Data Protection Day 2026: From Compliance to Resilience
Christoph Bausewein is Assistant General Counsel for Data Protection and Policy at CrowdStrike.This creates a new…
Christoph Bausewein is Assistant General Counsel for Data Protection and Policy at CrowdStrike.This creates a new…
– System Security Manager, Services (non-Government) IndustryThe truest assessment of the Falcon platform comes from the…
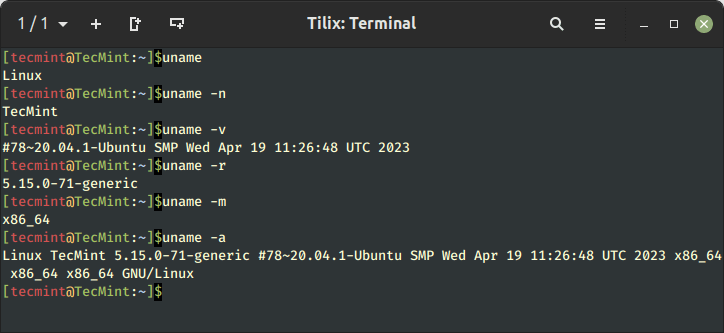
Learn 11 essential Linux commands to check hardware info including CPU, RAM, disk, USB, and PCI…
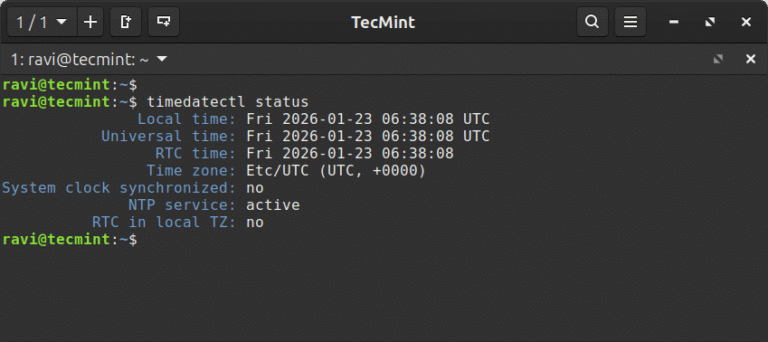
In this article, learn how to set time, timezone, and synchronize your Linux system clock with…
Precise device access: Security teams can allow, restrict, or block removable media based on device attributes,…
I’m delighted to announce CrowdStrike’s intent to acquire Seraphic, the leader in browser runtime security. With…
Actively Exploited Zero-Day Vulnerability in Windows Desktop Window Manager CVE-2026-20955 and CVE-2026-20957 are Critical remote code…
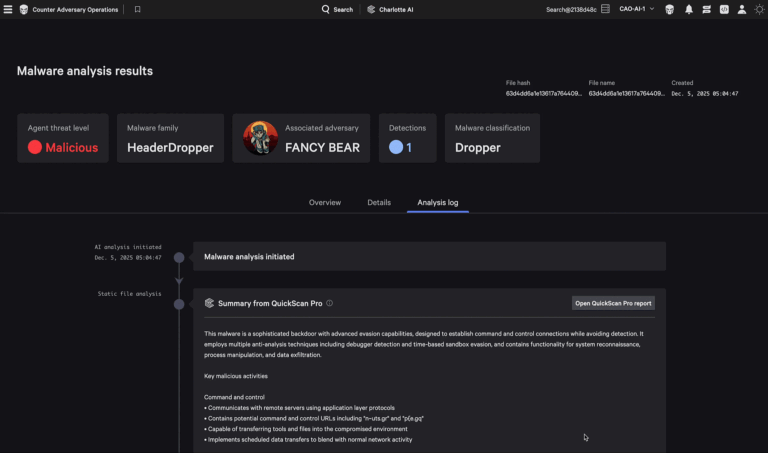
Under the Hood: How It Works Step 3: Dynamic behavioral analysis Step 5: Similar sample identification…
With the cluster infrastructure in place through the Vertex Training Cluster, we configured Slurm, the industry-standard…
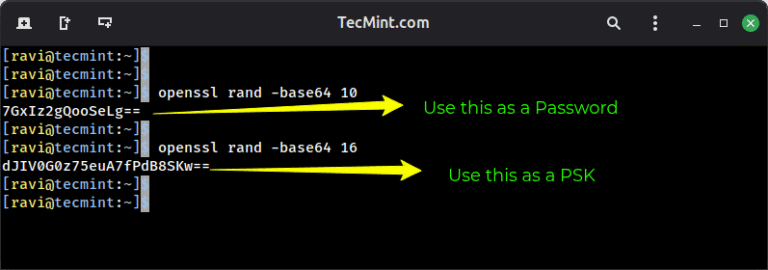
There are so many benefits of using a VPN (Virtual Private Network), some of which include…
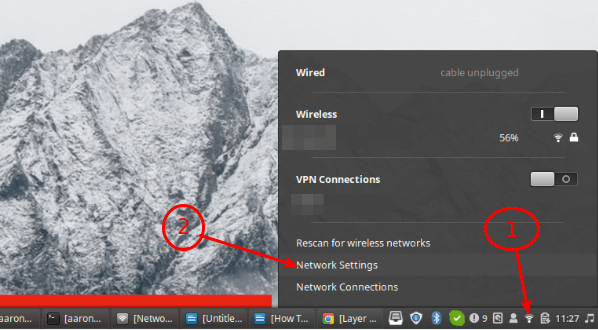
L2TP (which stands for Layer 2 Tunneling Protocol) is a tunneling protocol designed to support virtual…
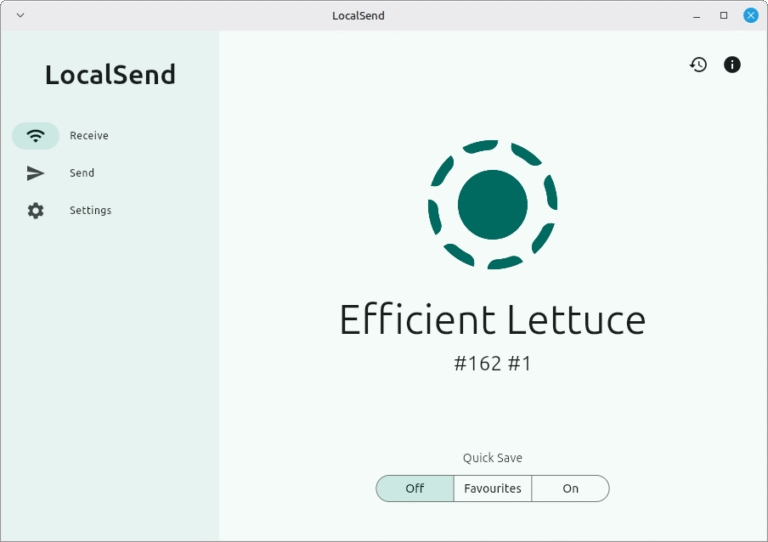
One of the most important uses of a network is for file sharing purposes, and there…
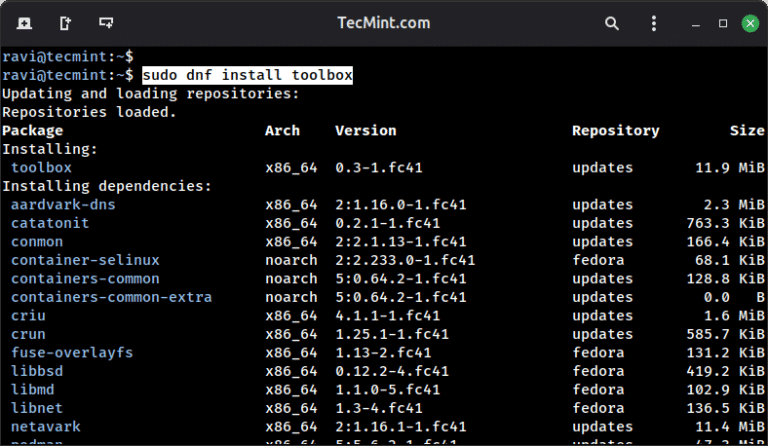
Modern Linux development has moved beyond the traditional approach of installing everything directly on your system….
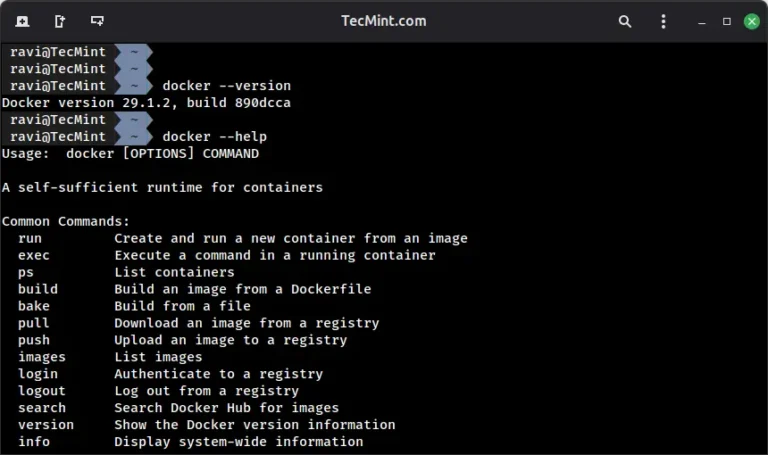
If you’re looking to get started with Docker, understanding how to work with its command-line interface…
WARP PANDA demonstrates a high level of stealth and almost certainly focuses on maintaining persistent, long-term,…