Why Linux Powers Everything From Your Coffee Machine to Mars Rovers
When most people think about operating systems, they picture Windows laptops or MacBooks, but here’s what’s…

When most people think about operating systems, they picture Windows laptops or MacBooks, but here’s what’s…

When someone visits your website, their browser and your server exchange information back and forth. Without…
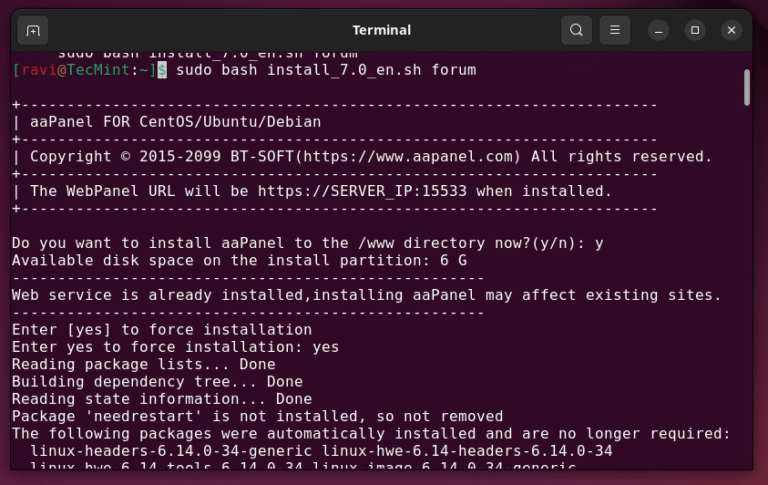
Managing a web server through command-line alone can feel like you’re juggling too many things at…
Here, we examine a case study in which CrowdStrike OverWatch threat hunters identified and disrupted BLOCKADE…
Despite the revolutionary agentic delivery mechanism used to achieve groundbreaking speed and scale in this attack,…
The outcomes that matter most — speed, accuracy, cost, and real-time risk reduction — can only…
Zero-Day Vulnerability in Windows Kernel When successfully exploited, attackers can gain SYSTEM privileges by winning a…

These reports include:With Falcon Cloud Security data correlated in Falcon Next-Gen SIEM, teams can detect cross-domain…
Key capabilities:Using the single Falcon sensor, organizations can move from deployment to complete XIoT visibility in…
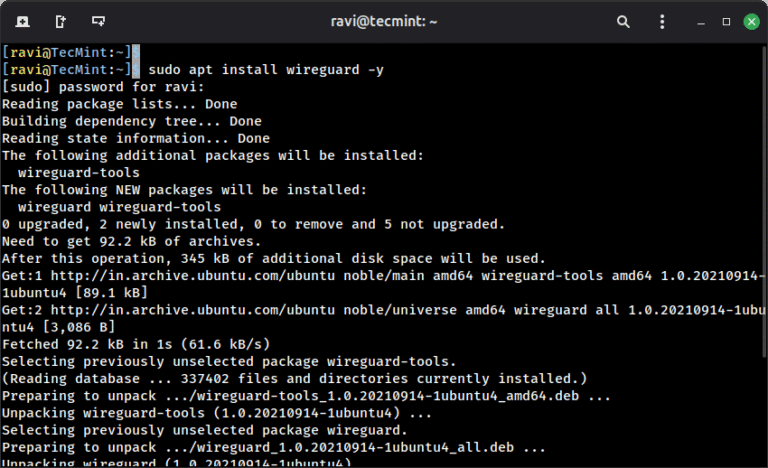
When you connect to a coffee shop’s WiFi or access the internet from any public network,…

Earlier this year, in testing against ransomware attacks, SE Labs employed realistic scenarios using tactics and…
Coerced Authentication The initial reconnaissance and setup phase requires minimal resources but careful planning. The attack…
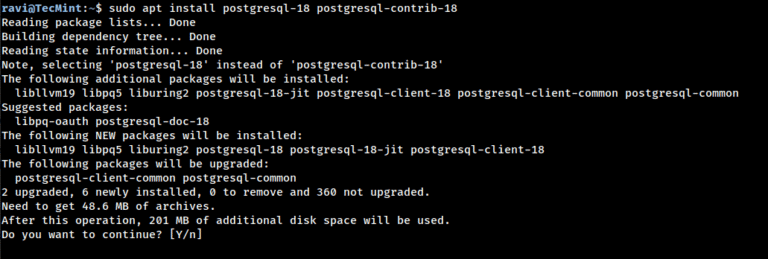
PostgreSQL (Postgres in short) is an open source, powerful, advanced, high-performance, and stable relational-document database system,…
Windows 10 End of Support Is Here There is evidence of active exploitation in the wild…
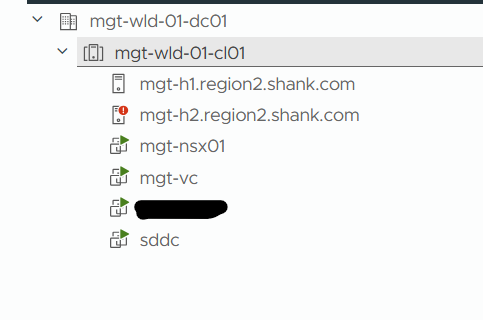
October 13, 2025 VCF 9 Fleet Deployment Task Fails The Issue? As with any failed deployment,…