How to Verify Debian and Ubuntu Packages Using MD5 Checksums
Have you ever wondered why a given binary or package installed on your system does not…
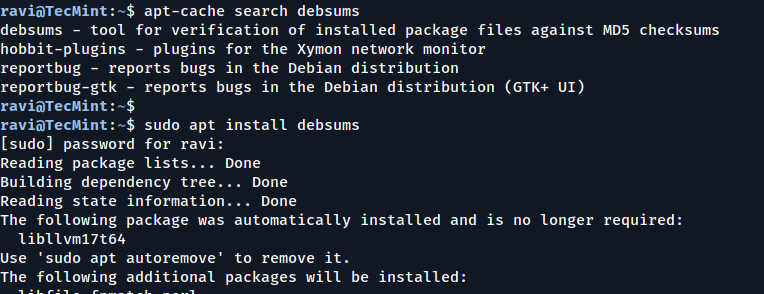
Have you ever wondered why a given binary or package installed on your system does not…
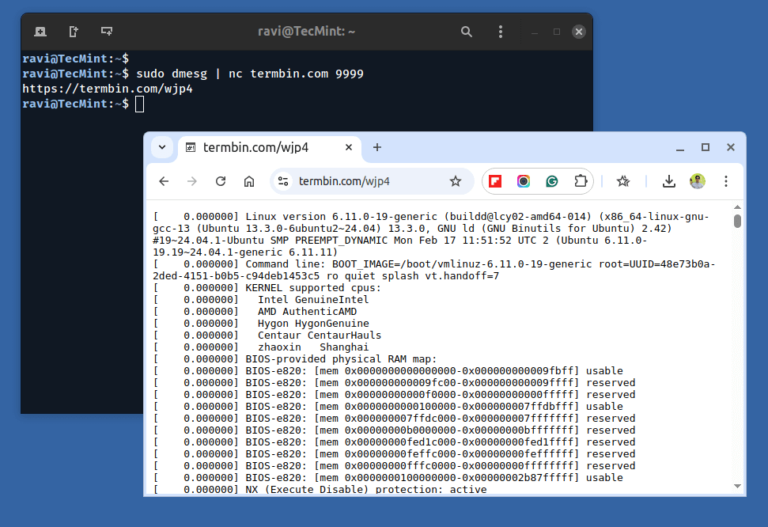
In the world of troubleshooting and collaborative debugging, sharing command-line output and error logs is an…
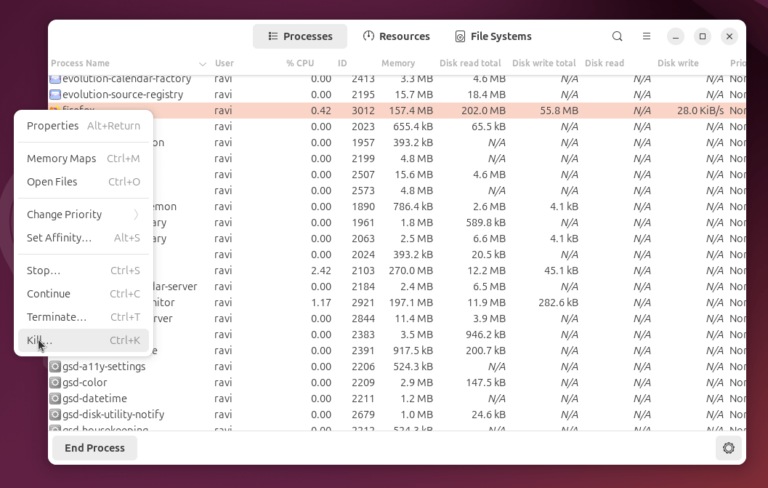
When your Ubuntu system suddenly freezes, it can be very frustrating, especially if you’re working on…
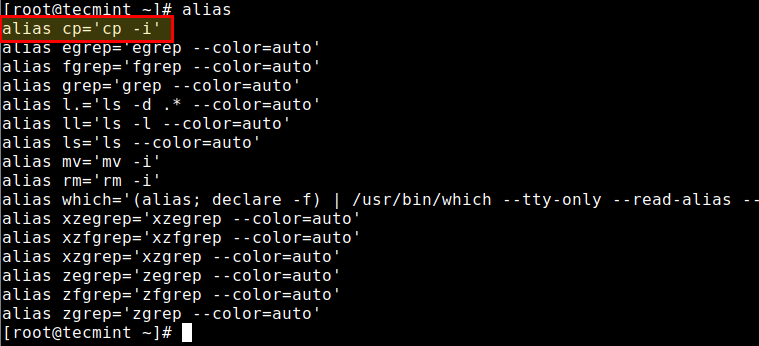
The cp command (short for copy) is one of the most commonly used commands in Linux…
Actively Exploited Zero-Day Vulnerability in Windows Common Log File System CVE-2025-27491 is a Critical RCE vulnerability…
Notepad++ is a completely free source code editor created as a replacement for Notepad on Windows…
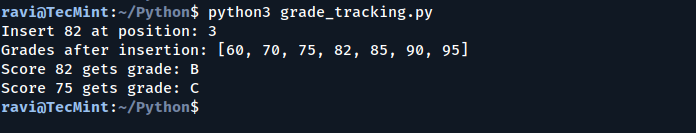
As developers, we often stick to our favorite built-in Python functions and sometimes even write custom…
Telegram has eventually become something more than a mere messaging app since its official release in…
OpenRC is a fast and lightweight init system used by many Linux distributions like Alpine, Gentoo,…
pCloud is a most secure popular cloud storage service that offers a range of features to…

In our previous article, we explored the top 5 command line archive tools, including tar, shar,…

In our day-to-day life, we often come across archived files on various platforms, whether it’s Windows,…

On systemd-based Linux distributions, managing and restarting services automatically after a failure is relatively straightforward. However,…
CrowdTour Houston | April 10From New York to Sydney, Dubai to São Paulo, London to Singapore,…
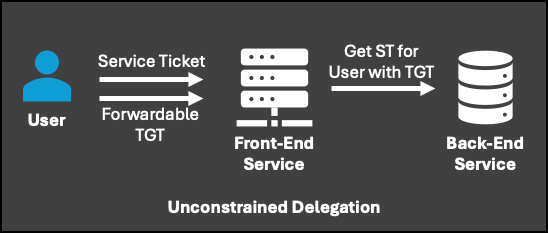
Using Certipy again, the template below would be vulnerable to ESC4.Though 2024 may be behind us,…