CrowdStrike Boosts SOC Detection Content with Correlation Rule Template Discovery Dashboard
The Falcon Next-Gen SIEM Correlation Rule Template Discovery dashboard provides customers with a streamlined way to…
The Falcon Next-Gen SIEM Correlation Rule Template Discovery dashboard provides customers with a streamlined way to…
The fundamental shift we’re seeing is moving security professionals from operators to orchestrators. Today, we have…
Strengths Recognized in the Frost Radar Read the full report: 2025 Frost Radar™: Cloud Workload Protection…

Google Cloud Platform is a suite of cloud computing services that shares its running environment with…

Every now and then, we check Udemy out for the most rated courses in different niches…

Python is often considered to be one of the most powerful, adaptable, and easy-to-learn high-level programming…

We are living in the midst of a revolution powered by computers and among the most…

Keeping files in sync across multiple machines is a common task for Linux users. You might…
For off-the-shelf capabilities like Bedrock or Vertex AI, Falcon Cloud Security identifies the APIs and services…
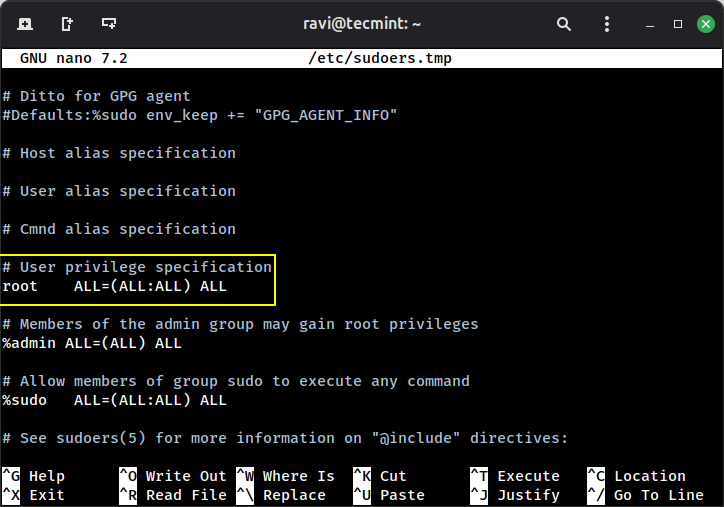
Linux is generally more secure than many other operating systems. A key part of this security…
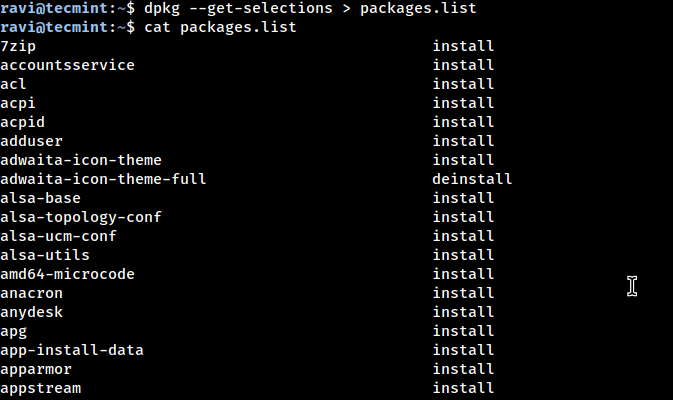
If you’ve ever reinstalled Ubuntu, you know the pain of setting everything up again, such as…
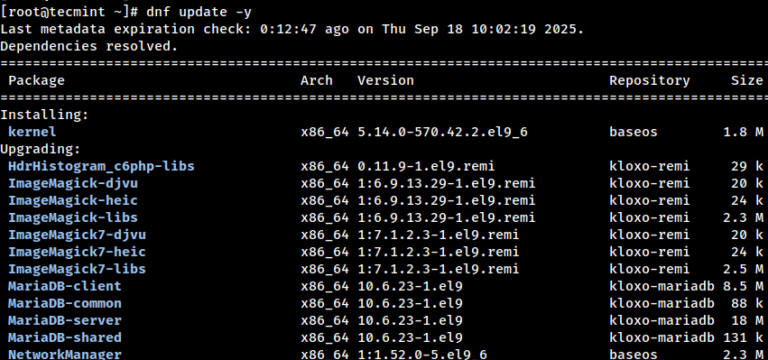
If you’ve ever managed a hosting server, you know that cPanel & WHM is one of…

CrowdStrike is introducing real-time visibility and protection across browsers, local applications, shadow AI services, and cloud…
Identity-driven case management is now generally available.CrowdStrike’s latest innovations deliver strong protections, great control, and fast…
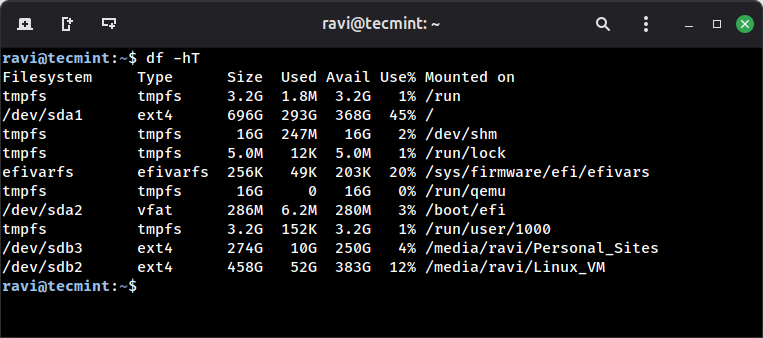
If you’ve ever run a Linux system in production or even just kept a personal server,…