How to Scale SOC Automation with Falcon Fusion SOAR
Whether you’re building your first automation workflow or exploring how AI can simplify everyday SOC tasks,…

Whether you’re building your first automation workflow or exploring how AI can simplify everyday SOC tasks,…
CrowdStrike uses NVIDIA Nemotron open models in CrowdStrike Falcon® Fusion SOAR and CrowdStrike Charlotte AI™ AgentWorks….
Unified classification: Apply consistent classifications for financial data, personally identifiable information (PII), protection health information (PHI),…
Despite the revolutionary agentic delivery mechanism used to achieve groundbreaking speed and scale in this attack,…
We believe our placement as a Visionary, coupled with our groundbreaking AI innovations and the acquisition…

CrowdStrike is introducing real-time visibility and protection across browsers, local applications, shadow AI services, and cloud…
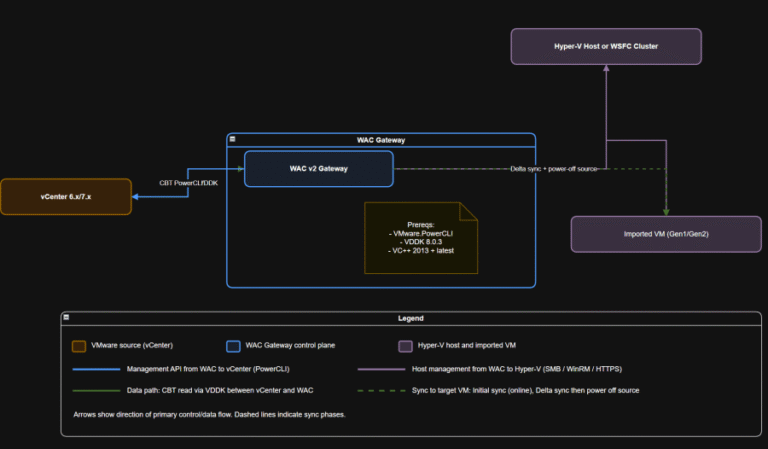
Compliance checkpoints (examples) Why this matters Bridge strategy: If you are standardizing on Windows Server and…
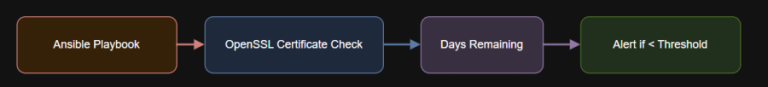
Introduction – name: Convert expiry date to epochset_fact:cert_expiry_date: “{{ cert_expiry_raw.stdout | trim }}”cert_expiry_epoch: “{{ cert_expiry_date |…
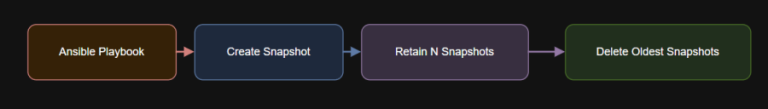
Introduction This playbook gives you complete control over Nutanix VM snapshots, ensuring consistency, compliance, and automation…
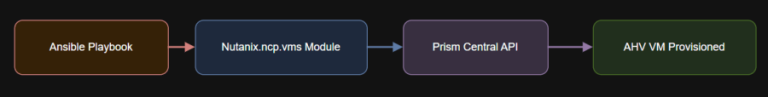
Introduction all:hosts:localhost:ansible_connection: local Step 2: Define Credentials File Once your Ansible control node is configured, deploying…
Stopping Modern Attacks with AI and Expertise The Frost Radar™ serves as essential research for organizations…