How To Create an Effective Ecommerce Return Policy and Process
Conduct research on your competitors to see what types of terms they include in their return…

Conduct research on your competitors to see what types of terms they include in their return…

What are the best WordPress Security plugins and how to set them up the best way…

The Most Important Stages and Plugins for WordPress Website Development Developing a WordPress website requires careful…
Powerful SEO Tools for WordPress Search Engine Optimisation (SEO) is essential for improving your WordPress website’s…
“The comprehensive coverage of the SaaS ecosystem fueled by solid threat prevention, detection, and response capabilities…
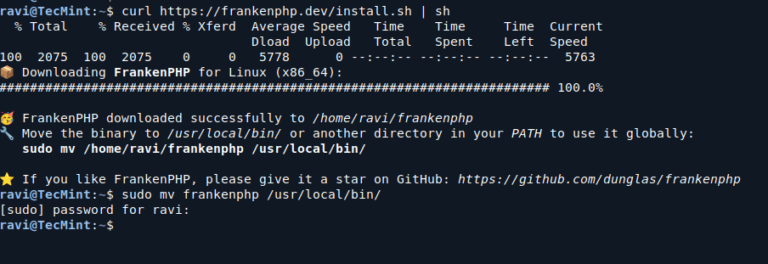
FrankenPHP is a modern application server for PHP that enhances the performance and capabilities of PHP…

Trust icons quickly communicate key value propositions and benefits in a visual way, allowing the user…

In the competitive landscape of e-commerce hosting, leveraging the right tools can be a game changer…
GOLDEN CHOLLIMA Shared infrastructure elements and tool cross-pollination indicate these units maintain close coordination. All three…
In this guide, we feature some of the best Linux distributions that you can install on…
Christoph Bausewein is Assistant General Counsel for Data Protection and Policy at CrowdStrike.This creates a new…
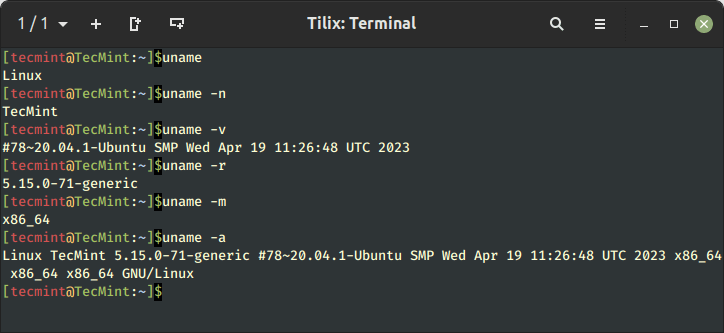
Learn 11 essential Linux commands to check hardware info including CPU, RAM, disk, USB, and PCI…
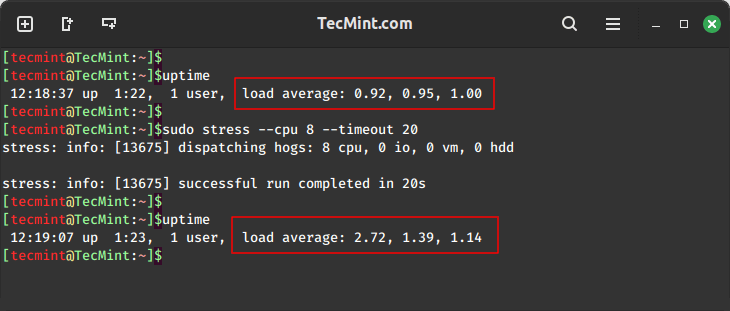
In this guide, we will explore two important tools, stress and stress-ng, for conducting comprehensive stress…
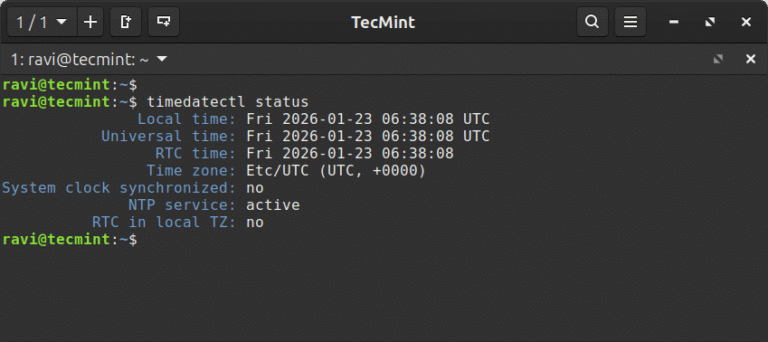
In this article, learn how to set time, timezone, and synchronize your Linux system clock with…

In this article, we show you how to encrypt files with GPG in Linux, generate key…
Precise device access: Security teams can allow, restrict, or block removable media based on device attributes,…
ARM (Advanced RISC Machine) is a RISC (Reduced Instruction Set Computing) instruction-set architecture developed by ARM…
Updated: This article has been refreshed to cover the latest ways to edit documents on Ubuntu…
Expert Agents: Native AI Reasoning Across the Falcon Platform Effective threat triage requires correlating evidence across…

As the name implies, the 5C model focuses around 5 key “C’s.” Each C represents a…
Actively Exploited Zero-Day Vulnerability in Windows Desktop Window Manager CVE-2026-20955 and CVE-2026-20957 are Critical remote code…
I’m delighted to announce CrowdStrike’s intent to acquire Seraphic, the leader in browser runtime security. With…

About Theresa Donahue Click here to learn more about Avalara. Avalara and Volusion work together to…