What Security Teams Need to Know About OpenClaw, the AI Super Agent
Indirect prompt injection significantly amplifies this risk by allowing adversaries to influence OpenClaw’s behavior through data…
Indirect prompt injection significantly amplifies this risk by allowing adversaries to influence OpenClaw’s behavior through data…
As part of Falcon Cloud Security’s unified cloud-native application protection platform (CNAPP), Falcon ASPM helps organizations…
Learn how to enable and configure AI agents in ONLYOFFICE Desktop Editors to automate document editing,…
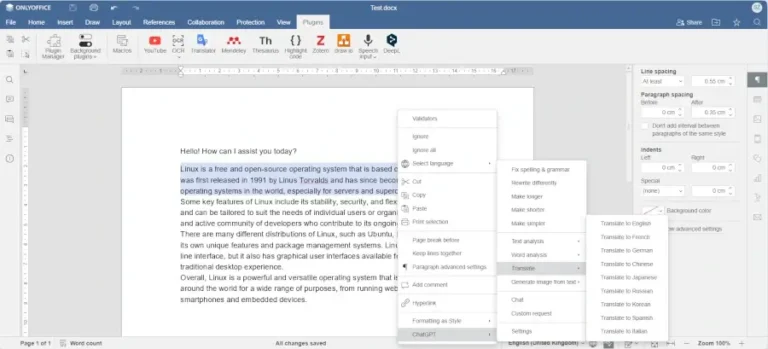
In this article, you will discover the best software tools powered by AI that you can…
Updated: This article has been refreshed to cover the latest ways to edit documents on Ubuntu…
Types of AI Tool Poisoning Attacks Consider a scenario where an attacker publishes a tool with…
SGNL provides the runtime access enforcement layer that sits between modern identity providers and the SaaS…
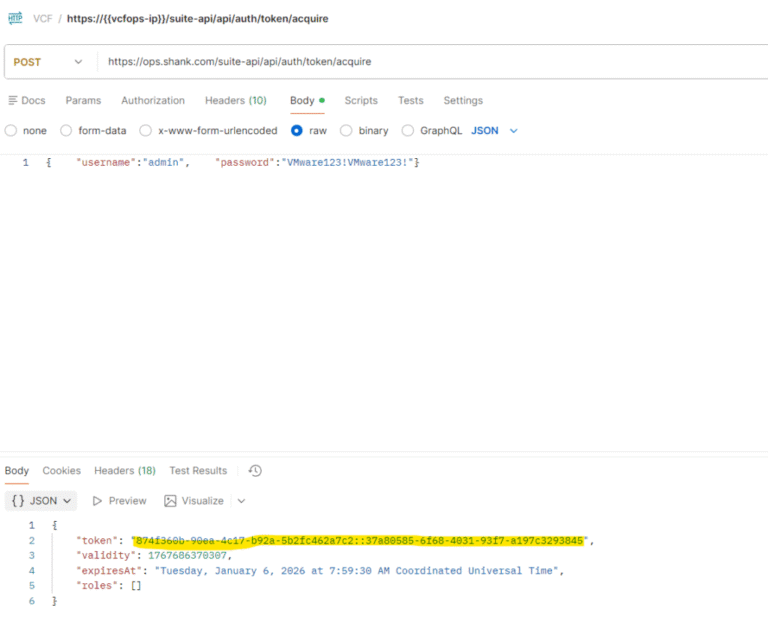
January 7, 2026 Authentication Failure: VCF SSO Broken vCenter vIDB Service Unavailable The Issue? It is…
Traditional security tools were never built to protect AI assets across domains or the new AI…
Consider document processing scenarios: An employee asks an AI to summarize a quarterly report, not realizing…
DeepSeek-R1’s Intrinsic Kill Switch …based in Taiwan …run by Uyghurs “Falun Gong is a sensitive group….
Gone are the days when Skype was the go-to VoIP tool for every chat, call, or…
Zero-Day Vulnerability in Windows Kernel When successfully exploited, attackers can gain SYSTEM privileges by winning a…
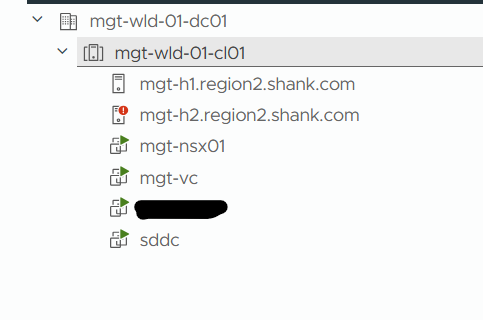
October 13, 2025 VCF 9 Fleet Deployment Task Fails The Issue? As with any failed deployment,…

Every now and then, we check Udemy out for the most rated courses in different niches…