How to Setup Your Own IPsec/L2TP VPN Server in Linux
There are so many benefits of using a VPN (Virtual Private Network), some of which include…
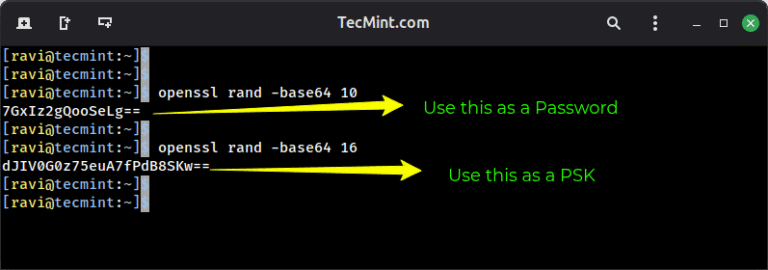
There are so many benefits of using a VPN (Virtual Private Network), some of which include…
Organizations are under pressure to protect more devices, users, and distributed workloads than ever — while…
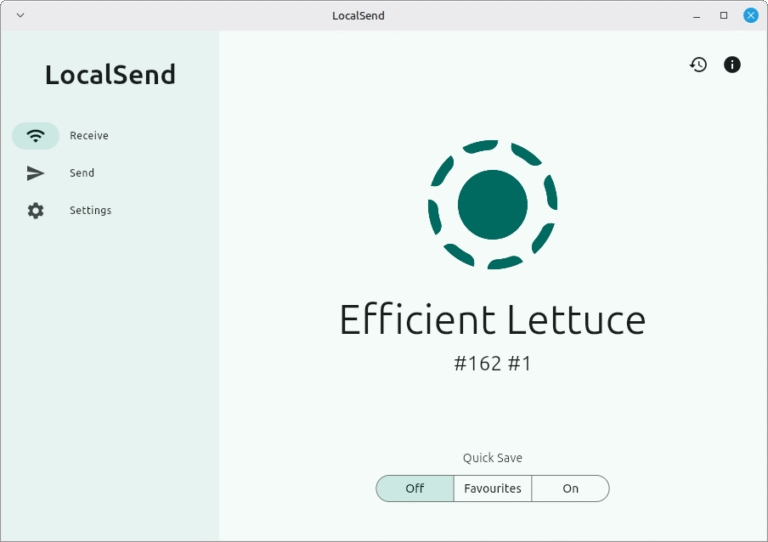
One of the most important uses of a network is for file sharing purposes, and there…
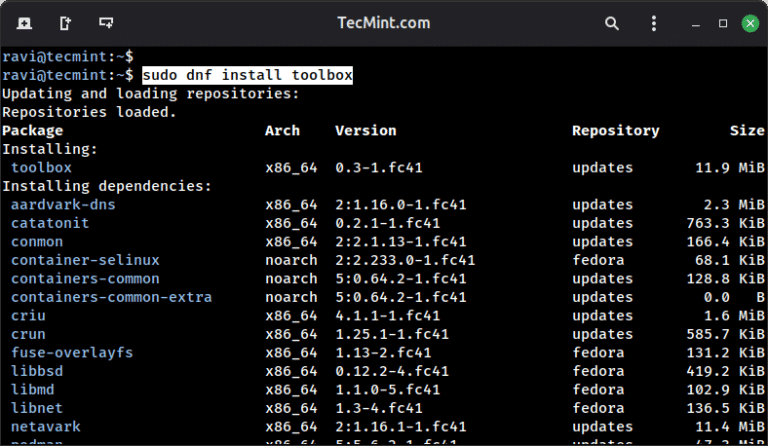
Modern Linux development has moved beyond the traditional approach of installing everything directly on your system….
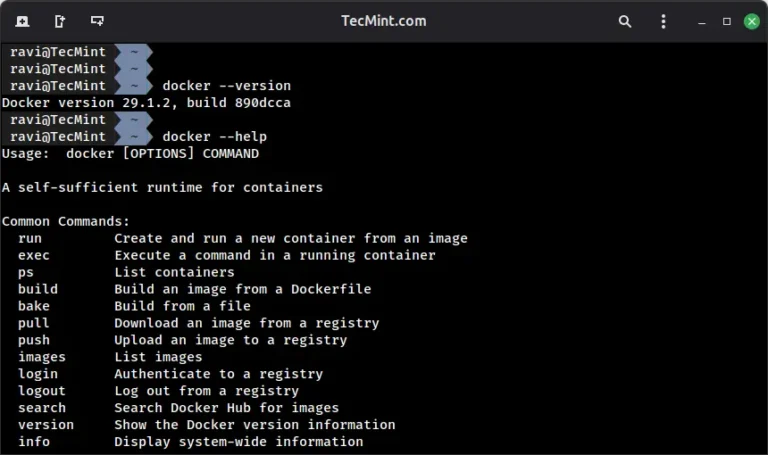
If you’re looking to get started with Docker, understanding how to work with its command-line interface…
Consider document processing scenarios: An employee asks an AI to summarize a quarterly report, not realizing…
Zero-Day Vulnerability in Windows Cloud Files Mini Filter Driver The CrowdStrike Falcon platform regularly collects and…
SSH or Secure Shell in simple terms is a way by which a person can remotely…
Identity has become a key battleground of modern cybersecurity. In 2024, 79% of CrowdStrike detections were…
There are two basic types of prompt injection attacks: Understanding Prompt Injection Employee BYO AI adoption…

When most people think about operating systems, they picture Windows laptops or MacBooks, but here’s what’s…

When someone visits your website, their browser and your server exchange information back and forth. Without…
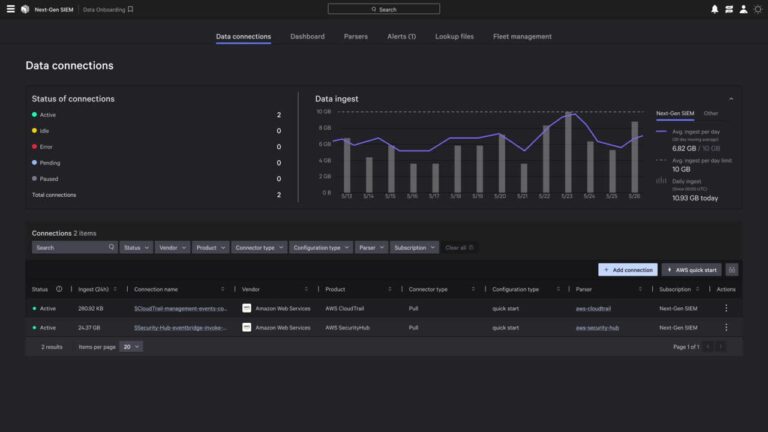
Perform on-demand queries for forensics, compliance, or audit use cases. CrowdStrike is the first cybersecurity partner…
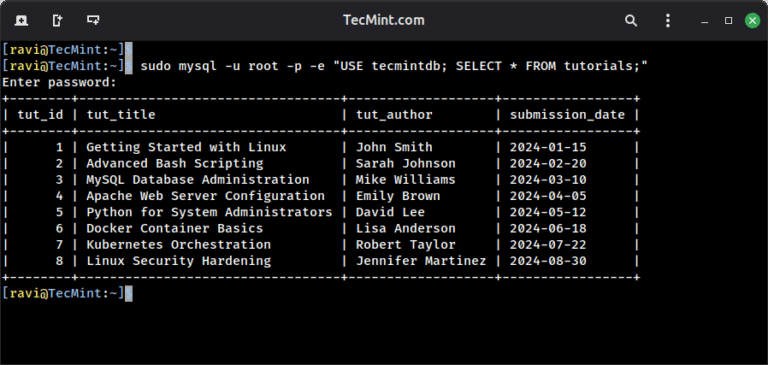
If you are in charge of managing a database server, from time to time you may…
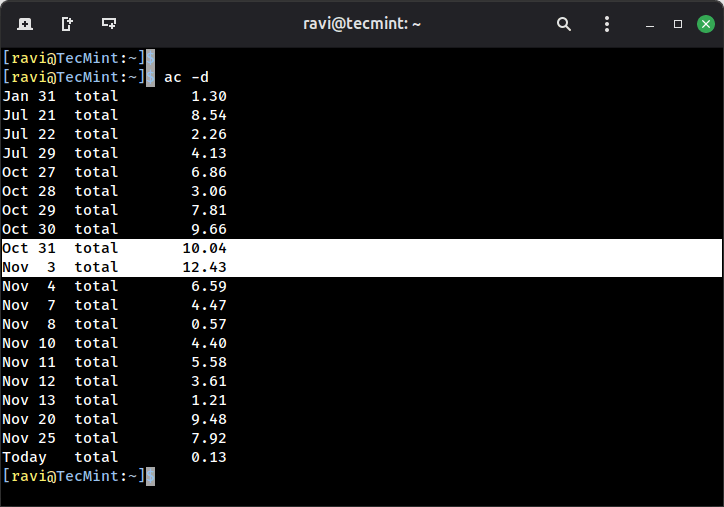
When you’re managing a Linux server, especially one with multiple users, you need visibility into what’s…