CrowdStrike Endpoint Security Achieves 273% ROI Over Three Years
Organizations are under pressure to protect more devices, users, and distributed workloads than ever — while…
Organizations are under pressure to protect more devices, users, and distributed workloads than ever — while…
Traditional security tools were never built to protect AI assets across domains or the new AI…
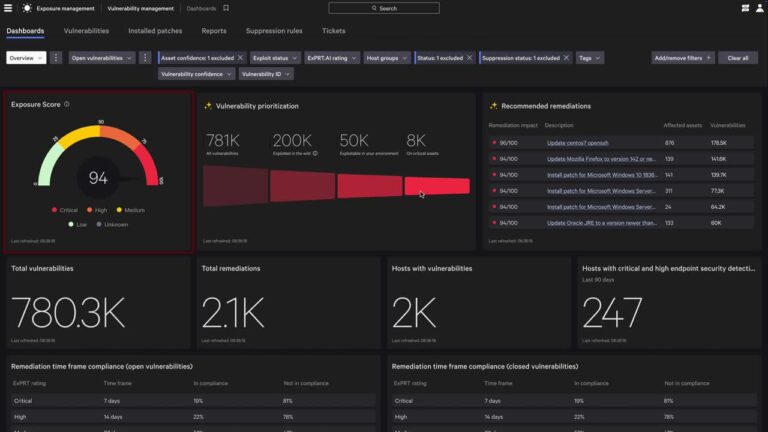
It’s fully embedded in the Falcon platform, so there’s no need to deploy a separate AI…

In the MUSTANG PANDA scenario, the adversary embedded encoded shellcode within their malware in an attempt…
There are two basic types of prompt injection attacks: Understanding Prompt Injection Employee BYO AI adoption…
CrowdStrike uses NVIDIA Nemotron open models in CrowdStrike Falcon® Fusion SOAR and CrowdStrike Charlotte AI™ AgentWorks….
Despite the revolutionary agentic delivery mechanism used to achieve groundbreaking speed and scale in this attack,…
Zero-Day Vulnerability in Windows Kernel When successfully exploited, attackers can gain SYSTEM privileges by winning a…
There’s no doubt that Skype was once one of the most popular instant messaging and video…

Earlier this year, in testing against ransomware attacks, SE Labs employed realistic scenarios using tactics and…
Coerced Authentication The initial reconnaissance and setup phase requires minimal resources but careful planning. The attack…
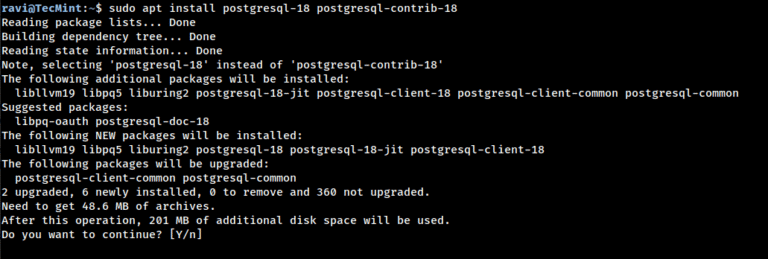
PostgreSQL (Postgres in short) is an open source, powerful, advanced, high-performance, and stable relational-document database system,…
Unsupported operating systems have historically become adversary targets. The longer a system remains unsupported, the more…
In Linux and other Unix-like operating systems, the init (initialization) process is the first process executed…

These new innovations are the essential pillars that define the agentic security platform. We are living…