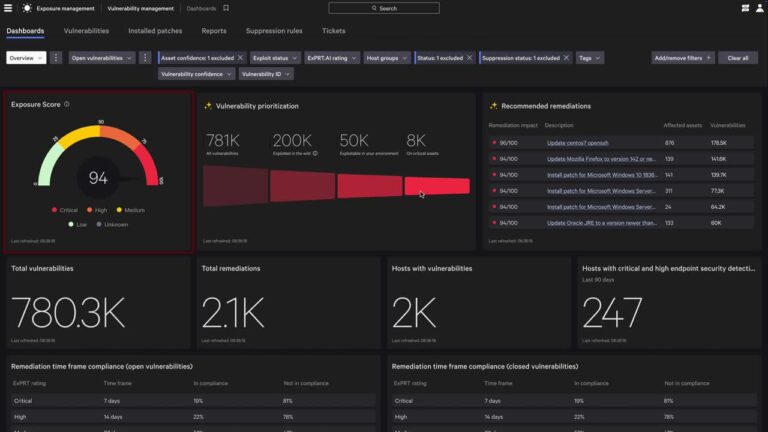
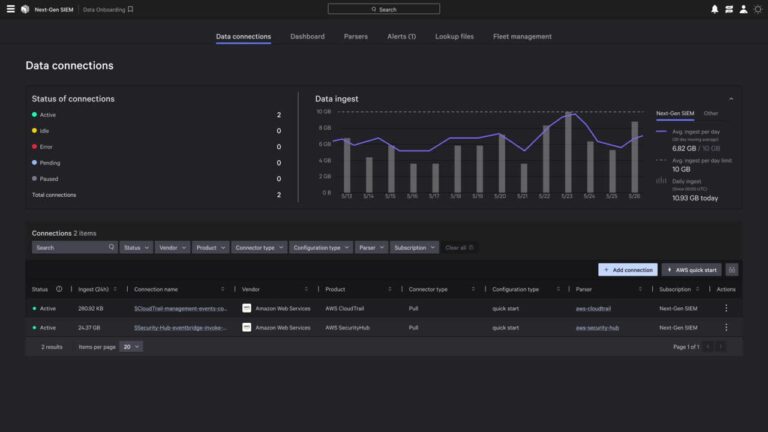
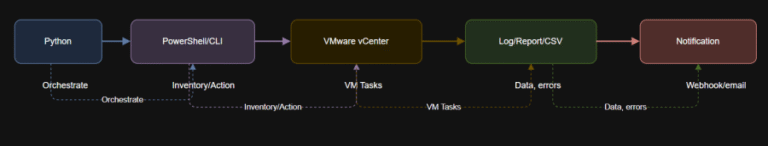
CrowdStrike Named a Customers’ Choice in 2026 Gartner Peer Insights™ Voice of the Customer for Application Security Posture Management Tools
As part of Falcon Cloud Security’s unified cloud-native application protection platform (CNAPP), Falcon ASPM helps organizations…