How CrowdStrike’s Malware Analysis Agent Detects Malware at Machine Speed
Under the Hood: How It Works Step 3: Dynamic behavioral analysis Step 5: Similar sample identification…
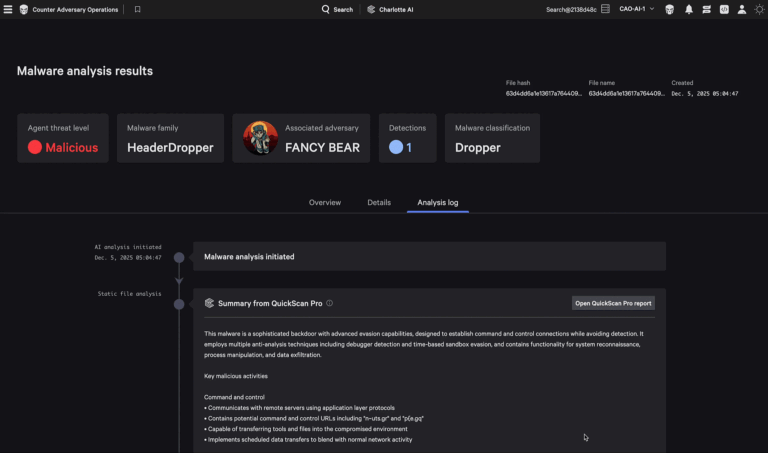
Under the Hood: How It Works Step 3: Dynamic behavioral analysis Step 5: Similar sample identification…
These content packs span multiple categories including application resilience, file discovery, Linux device control, and asset…
Pillar #1: A Rich Corpus of Human-refined Data In cybersecurity, AI agents don’t operate in a…
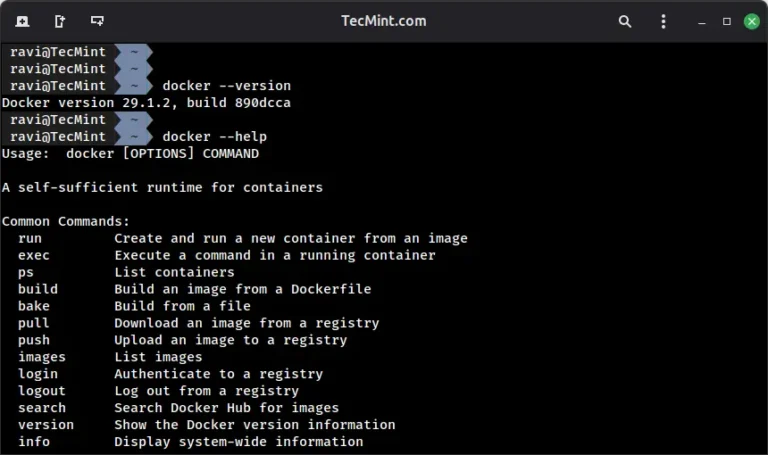
If you’re looking to get started with Docker, understanding how to work with its command-line interface…

In the MUSTANG PANDA scenario, the adversary embedded encoded shellcode within their malware in an attempt…
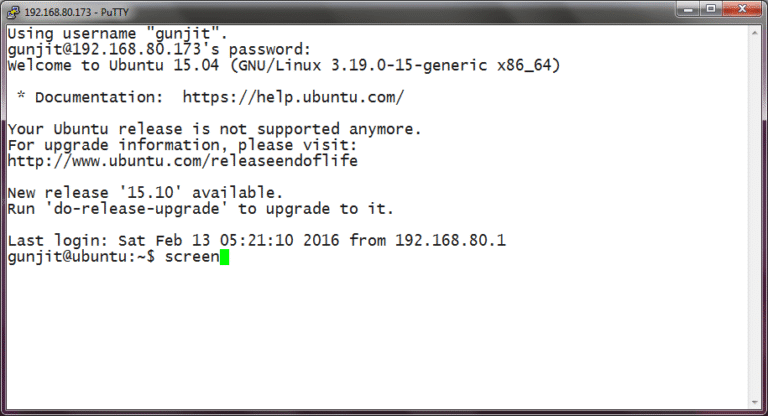
SSH or Secure Shell in simple terms is a way by which a person can remotely…
Identity has become a key battleground of modern cybersecurity. In 2024, 79% of CrowdStrike detections were…
There are two basic types of prompt injection attacks: Understanding Prompt Injection Employee BYO AI adoption…
WARP PANDA demonstrates a high level of stealth and almost certainly focuses on maintaining persistent, long-term,…

When most people think about operating systems, they picture Windows laptops or MacBooks, but here’s what’s…

When someone visits your website, their browser and your server exchange information back and forth. Without…
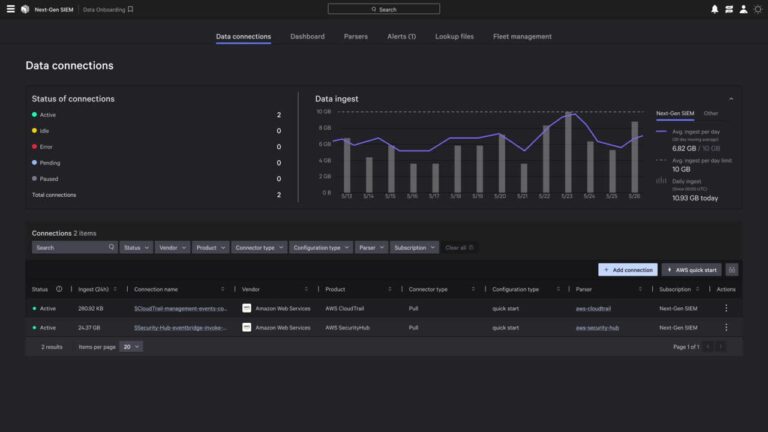
Perform on-demand queries for forensics, compliance, or audit use cases. CrowdStrike is the first cybersecurity partner…
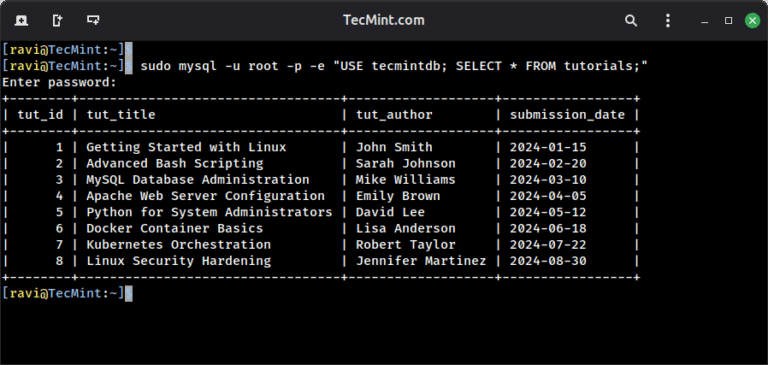
If you are in charge of managing a database server, from time to time you may…
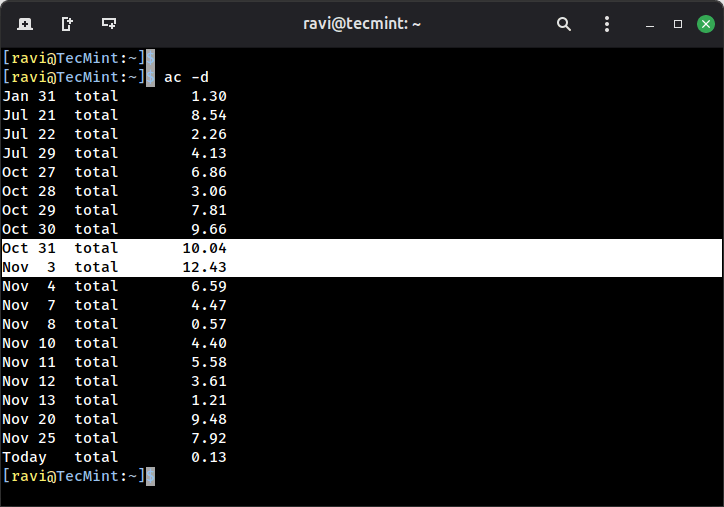
When you’re managing a Linux server, especially one with multiple users, you need visibility into what’s…
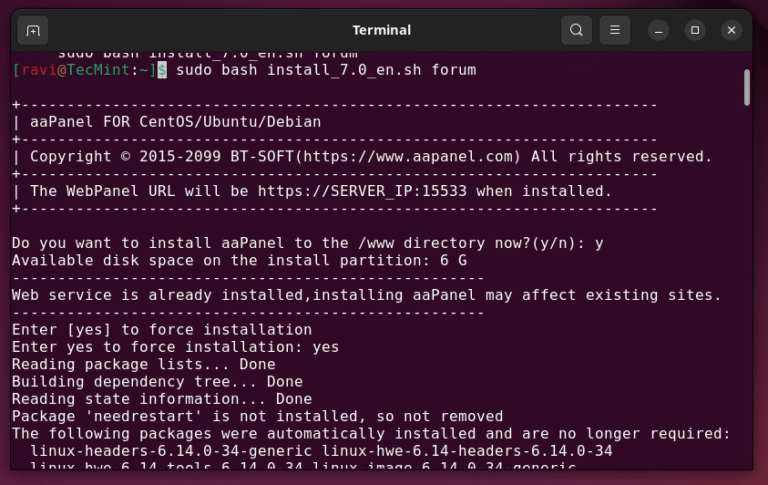
Managing a web server through command-line alone can feel like you’re juggling too many things at…