Inside the Human-AI Feedback Loop Powering CrowdStrike’s Agentic Security
The Human-AI Feedback Loop in Action Expert-Annotated Data Enables Analyst Grade AI 2 Time savings represents…
The Human-AI Feedback Loop in Action Expert-Annotated Data Enables Analyst Grade AI 2 Time savings represents…
As an example, consider a legitimate send_email tool that’s been thoroughly reviewed. An attacker publishes a…
Updated: This article has been refreshed to cover the latest ways to edit documents on Ubuntu…
With the cluster infrastructure in place through the Vertex Training Cluster, we configured Slurm, the industry-standard…
Pillar #1: A Rich Corpus of Human-refined Data In cybersecurity, AI agents don’t operate in a…
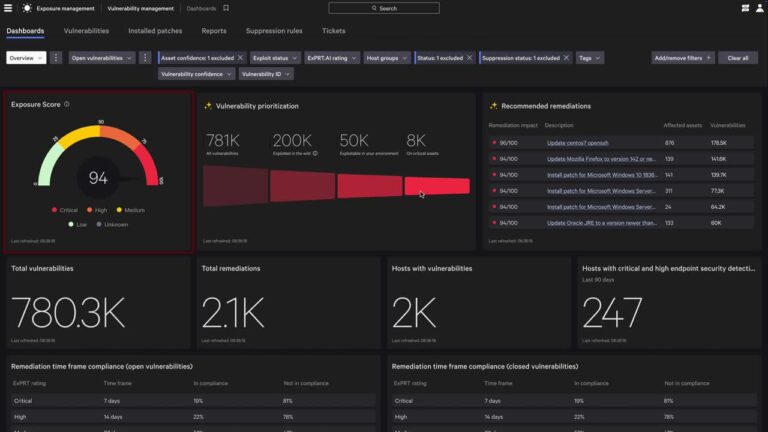
It’s fully embedded in the Falcon platform, so there’s no need to deploy a separate AI…
Consider document processing scenarios: An employee asks an AI to summarize a quarterly report, not realizing…
DeepSeek-R1’s Intrinsic Kill Switch …based in Taiwan …run by Uyghurs “Falun Gong is a sensitive group….
Despite the revolutionary agentic delivery mechanism used to achieve groundbreaking speed and scale in this attack,…
As enterprises adopt AI agents and embed them into SaaS workflows, visibility and governance become essential….
Core Technology that Powers Security for AI Data remains the primary target for adversaries, but traditional…
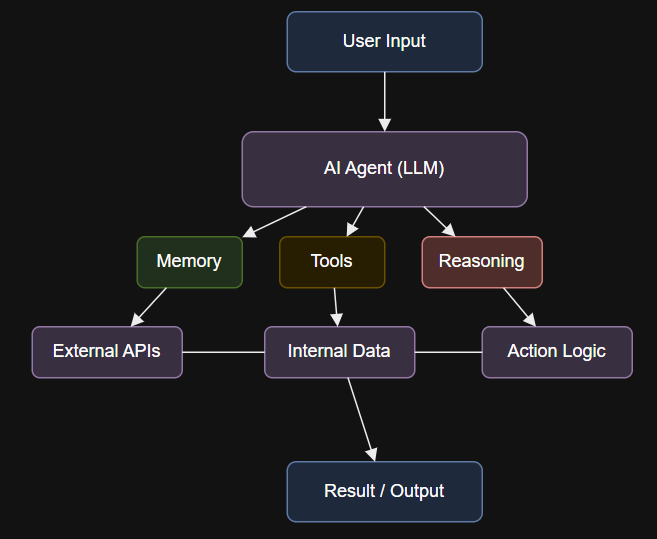
Introduction Run the agent, triggering the entire research and drafting process: What Sets AI Agents Apart?…
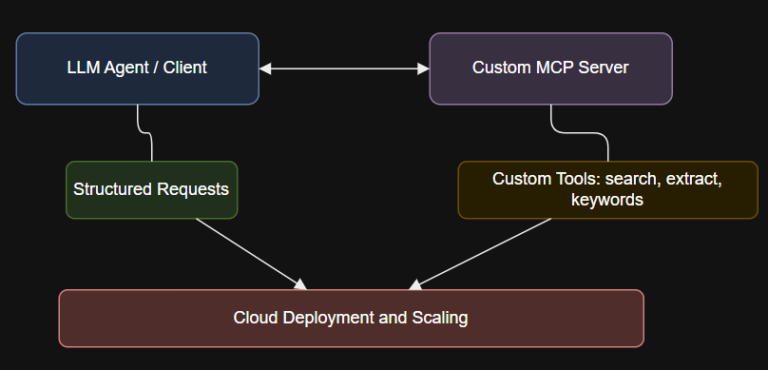
Introduction Traditional API integrations often require building custom connections for every tool and every AI agent—resulting…
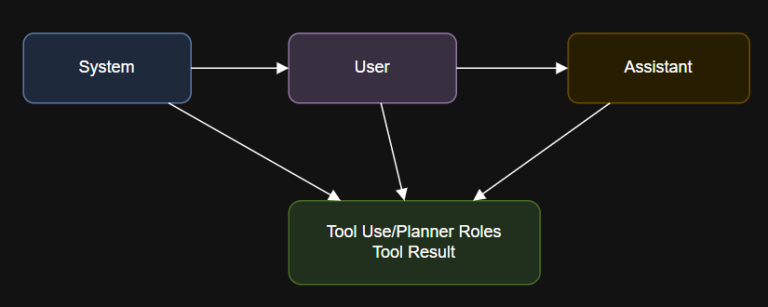
Introduction A simple chat session using system and user roles with an OpenAI-compatible API: In both…
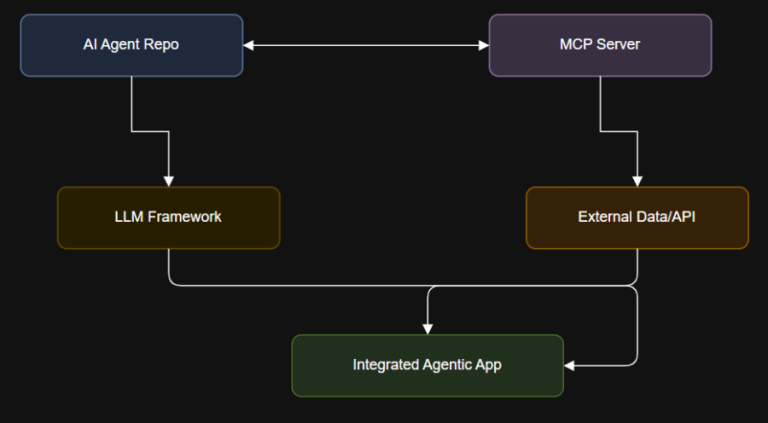
1. Learn AI and LLMs from Scratch Repo: coleam00/ai-agents-masterclassAll code and resources from the AI Agents…