Inside CrowdStrike’s Science-Backed Approach to Building Expert SOC Agents
Pillar #1: A Rich Corpus of Human-refined Data In cybersecurity, AI agents don’t operate in a…
Pillar #1: A Rich Corpus of Human-refined Data In cybersecurity, AI agents don’t operate in a…
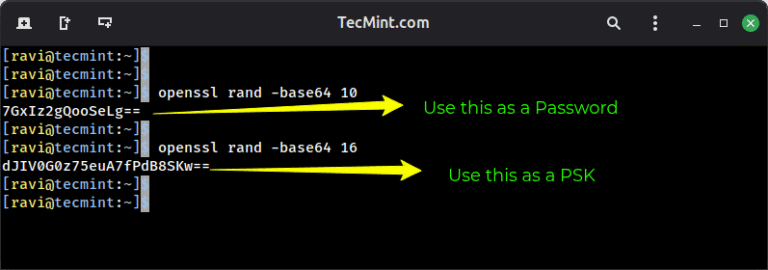
There are so many benefits of using a VPN (Virtual Private Network), some of which include…
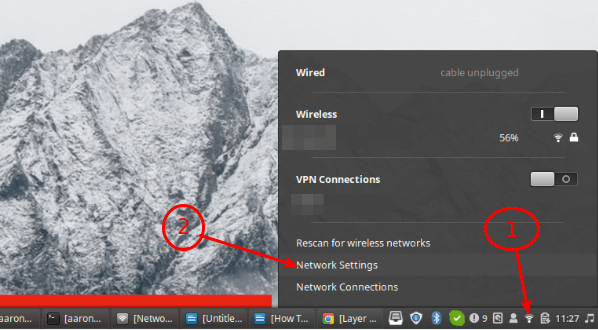
L2TP (which stands for Layer 2 Tunneling Protocol) is a tunneling protocol designed to support virtual…
Organizations are under pressure to protect more devices, users, and distributed workloads than ever — while…
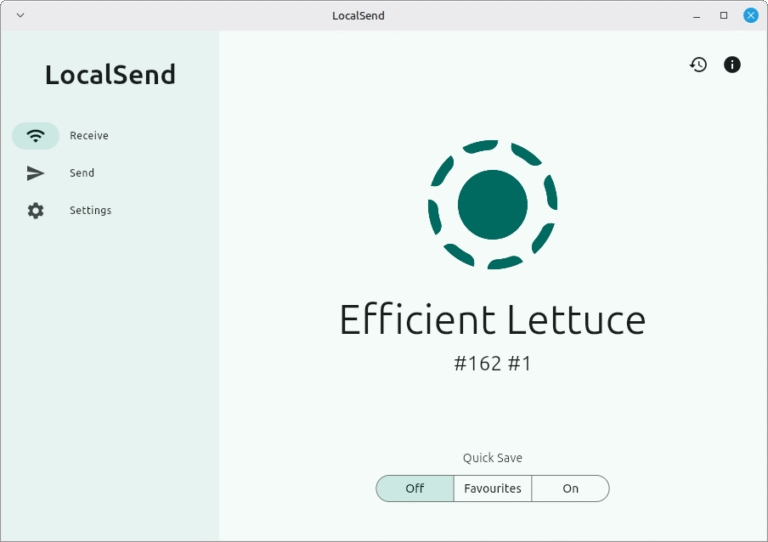
One of the most important uses of a network is for file sharing purposes, and there…
Traditional security tools were never built to protect AI assets across domains or the new AI…
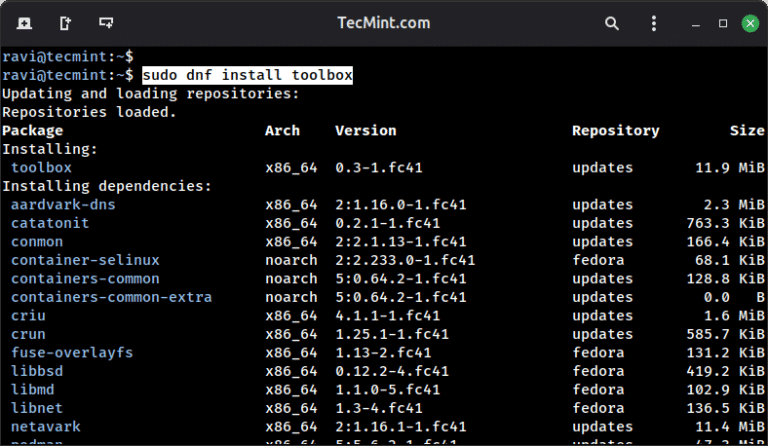
Modern Linux development has moved beyond the traditional approach of installing everything directly on your system….
If you’re looking to get started with Docker, understanding how to work with its command-line interface…
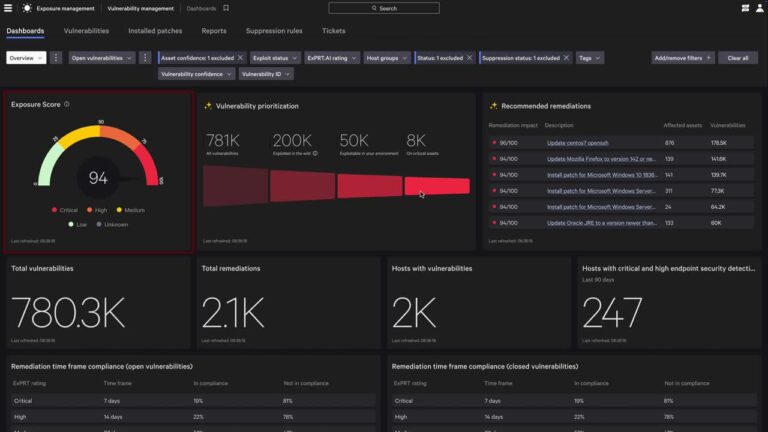
It’s fully embedded in the Falcon platform, so there’s no need to deploy a separate AI…
Consider document processing scenarios: An employee asks an AI to summarize a quarterly report, not realizing…

In the MUSTANG PANDA scenario, the adversary embedded encoded shellcode within their malware in an attempt…
Zero-Day Vulnerability in Windows Cloud Files Mini Filter Driver The CrowdStrike Falcon platform regularly collects and…
SSH or Secure Shell in simple terms is a way by which a person can remotely…
Why Modern Ecommerce Design Matters for 2026 As we move into 2026, modern ecommerce design is…
Identity has become a key battleground of modern cybersecurity. In 2024, 79% of CrowdStrike detections were…