Falcon for XIoT Extends Asset Protection to Healthcare Environments
Detect Exposures and Prioritize Threats to Connected Medical Devices The lightweight Falcon sensor will use threat…
Detect Exposures and Prioritize Threats to Connected Medical Devices The lightweight Falcon sensor will use threat…
This milestone comes as the UK places increased emphasis on cyber resilience, operational assurance, and incident…

Stopping compromised access at login is essential, but identity risk doesn’t end there. CrowdStrike acquired SGNL…
To defend themselves, security leaders need clarity on which adversaries to watch, the details of their…
Insider threats pose a growing risk to organizations. Whether insiders take malicious actions, exhibit negligent behavior,…

Whether you’re building your first automation workflow or exploring how AI can simplify everyday SOC tasks,…
The Human-AI Feedback Loop in Action Expert-Annotated Data Enables Analyst Grade AI 2 Time savings represents…
Actively Exploited Zero-Day Vulnerability in Windows Remote Desktop The vulnerability allows local attackers with no privileges…
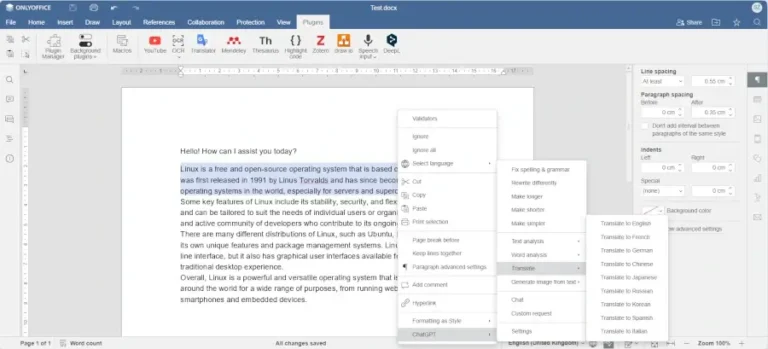
Learn how to enable and configure AI agents in ONLYOFFICE Desktop Editors to automate document editing,…
In this article, you will discover the best software tools powered by AI that you can…
GOLDEN CHOLLIMA Shared infrastructure elements and tool cross-pollination indicate these units maintain close coordination. All three…
Christoph Bausewein is Assistant General Counsel for Data Protection and Policy at CrowdStrike.This creates a new…
– System Security Manager, Services (non-Government) IndustryThe truest assessment of the Falcon platform comes from the…
Precise device access: Security teams can allow, restrict, or block removable media based on device attributes,…
Expert Agents: Native AI Reasoning Across the Falcon Platform Effective threat triage requires correlating evidence across…