50+ Best Free and Open-Source Software for Linux in 2025
It is time once again to share a list of the best free and open-source software…
It is time once again to share a list of the best free and open-source software…
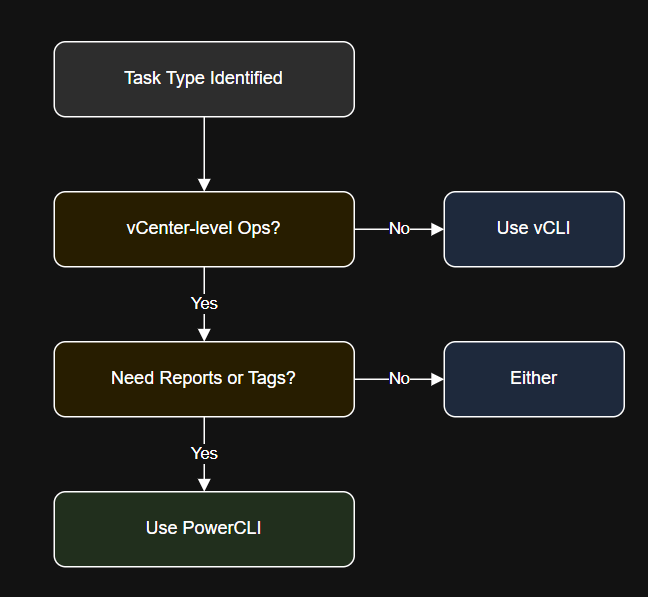
Introduction In this article, you’ll learn: Install using VMware downloads or use the VMA (vSphere Management…
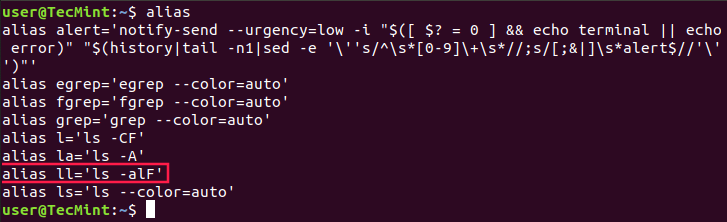
Linux users often need to use one command over and over again. Typing or copying the…
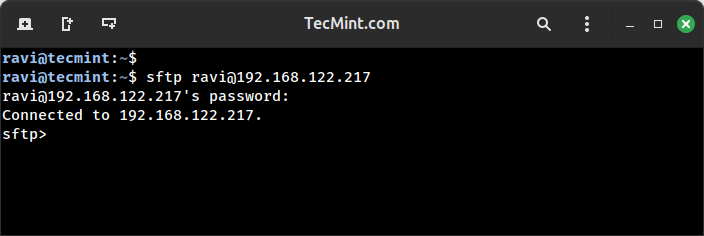
File Transfer Protocol (FTP) was once a widely used method for transferring files or data remotely….
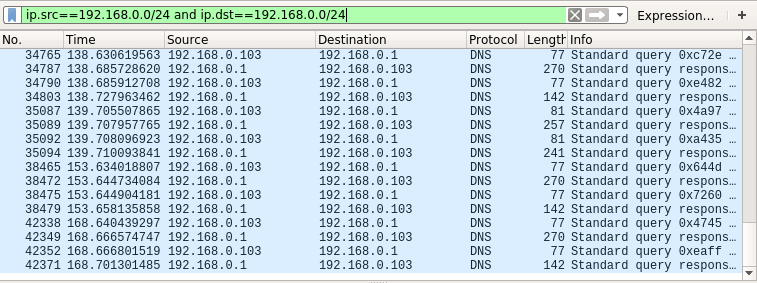
A system administrator’s routine tasks include configuring, maintaining, troubleshooting, and managing servers and networks within data…

If you’re managing multiple Ubuntu machines in a network, downloading updates and packages for each system…

Linux configuration files are often plain text, which makes them easily editable using command-line tools. Among…
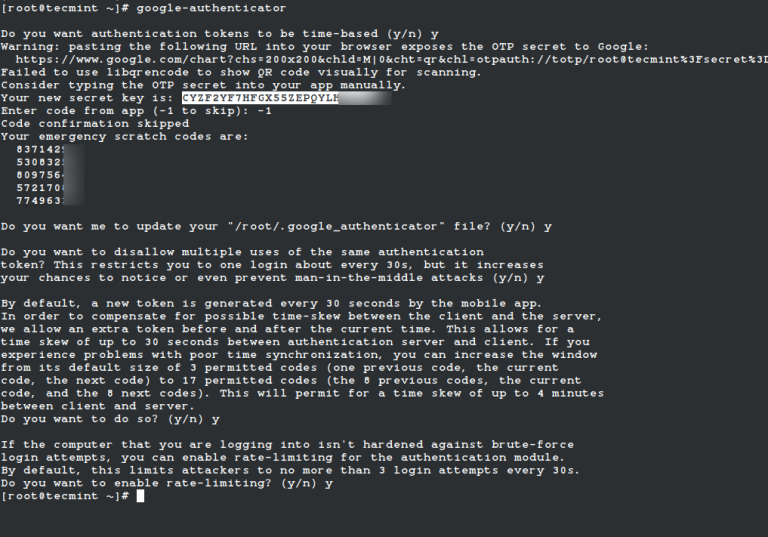
By default, SSH already uses secure data communication between remote machines, but if you want to…
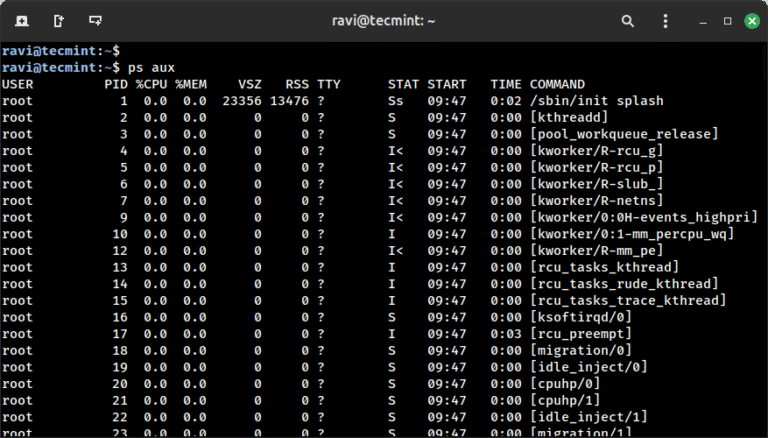
When starting out with Linux, you may encounter the terms “services” and “daemons” quite frequently, which…

After the success of our RHCSA / RHCE and LFCS / LFCE certification books, we are…

Introduction Workflow 2: Telemedicine Visit Table of Contents Executive Overview Healthcare Security Challenges Solution Architecture Overview…
SCATTERED SPIDER, an eCrime adversary, has recently broadened its target scope to include the aviation sector,…

Backups are like insurance; you don’t need them every day, but when disaster strikes, such as…

Today, I’m going to show you a simple but effective way to automatically block suspicious IPs…
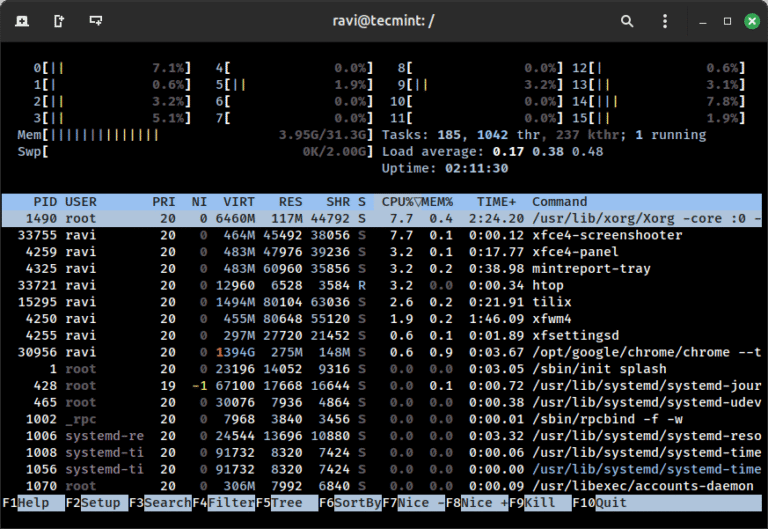
As a Linux SysAdmin working in a production environment, your daily routine is all about keeping…