CrowdStrike Falcon Achieves 100% Protection and Accuracy in SE Labs Endpoint Protection Evaluation
Earlier this year, in testing against ransomware attacks, SE Labs employed realistic scenarios using tactics and…

Earlier this year, in testing against ransomware attacks, SE Labs employed realistic scenarios using tactics and…
Frost & Sullivan also praised how CrowdStrike both secures AI agents and leverages agentic AI for…
Coerced Authentication The initial reconnaissance and setup phase requires minimal resources but careful planning. The attack…
This isn’t just about saving time. It’s about enabling every stakeholder to see, understand, and act…
AI-enhanced social engineering poses particular challenges. Attackers use generative AI to craft contextually appropriate phishing emails…
The eCrime threat landscape in the Asia Pacific and Japan (APJ) region is quickly evolving, driven…
ExPRT.AI is trained to rank vulnerabilities based on how likely they are to be exploited in…
An attacker can exploit this vulnerability by crafting a Git repository including a malicious .gitmodules file…
PostgreSQL (Postgres in short) is an open source, powerful, advanced, high-performance, and stable relational-document database system,…
Adversaries move fast, and so must defenders. CrowdStrike is raising the bar for ChromeOS security with…
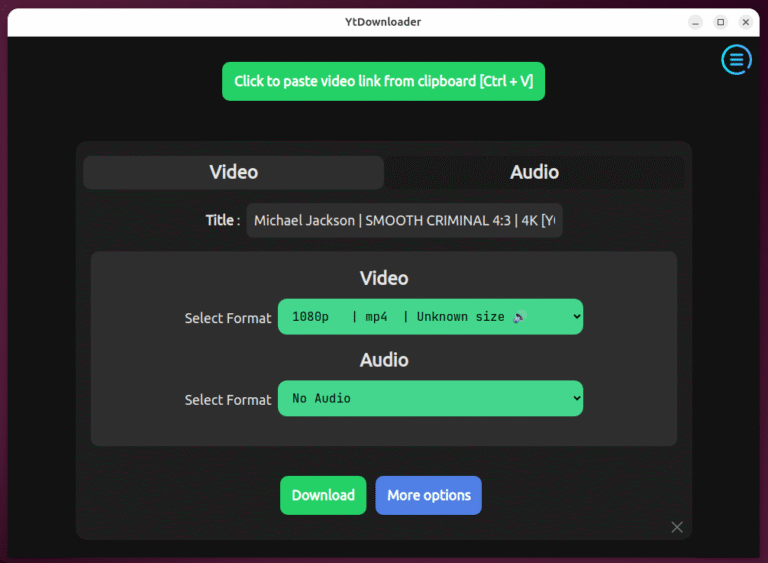
Earlier, I wrote about yt-dlp, the powerful command-line tool for downloading videos from hundreds of websites,…
Unsupported operating systems have historically become adversary targets. The longer a system remains unsupported, the more…
Windows 10 End of Support Is Here There is evidence of active exploitation in the wild…

Unauthorized use of RMM tools has become especially dangerous: Throughout 2024, eCrime actors frequently used RMM…
In Linux and other Unix-like operating systems, the init (initialization) process is the first process executed…