Announcing the CrowdStrike 2025 Global CrowdTour: Bringing the Power of the Crowd to a City Near You
CrowdTour Houston | April 10From New York to Sydney, Dubai to São Paulo, London to Singapore,…
CrowdTour Houston | April 10From New York to Sydney, Dubai to São Paulo, London to Singapore,…
Securing the Nation’s Most Critical Systems: CrowdStrike Achieves FedRAMP High Authorization In an era where adversaries…
Artificial intelligence (AI) is rapidly transforming industries, but with this innovation come new security challenges as…
The aforementioned processes would likely take weeks or even months when totaling hundreds of terabytes and…
This integration will provide an in-depth understanding of how threats impact interconnected applications and endpoints. In…
They detect techniques across the entire cyber kill chain with out-of-the-box correlation rules mapped to both…
1. Initial Entry and Exploitation After gaining initial access, the adversary moved laterally through the network…
Falcon Cloud Security Proactive Security offers USPM, which provides business context-driven security and leverages industry-leading threat…
Adversaries may tamper with organizations’ infrastructure to facilitate data exfiltration. Some examples include:It is essential to…
Since its customer story was first published in 2023, the University of Sunderland has expanded its…
When Conventional Security Meets Modern Cloud Threats These challenges demand a new approach to cloud security….
Falcon Cloud Security has them covered. With a single tool and cohesive UI experience, it provides…
Cloud computing has revolutionized how businesses operate, and its influence continues to grow in 2025. With…
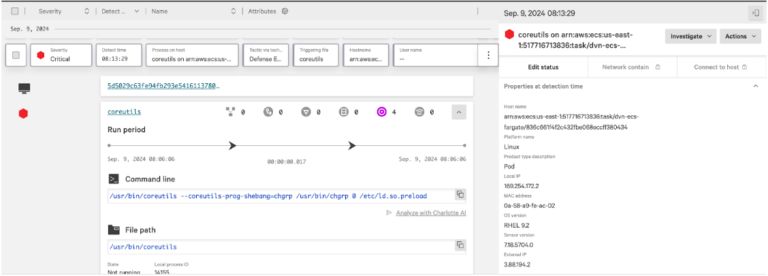
CrowdStrike commonly sees adversaries moving between the endpoint and identity planes, or from the cloud to…
Customers using Falcon Cloud Security for image assessments can now take advantage of these massive ML…