Small Devices, Big Risk: USB Drives Threaten Enterprise Security
Precise device access: Security teams can allow, restrict, or block removable media based on device attributes,…
Precise device access: Security teams can allow, restrict, or block removable media based on device attributes,…
ARM (Advanced RISC Machine) is a RISC (Reduced Instruction Set Computing) instruction-set architecture developed by ARM…
Updated: This article has been refreshed to cover the latest ways to edit documents on Ubuntu…
Expert Agents: Native AI Reasoning Across the Falcon Platform Effective threat triage requires correlating evidence across…

As the name implies, the 5C model focuses around 5 key “C’s.” Each C represents a…
I’m delighted to announce CrowdStrike’s intent to acquire Seraphic, the leader in browser runtime security. With…
Actively Exploited Zero-Day Vulnerability in Windows Desktop Window Manager CVE-2026-20955 and CVE-2026-20957 are Critical remote code…

About Theresa Donahue Click here to learn more about Avalara. Avalara and Volusion work together to…
Types of AI Tool Poisoning Attacks Consider a scenario where an attacker publishes a tool with…
SGNL provides the runtime access enforcement layer that sits between modern identity providers and the SaaS…
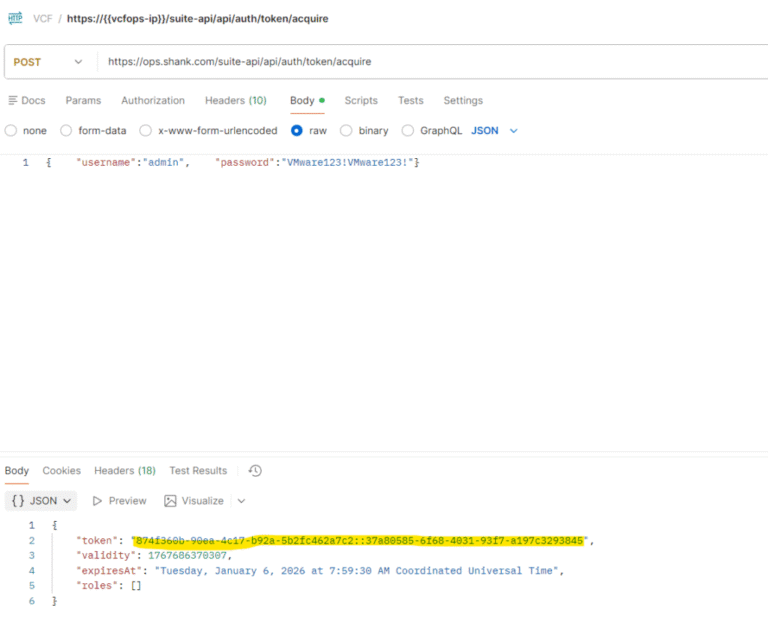
January 7, 2026 Authentication Failure: VCF SSO Broken vCenter vIDB Service Unavailable The Issue? It is…
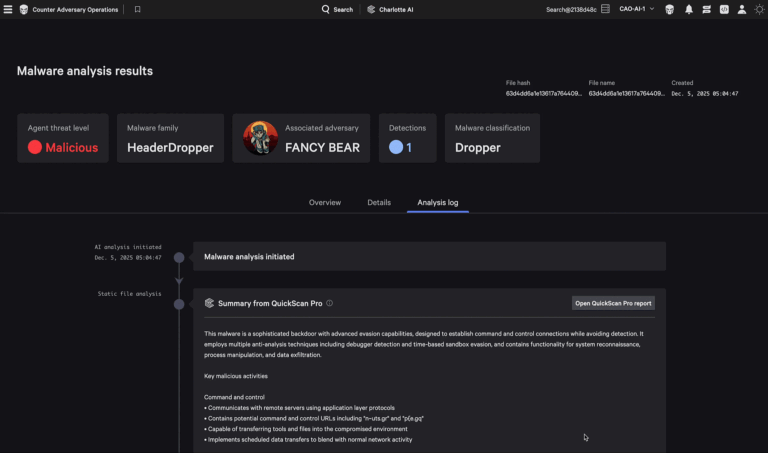
Under the Hood: How It Works Step 3: Dynamic behavioral analysis Step 5: Similar sample identification…
Rather than manually annotating thousands of queries (an expensive and time-consuming process), we leveraged NVIDIA NeMo…
These content packs span multiple categories including application resilience, file discovery, Linux device control, and asset…
In this article, we will go through the various steps to install the constituent packages in…