CrowdStrike Falcon Scores Perfect 100% in SE Labs’ Most Challenging Ransomware Test
SE Labs employed both direct attacks and deep attacks. Test results and the feedback of third-party…

SE Labs employed both direct attacks and deep attacks. Test results and the feedback of third-party…
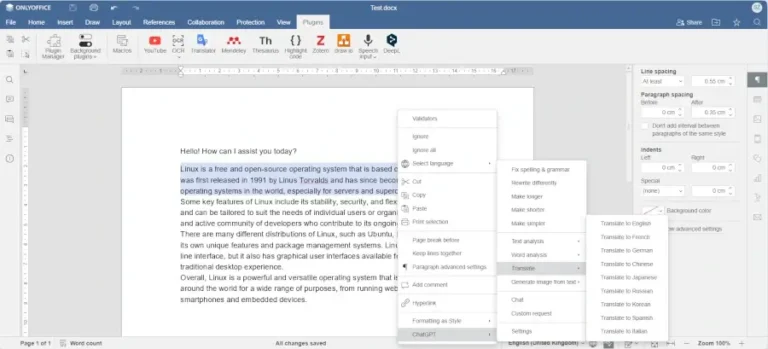
In this article, you will discover the best software tools powered by AI that you can…
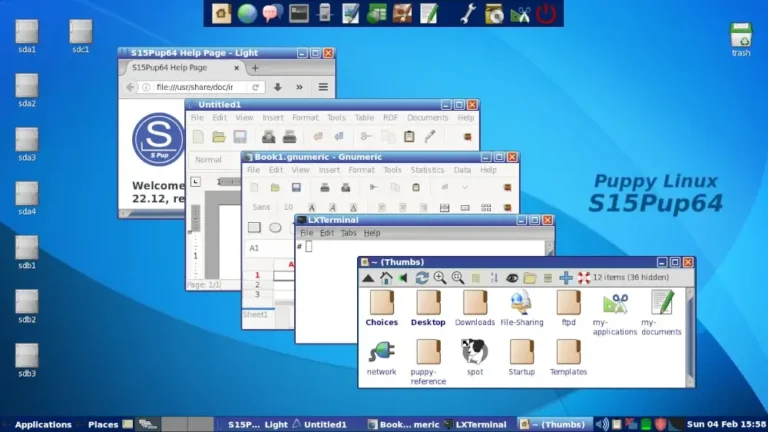
In this guide, we feature some of the best Linux distributions that you can install on…
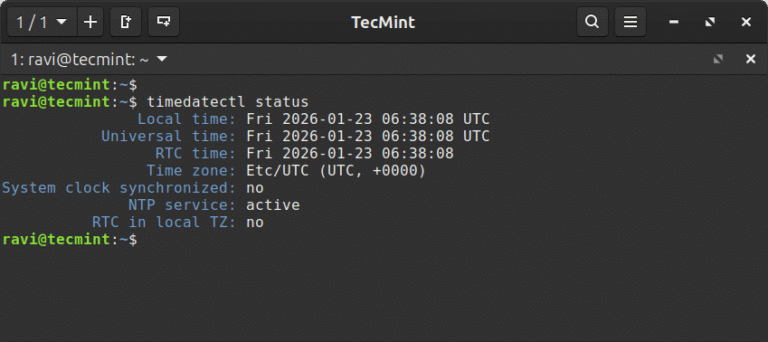
In this article, learn how to set time, timezone, and synchronize your Linux system clock with…

In the MUSTANG PANDA scenario, the adversary embedded encoded shellcode within their malware in an attempt…
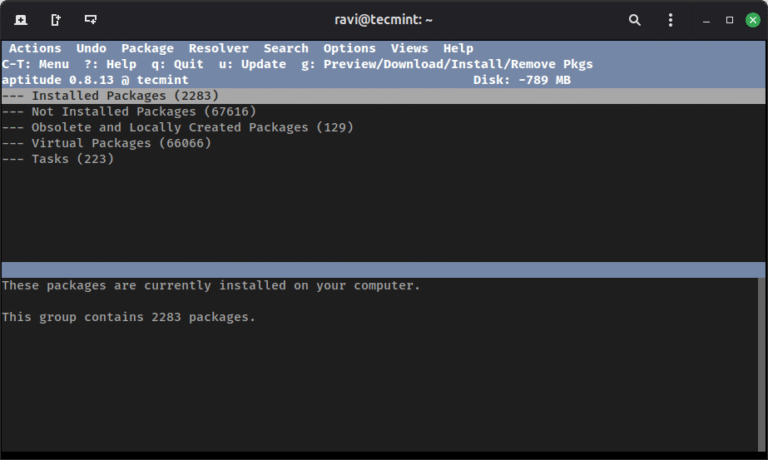
Debian offers several tools for managing software packages, each serving a specific purpose in the package…

Android software development involves creating applications for devices running the Android operating system, primarily using Kotlin…
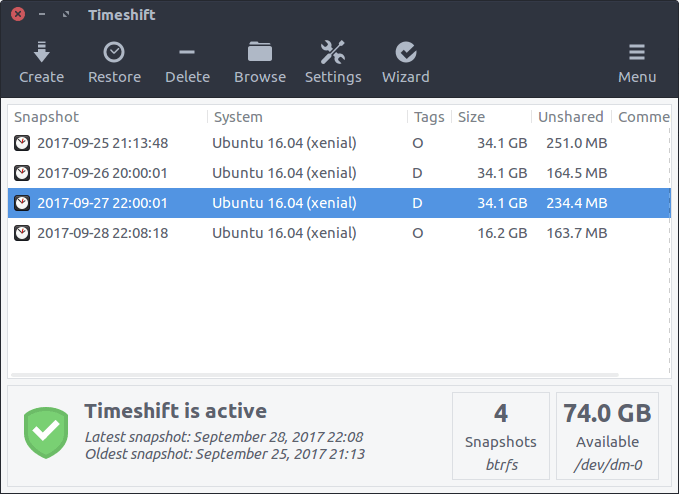
It isn’t easy to figure out which of the many Linux apps out there are actually…
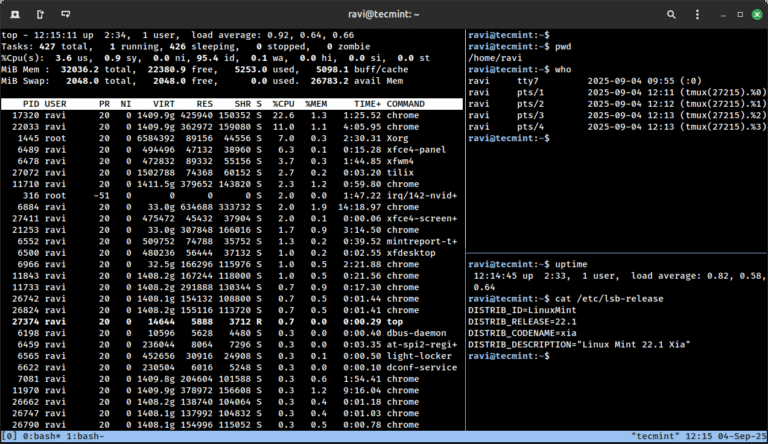
It is time once again to share a list of the best free and open-source software…
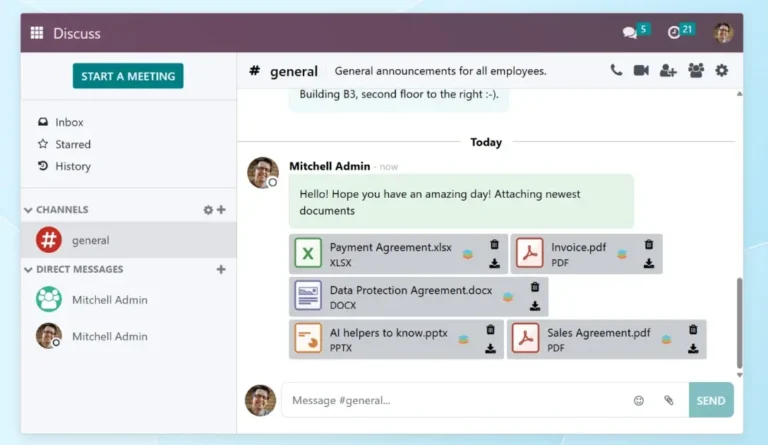
Odoo is the ideal open-source enterprise software for teams and businesses that value flexibility, data privacy,…
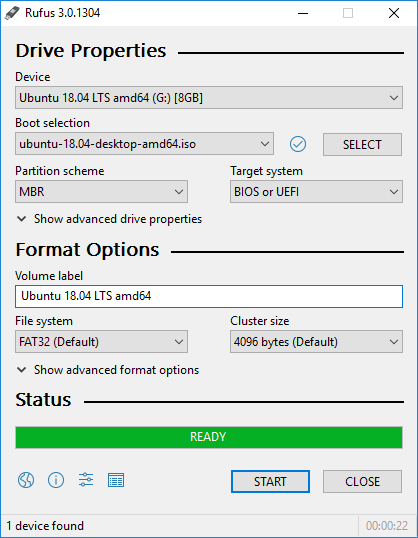
CD and DVD writers are a thing of the past. You are not likely to find…

What’s New in VCF 9 (with NSX) GUI steps and automation for these features follow similar…

OCR stands for optical character recognition, and software of this type is designed to convert images,…
Ubuntu is known for its user-friendly interface and robust performance, but over time, even the best…
Notepad++ is a completely free source code editor created as a replacement for Notepad on Windows…