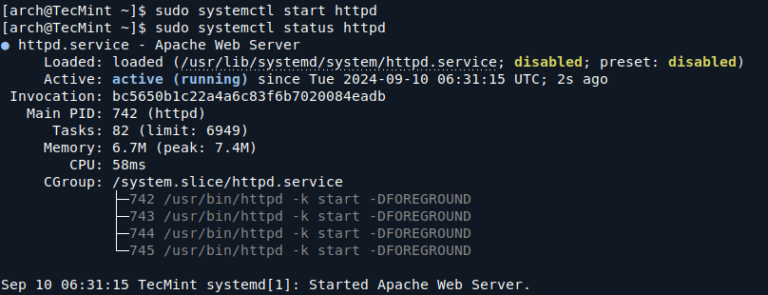
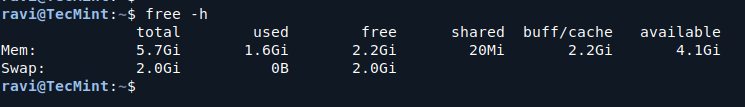
Container Escape Vectors
Let’s review some examples of container escape vectors.
The progression from initial container access to successful escape follows a systematic pattern that attackers have refined over time.
Privileged Container Abuse
Excessive Linux capabilities granted to containers can enable escape techniques. Below are a few examples:
Volume Mount Exploits
Containers share the host kernel, making kernel vulnerabilities particularly dangerous for container environments. One recent example would be CVE-2022-0847 (Dirty Pipe).
- /var/run/docker.sock: Complete Docker API access
- /: Host root filesystem access
- /proc: Host process information
- /sys: Host system configuration
Kernel Vulnerability Exploitation
Next we examine a complete attack kill-chain, demonstrating how a single misconfiguration — exposing a Docker API to the internet — can lead to the comprehensive compromise of an entire cloud environment. We’ll walk through each step of this attack progression, highlighting how one seemingly minor oversight can cascade into a full account takeover.
Capability Misconfigurations
Container escape allows attackers to break out of container isolation boundaries and access the underlying host system. These escape vectors typically exploit flaws in container configuration, application or library vulnerabilities, or kernel weaknesses.
- CAP_SYS_ADMIN: Allows mount operations and other privileged actions
- CAP_NET_ADMIN: Enables network configuration manipulation
- CAP_SYS_PTRACE: Permits process tracing and memory access
- CAP_SYS_MODULE: Allows loading kernel modules
From Initial Access to Breach
Initial Access Vectors in Container Environments
Adversaries employ multiple different techniques to gain initial access to containerized environments. The most prevalent attack vector involves Docker and Kubernetes API abuse (T1552 → T1610), where attackers exploit exposed API endpoints, weak authentication mechanisms, or misconfigured role-based access control (RBAC) settings. These misconfigurations often result from incomplete security hardening of container orchestration platforms. Other initial access vectors that have been observed include exploitation of vulnerable containerized application (T1190) and compromised image registry (T1204).
Detailed Attack Kill Chain: From Container Access to Escape
Improper volume mounts can create direct paths for container escape by exposing sensitive host directories or system sockets. Some of the most used critical mount points are:
Containers running in privileged mode effectively disable most security mechanisms, granting near-equivalent access to the host system. This configuration is particularly dangerous as it allows attackers the ability to load kernel modules, potentially mount sensitive host filesystems, and gain full access to host devices.