VCF 9.0 GA Mental Model Part 6: Topology and Identity Boundaries for Single Site, Dual Site, and Multi-Region
TL;DR Scope: VMware Cloud Foundation 9.0.0.0 GA (primary platform build 24703748) and the associated 9.0 GA…
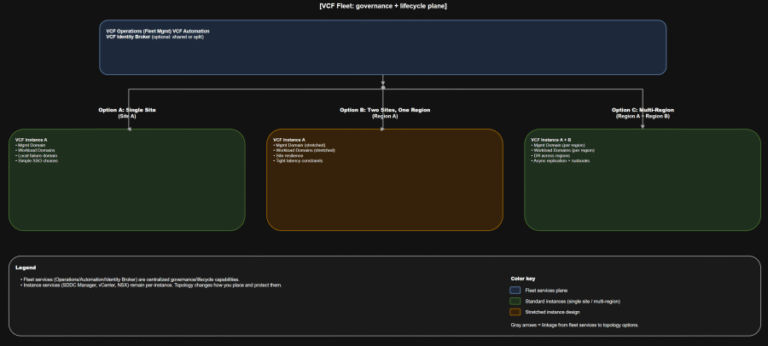
TL;DR Scope: VMware Cloud Foundation 9.0.0.0 GA (primary platform build 24703748) and the associated 9.0 GA…
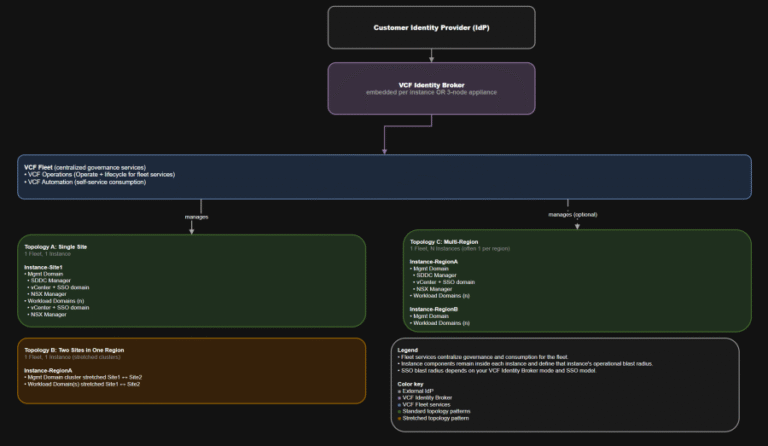
TL;DR This post targets VCF 9.0 GA only: VCF 9.0 (17 JUN 2025) build 24755599, with…
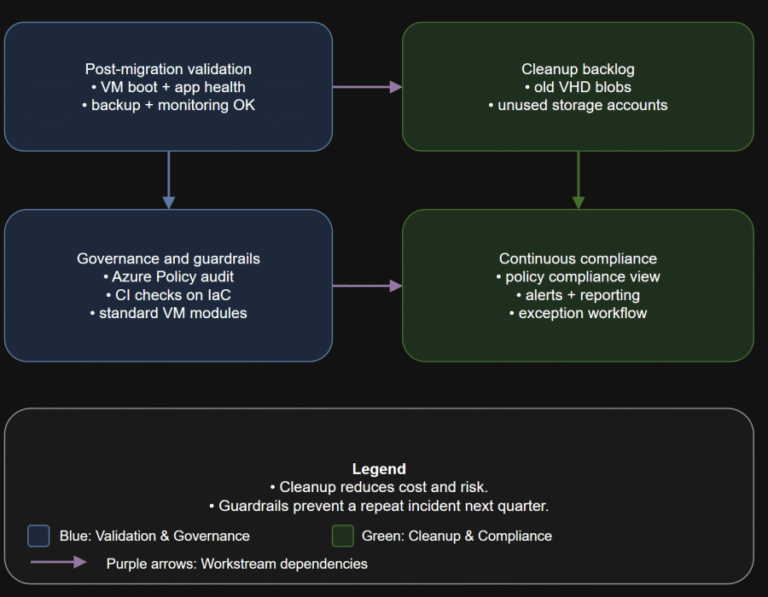
TL;DR Converting disks is not the finish line. Your real goal is a new steady state:…
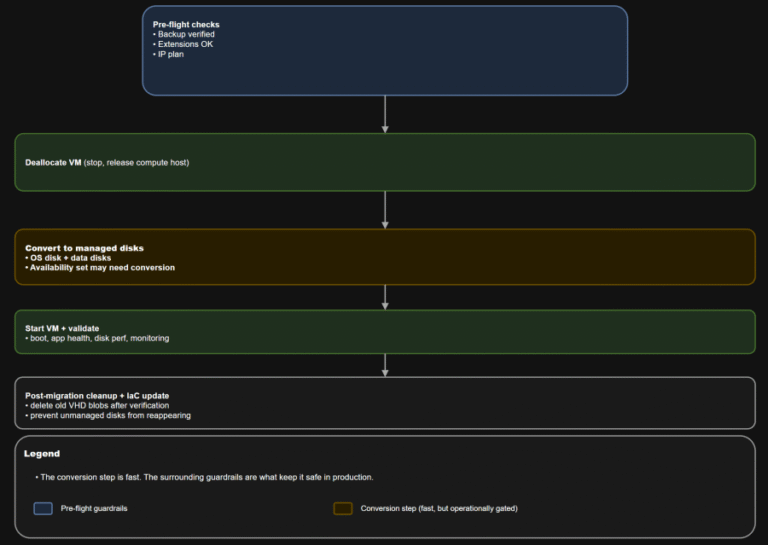
TL;DR Converting a VM to managed disks is usually operationally straightforward: deallocate, convert, start, validate. The…
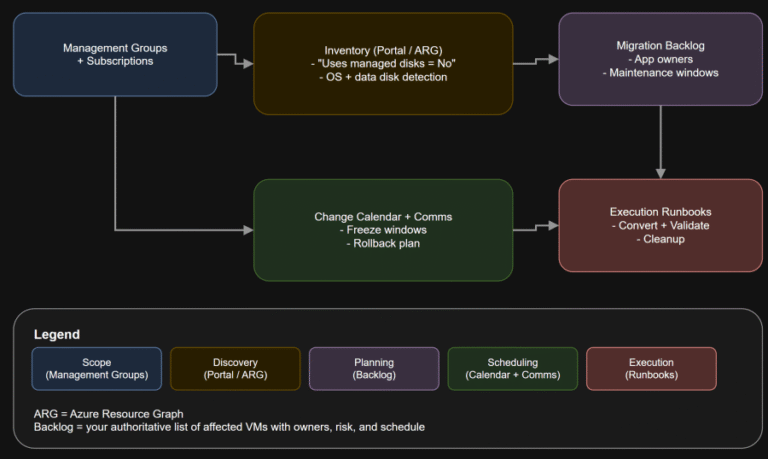
TL;DR If any Azure IaaS VM in your estate still uses unmanaged disks, it is on…
Insider threats pose a growing risk to organizations. Whether insiders take malicious actions, exhibit negligent behavior,…
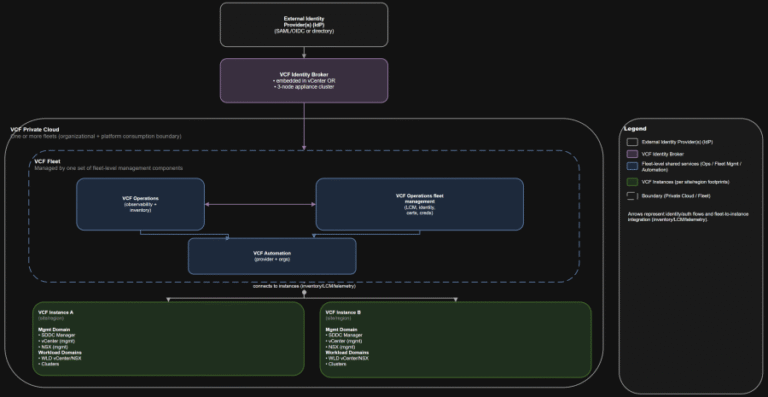
TL;DR Practical implication: if fleet services are impaired, governance and workflows degrade, but the instance-level control…
Actively Exploited Zero-Day Vulnerability in Windows Remote Desktop The vulnerability allows local attackers with no privileges…
In this guide, we feature some of the best Linux distributions that you can install on…
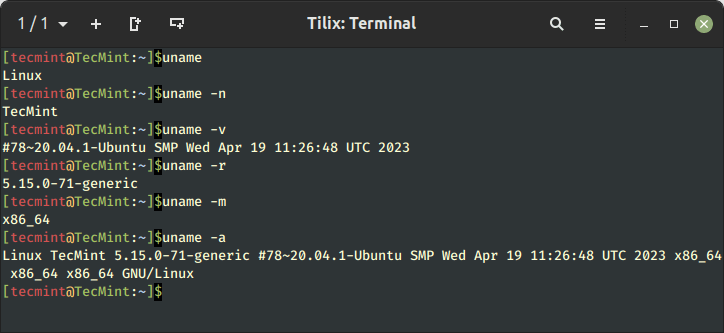
Learn 11 essential Linux commands to check hardware info including CPU, RAM, disk, USB, and PCI…
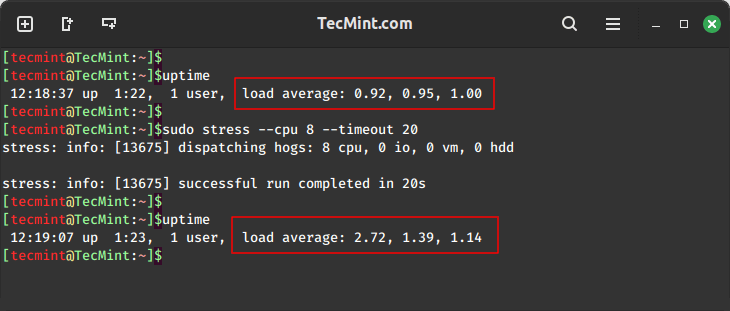
In this guide, we will explore two important tools, stress and stress-ng, for conducting comprehensive stress…
Precise device access: Security teams can allow, restrict, or block removable media based on device attributes,…
Consider document processing scenarios: An employee asks an AI to summarize a quarterly report, not realizing…

When most people think about operating systems, they picture Windows laptops or MacBooks, but here’s what’s…
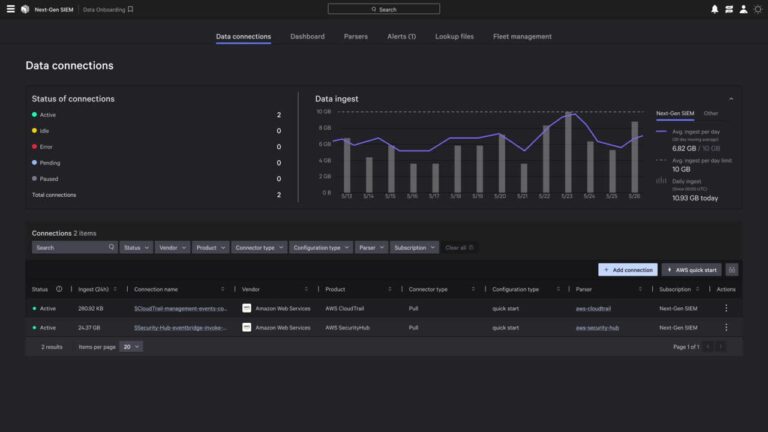
Perform on-demand queries for forensics, compliance, or audit use cases. CrowdStrike is the first cybersecurity partner…