Falcon Identity Protection Innovations Stop Insider Risk, Secure Non-Human Identities, and Lock Down Privileged Access
Find and Fix Risky NHIs Before Adversaries Exploit Them Key Takeaway: Falcon Privileged Access delivers real-time,…

Find and Fix Risky NHIs Before Adversaries Exploit Them Key Takeaway: Falcon Privileged Access delivers real-time,…
Today, CrowdStrike and Microsoft announced a strategic alliance to bring clarity and coordination to the way…
With our unified platform approach, extensive threat intelligence, and proven track record of stopping breaches, CrowdStrike…
CrowdStrike has enhanced ExPRT.AI, our Expert Prediction Rating AI model, with XIoT-specific asset and adversary context…
“CrowdStrike Falcon is excellent at detecting anomalous activity where traditional antivirus is otherwise incapable of detecting…
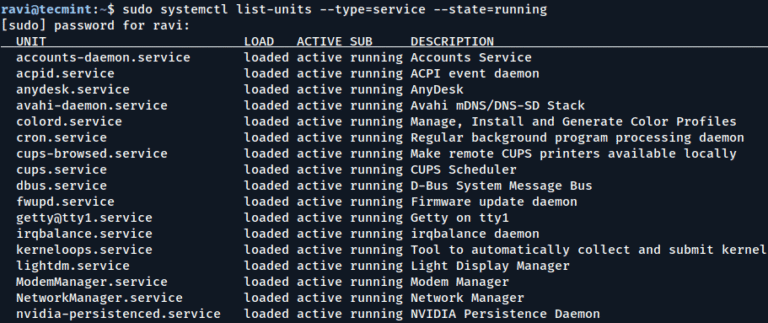
When you build a server according to your plan and requirements, you want it to run…

FTP stands for File Transfer Protocol and is one of the most widely used and standard…
Imagine you’re happily working on your Linux system, maybe compiling a package, running updates, or just…
Introduction Effective collaboration is essential when confronting today’s sophisticated cyber adversaries, particularly those operating with state…
Adversary-driven approach: GigaOm praised CrowdStrike’s adversary-centric approach to identity security: “Utilizing threat intelligence, it enriches alerts…
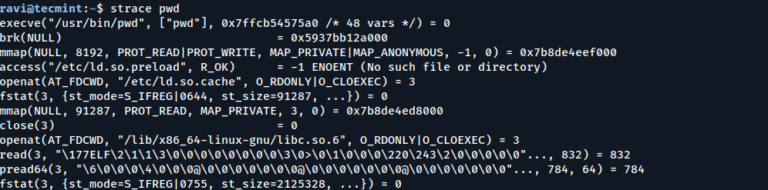
Welcome back to our ongoing journey through the world of powerful but often overlooked Linux commands….

Keylogging, short for “keystroke logging” is the process of recording the keys struck on a keyboard,…
The CrowdStrike 2025 Latin America Threat Landscape Report provides key insights into cyber activity across Central…
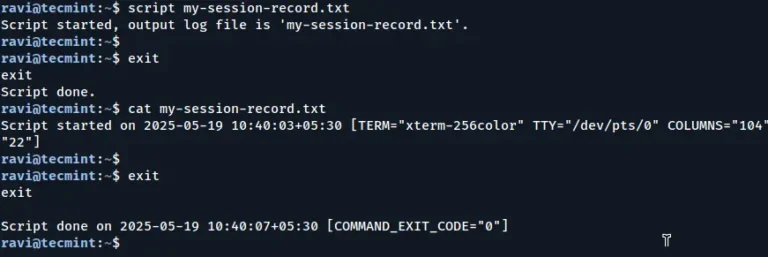
Welcome back to our Linux Interview Questions series on Tecmint! After laying a strong foundation in…

Midori is an open-source, lightweight, and fast web browser designed for people who want a simple…