Exposing Insider Threats through Data Protection, Identity, and HR Context
Insider threats pose a growing risk to organizations. Whether insiders take malicious actions, exhibit negligent behavior,…
Insider threats pose a growing risk to organizations. Whether insiders take malicious actions, exhibit negligent behavior,…

Whether you’re building your first automation workflow or exploring how AI can simplify everyday SOC tasks,…
Perform on-demand queries for forensics, compliance, or audit use cases. CrowdStrike is the first cybersecurity partner…
This blog includes descriptions of products, features, or functionality that may not be currently generally available….
We believe our placement as a Visionary, coupled with our groundbreaking AI innovations and the acquisition…
The Falcon Next-Gen SIEM Correlation Rule Template Discovery dashboard provides customers with a streamlined way to…
The Adversary’s Path to Achieving Persistence Once SCATTERED SPIDER gains access to a target organization, they…
The 2025 GigaOm Radar for SIEM highlights the notable shift to vendors offering full platforms for…
One challenge of correlating all of the attack stages together is the events for uploading an…
New UEBA in Falcon Next-Gen SIEM delivers behavior-based threat detection powered by automation, AI, and contextual…

By ingesting Microsoft Edge for Business browser data directly into Falcon Next-Gen SIEM, and correlating it…
They detect techniques across the entire cyber kill chain with out-of-the-box correlation rules mapped to both…
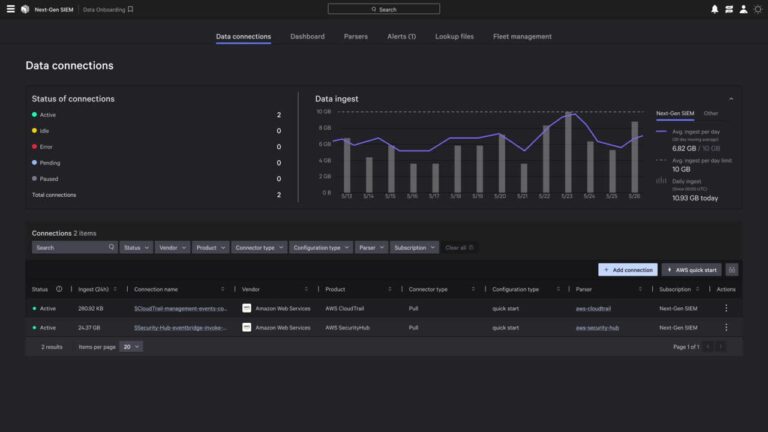
It all starts with getting data in. Unlike their predecessors, the next generation of SIEMs live…
Adversaries may tamper with organizations’ infrastructure to facilitate data exfiltration. Some examples include:It is essential to…

Fal.Con 2024 wasn’t just about product innovation — it was about delivering an unforgettable experience with…