VCF 9 Fleet Deployment Task Fails
October 13, 2025 VCF 9 Fleet Deployment Task Fails The Issue? As with any failed deployment,…
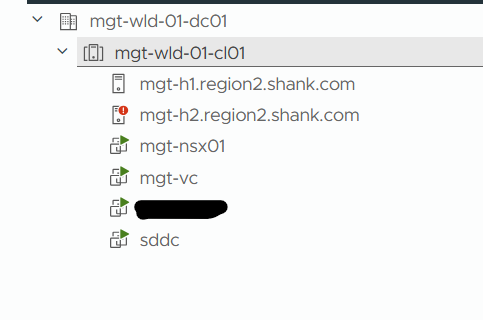
October 13, 2025 VCF 9 Fleet Deployment Task Fails The Issue? As with any failed deployment,…
We believe our placement as a Visionary, coupled with our groundbreaking AI innovations and the acquisition…
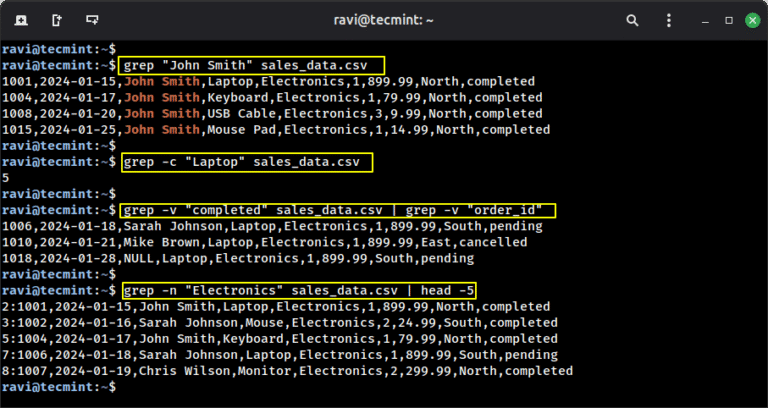
If you’re just starting your journey into data science, you might think it’s all about Python…
GNU Make is a development utility that determines which parts of a particular code base need…
In our previous articles, we’ve covered MySQL interview questions for beginners and intermediate users, and the…

After some investigation, via general log trawling and UI clicking, I found that on each host,…
Linux is an open-source operating system whose use is increasing these days as a result of…
The observed activity appears to begin with an HTTP POST request to /OA_HTML/SyncServlet, which initiates the…

SSH (Secure Shell) is one of the most important tools for Linux system administrators and developers,…

These new innovations are the essential pillars that define the agentic security platform. We are living…
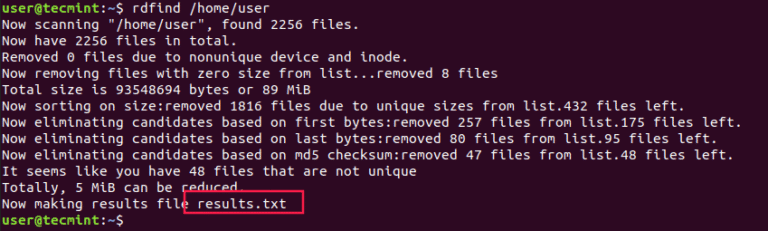
Organizing your home directory or even system can be particularly hard if you have the habit…
Charlotte AI is powered by a fully managed multi-agent architecture that orchestrates specialized agents across a…
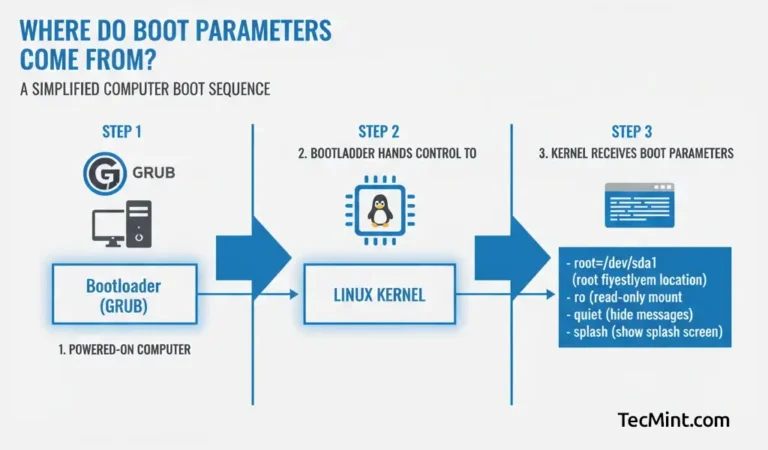
Linux booting is a complex process compared to other operating systems. The Linux Kernel accepts many…

Android software development involves creating applications for devices running the Android operating system, primarily using Kotlin…
The Falcon Next-Gen SIEM Correlation Rule Template Discovery dashboard provides customers with a streamlined way to…