How to Enable AI Agents in ONLYOFFICE Desktop Editors on Linux
Learn how to enable and configure AI agents in ONLYOFFICE Desktop Editors to automate document editing,…
Learn how to enable and configure AI agents in ONLYOFFICE Desktop Editors to automate document editing,…
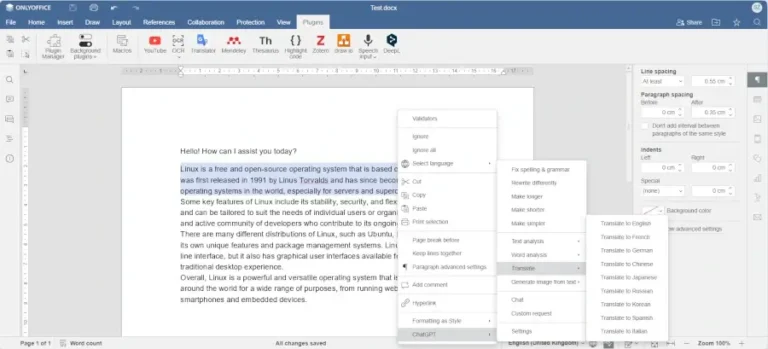
In this article, you will discover the best software tools powered by AI that you can…
As AI adoption accelerated, WEX® — a global commerce platform that supports business operations primarily for…
As an example, consider a legitimate send_email tool that’s been thoroughly reviewed. An attacker publishes a…
GOLDEN CHOLLIMA Shared infrastructure elements and tool cross-pollination indicate these units maintain close coordination. All three…
In this guide, we feature some of the best Linux distributions that you can install on…
– System Security Manager, Services (non-Government) IndustryThe truest assessment of the Falcon platform comes from the…
Christoph Bausewein is Assistant General Counsel for Data Protection and Policy at CrowdStrike.This creates a new…
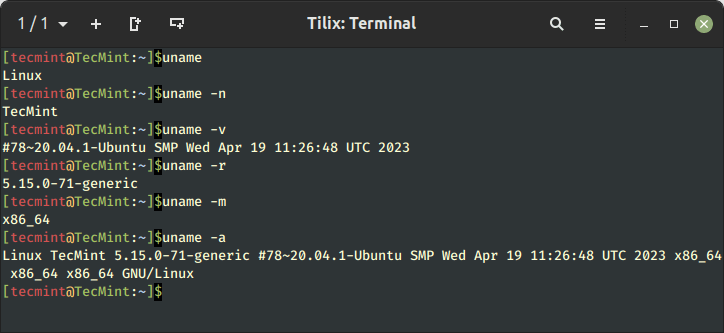
Learn 11 essential Linux commands to check hardware info including CPU, RAM, disk, USB, and PCI…
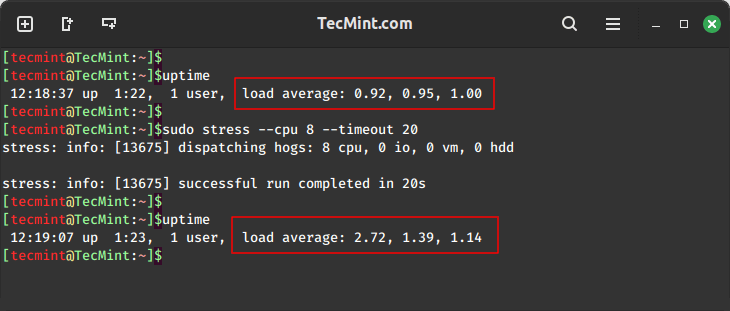
In this guide, we will explore two important tools, stress and stress-ng, for conducting comprehensive stress…
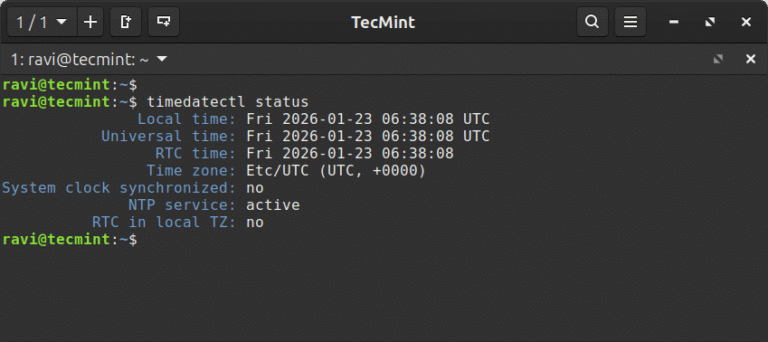
In this article, learn how to set time, timezone, and synchronize your Linux system clock with…

In this article, we show you how to encrypt files with GPG in Linux, generate key…
Precise device access: Security teams can allow, restrict, or block removable media based on device attributes,…
ARM (Advanced RISC Machine) is a RISC (Reduced Instruction Set Computing) instruction-set architecture developed by ARM…
Updated: This article has been refreshed to cover the latest ways to edit documents on Ubuntu…