Falcon for IT Redefines Vulnerability Management with Risk-based Patching
Traditional vulnerability management is broken. Security teams rely on one set of tools to find vulnerabilities;…
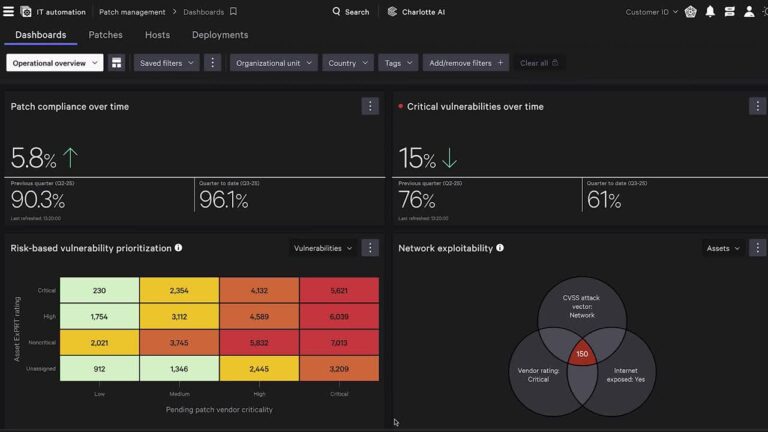
Traditional vulnerability management is broken. Security teams rely on one set of tools to find vulnerabilities;…
The Falcon platform’s console unifies fragmented data, bridges silos, and translates complex queries into natural-language conversations….
Core Technology that Powers Security for AI Data remains the primary target for adversaries, but traditional…
Stopping Breaches with Platform-Native Speed and Expertise With over 100,000 hours of IR casework annually, CrowdStrike…
Security teams today face a data crisis: Exploding volumes of security and IT telemetry are difficult…
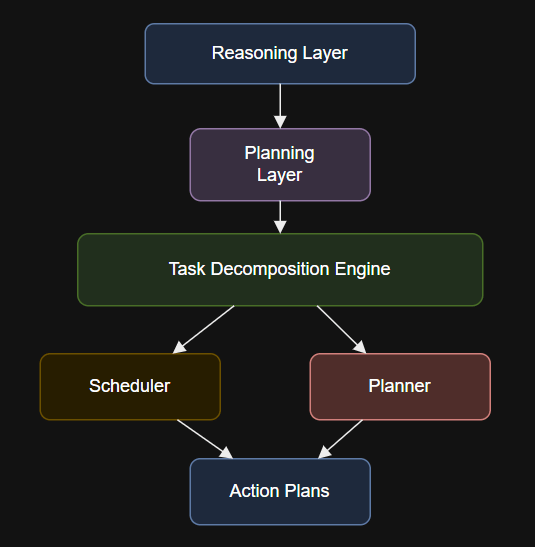
Introduction @app.task(bind=True, max_retries=3)def execute_api_action(self, endpoint, payload):try:response = requests.post(endpoint, json=payload, timeout=10)response.raise_for_status()return {“status”: “success”, “response”: response.json()}except Exception as…
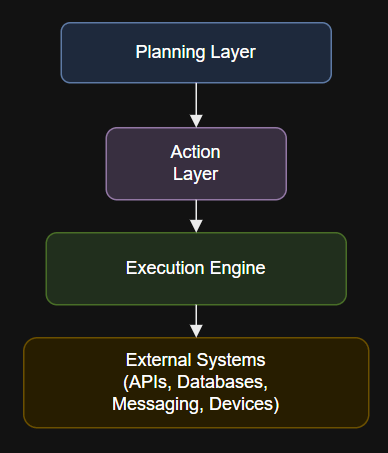
Introduction def notify_team(**kwargs):print(“Notifying team…”) What This Layer Is and Why It Matters Explore workflow planning and…
Since late 2024, CrowdStrike Counter Adversary Operations has observed significant activity conducted by MURKY PANDA, a…
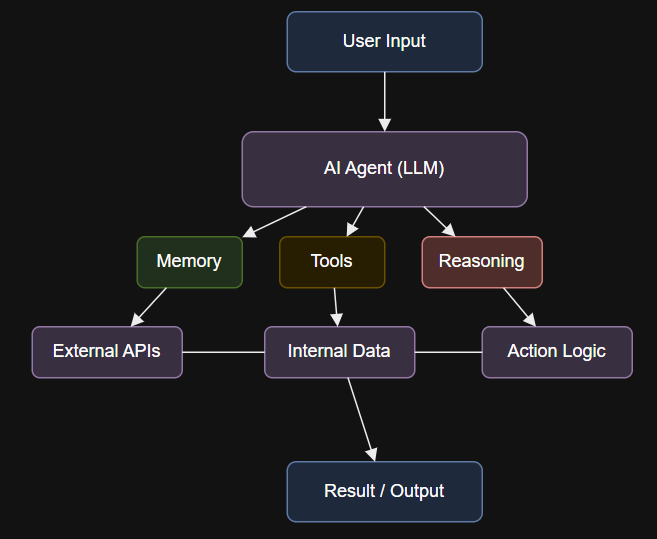
Introduction Run the agent, triggering the entire research and drafting process: What Sets AI Agents Apart?…
CrowdStrike is excited to announce CrowdStrike Falcon® Next-Gen Identity Security, a new solution built to protect…
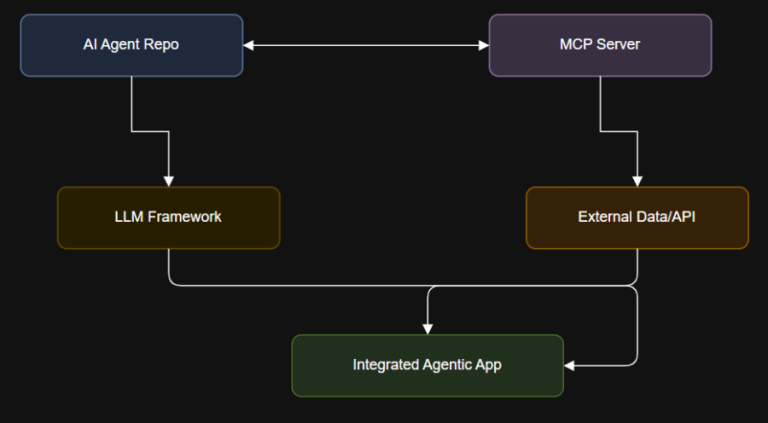
1. Learn AI and LLMs from Scratch Repo: coleam00/ai-agents-masterclassAll code and resources from the AI Agents…
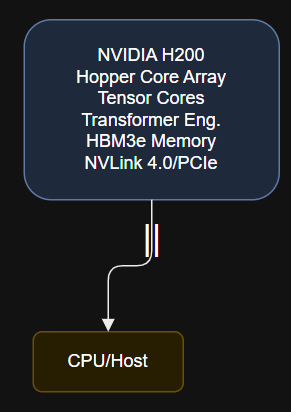
Why GPUs Matter in AI Workloads AMD’s Instinct MI300X, announced for production in 2025, is built…
AI must be deployed strategically in the SOC to outpace AI-savvy adversaries. The Threat Hunting Report…

This enhanced workflow turns every indicator into actionable intelligence so teams can conduct smarter, faster investigations….
Today’s enterprising adversaries are weaponizing AI to scale operations, accelerate attacks, and target the autonomous AI…