Managing VM Power State with Ansible
Introduction vm_power_map:web01: powerondb01: powerofftest01: restart Playbook: vm_power_control.yml External Documentation: Diagram: VM Power Workflow Use Case Gracefully…
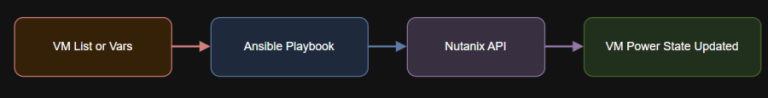
Introduction vm_power_map:web01: powerondb01: powerofftest01: restart Playbook: vm_power_control.yml External Documentation: Diagram: VM Power Workflow Use Case Gracefully…
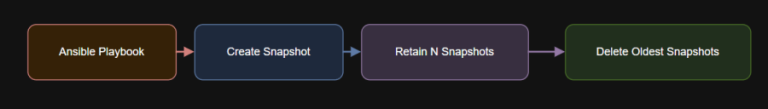
Introduction This playbook gives you complete control over Nutanix VM snapshots, ensuring consistency, compliance, and automation…

Like any other operating system, GNU/Linux has implemented memory management efficiently and even more than that….
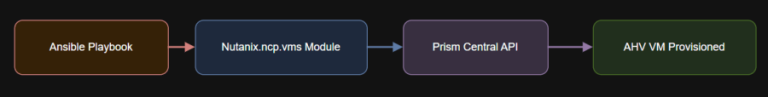
Introduction all:hosts:localhost:ansible_connection: local Step 2: Define Credentials File Once your Ansible control node is configured, deploying…
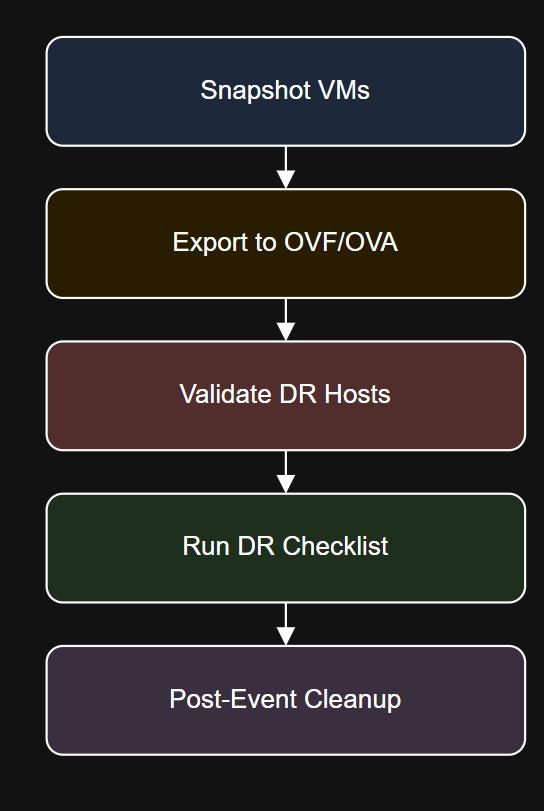
Introduction Get-ChildItem “D:VMBackups” -Filter *.ova | Where-Object {$_.LastWriteTime -lt (Get-Date).AddDays(-10)} | Remove-Item Diagram: DR Workflow with…
Here, we outline this attack and explain how the CrowdStrike Falcon® platform detects and successfully prevents…
Falcon Identity Protection is built for modern enterprises that demand comprehensive, unified, and automated identity security….
A system administrator’s routine tasks include configuring, maintaining, troubleshooting, and managing servers and networks within data…
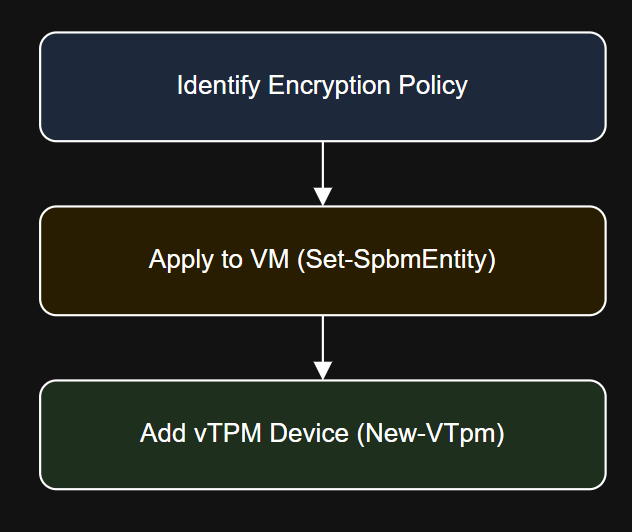
Introduction Security-sensitive workloads often require encryption at rest and support for virtual TPM (vTPM) devices. These…

If you’re managing multiple Ubuntu machines in a network, downloading updates and packages for each system…
Container Escape Vectors Let’s review some examples of container escape vectors. The progression from initial container…
Stopping Modern Attacks with AI and Expertise The Frost Radar™ serves as essential research for organizations…
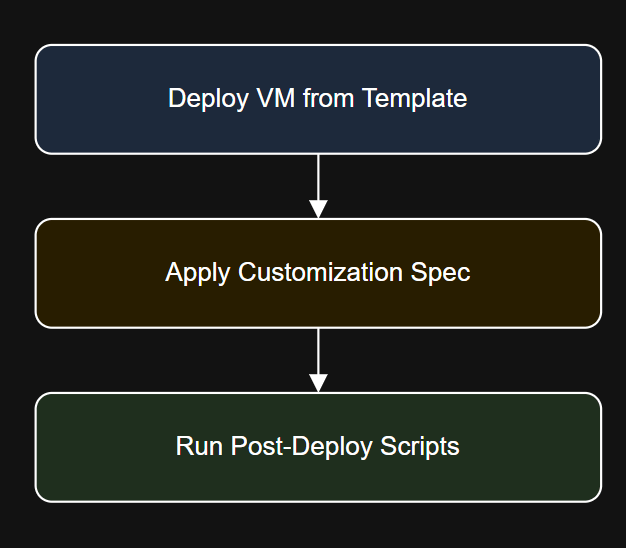
Introduction In the next article, we will cover: $servers = Import-Csv “C:ConfigsLinuxVMs.csv”You can store custom values…

If you’ve ever tried to set up HTTPS locally for development, you’ve probably run into a…
correlate( cmd: { #event_simpleName=ProcessRollup2 event_platform=Win FileName=”cmd.exe” ParentBaseFileName=”w3wp.exe” } include: [aid, ComputerName, TargetProcessId, ParentBaseFileName, FileName, CommandLine], pwsh:…