VCF 9.0 GA Mental Model Part 6: Topology and Identity Boundaries for Single Site, Dual Site, and Multi-Region
TL;DR Scope: VMware Cloud Foundation 9.0.0.0 GA (primary platform build 24703748) and the associated 9.0 GA…
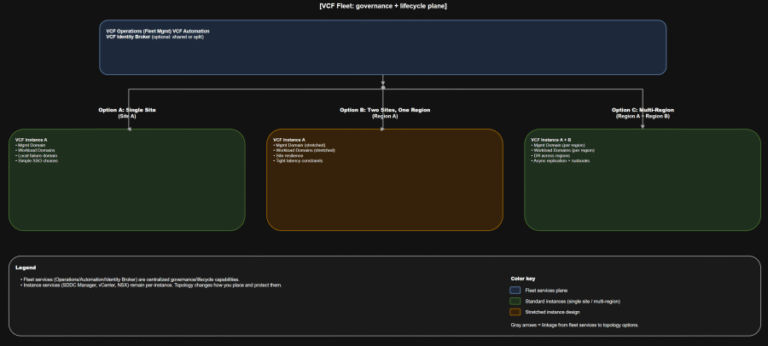
TL;DR Scope: VMware Cloud Foundation 9.0.0.0 GA (primary platform build 24703748) and the associated 9.0 GA…
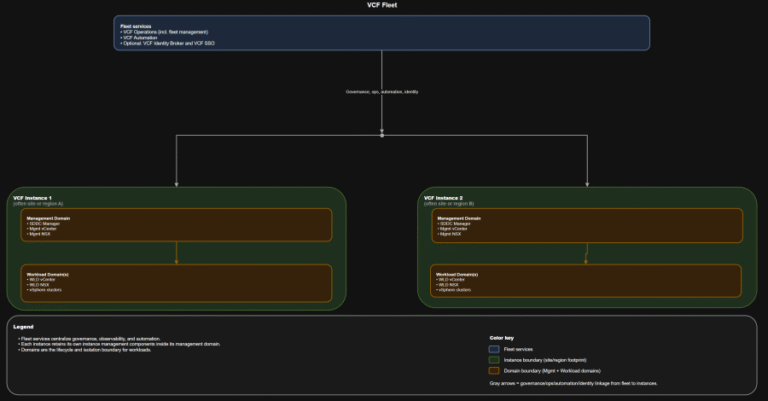
TL;DR Identity is not a “later” decision. It is a boundary decision. The hierarchy you should…
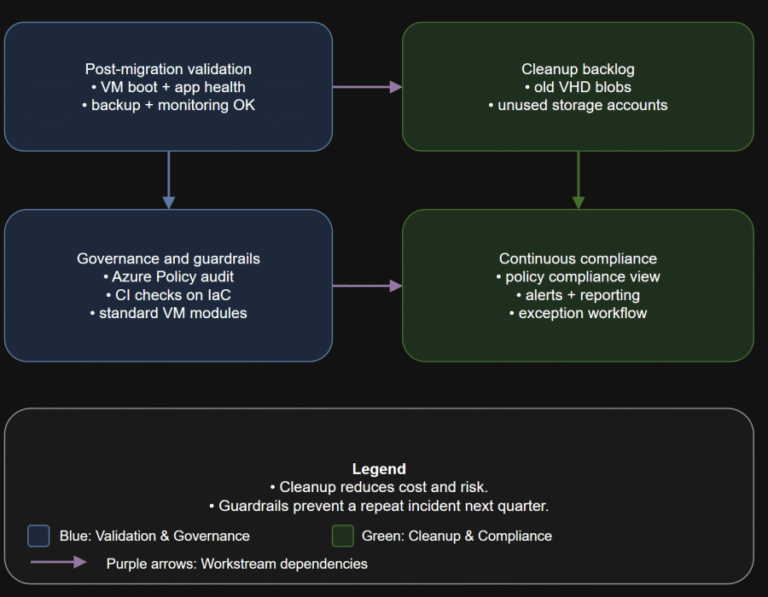
TL;DR Converting disks is not the finish line. Your real goal is a new steady state:…
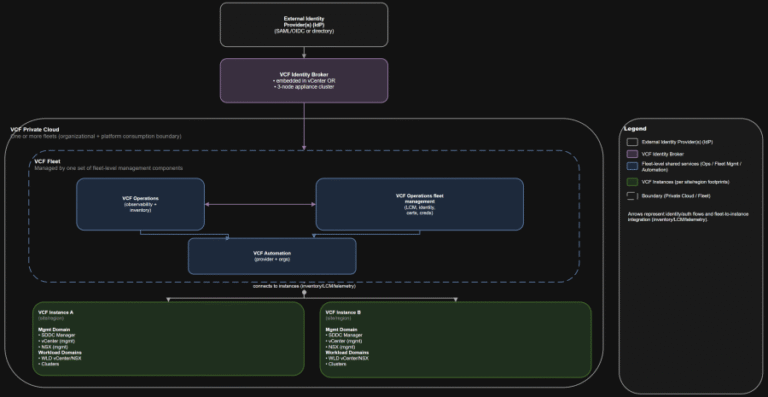
TL;DR Practical implication: if fleet services are impaired, governance and workflows degrade, but the instance-level control…

In this article, you will learn how to list, configure, enable, disable, and troubleshoot network interfaces…
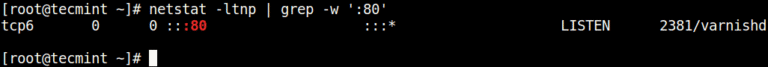
In this article, you will learn how to find which process or service is listening on…
CrowdStrike Falcon Identity Protection — A Great Tool to Gain Visibility We remain committed to innovating…
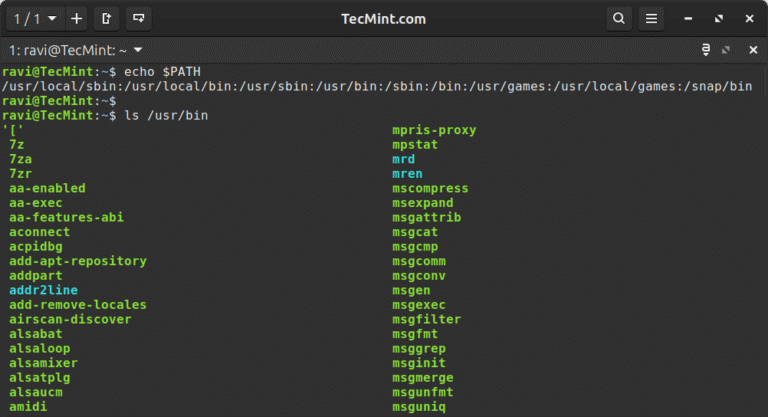
In this guide, you’ll learn five practical commands for discovering quick information about any binary command:…
Actively Exploited Zero-Day Vulnerability in Windows Remote Desktop The vulnerability allows local attackers with no privileges…
The Human-AI Feedback Loop in Action Expert-Annotated Data Enables Analyst Grade AI 2 Time savings represents…
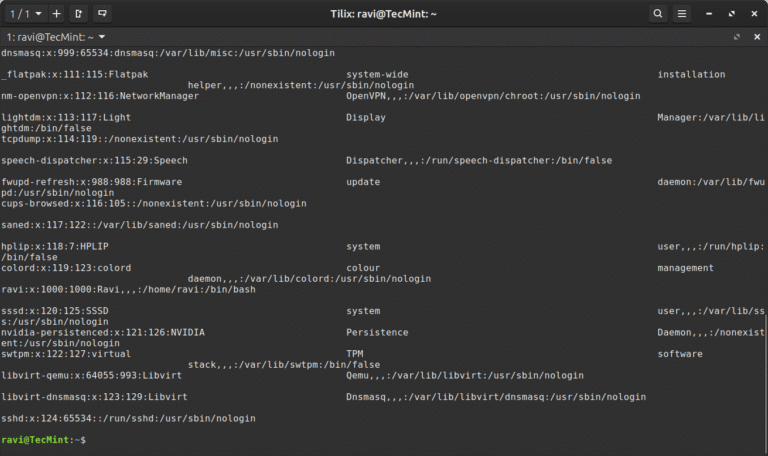
In this article, you will learn how to use the Linux column command to format text…
Indirect prompt injection significantly amplifies this risk by allowing adversaries to influence OpenClaw’s behavior through data…
As part of Falcon Cloud Security’s unified cloud-native application protection platform (CNAPP), Falcon ASPM helps organizations…
Learn how to enable and configure AI agents in ONLYOFFICE Desktop Editors to automate document editing,…
In this article, you will discover the best software tools powered by AI that you can…