EMBER2024: Advancing the Training of Cybersecurity ML Models Against Evasive Malware
To solve this problem, the feature calculation code was updated to use the most recent version…
To solve this problem, the feature calculation code was updated to use the most recent version…
Assessment rescue-mac[.]com https[:]//macostutorial[.]com/iterm2/install[.]sh Recommended Prevention Settings https[:]//macostutorial[.]com/iterm2/update Suspicious process prevention Intelligence-sourced threat prevention Threat Hunting Queries …
“Leakage” in machine learning (ML) occurs when data that an ML model should not learn on…
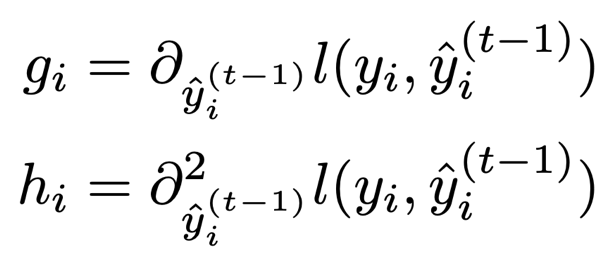
A note to the observant reader (not from the docs): In the above expansion, the loss…
CrowdStrike researchers have developed a next-gen method to train byte-based Transformer blocks that help models “understand”…
Detecting MFA Fatigue Compromising an account via delegate authority requires the organization to be enrolled in…