The Dawn of the Agentic SOC: Reimagining Cybersecurity for the AI Era
The fundamental shift we’re seeing is moving security professionals from operators to orchestrators. Today, we have…
The fundamental shift we’re seeing is moving security professionals from operators to orchestrators. Today, we have…
Strengths Recognized in the Frost Radar Read the full report: 2025 Frost Radar™: Cloud Workload Protection…

Google Cloud Platform is a suite of cloud computing services that shares its running environment with…

Every now and then, we check Udemy out for the most rated courses in different niches…
For off-the-shelf capabilities like Bedrock or Vertex AI, Falcon Cloud Security identifies the APIs and services…
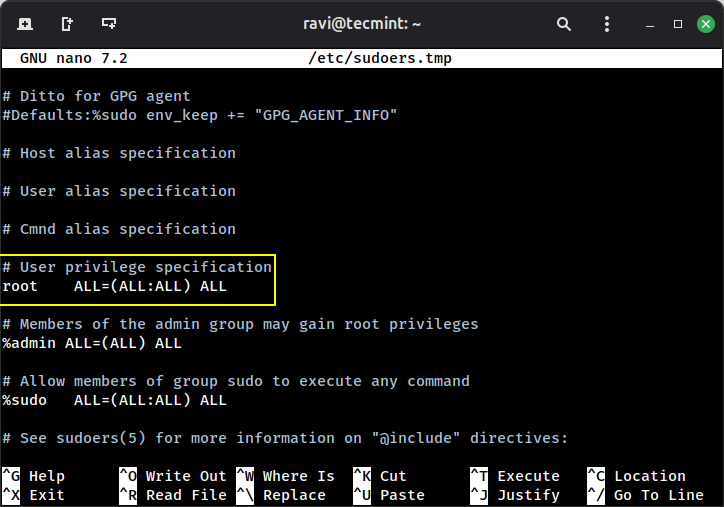
Linux is generally more secure than many other operating systems. A key part of this security…
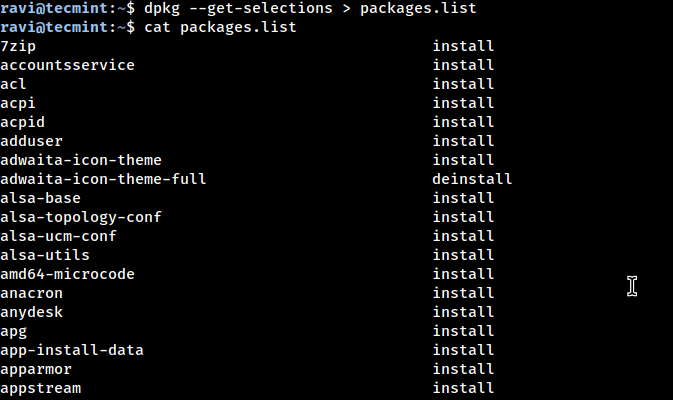
If you’ve ever reinstalled Ubuntu, you know the pain of setting everything up again, such as…
If you’ve ever managed a hosting server, you know that cPanel & WHM is one of…
Identity-driven case management is now generally available.CrowdStrike’s latest innovations deliver strong protections, great control, and fast…

CrowdStrike is introducing real-time visibility and protection across browsers, local applications, shadow AI services, and cloud…
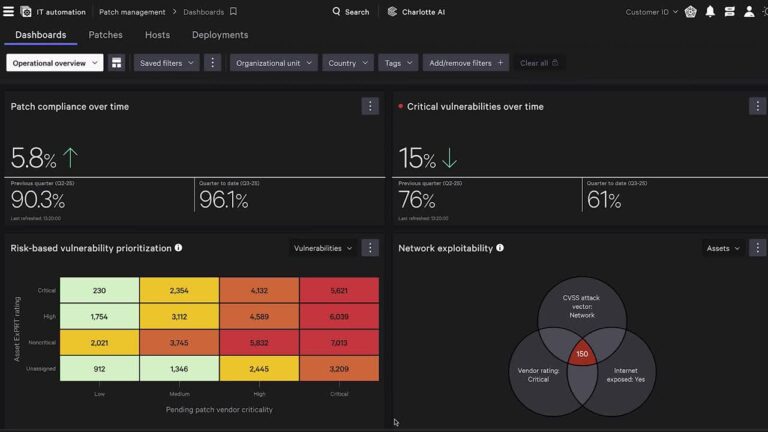
Traditional vulnerability management is broken. Security teams rely on one set of tools to find vulnerabilities;…

Many security teams struggle with threat hunting because they don’t know where to start or what…
As enterprises adopt AI agents and embed them into SaaS workflows, visibility and governance become essential….
The Falcon platform’s console unifies fragmented data, bridges silos, and translates complex queries into natural-language conversations….
Linux Mint 22.2 (“Zara”) is the latest point release in the Linux Mint 22 series, which…