In terms of methodology, voice phishing and fake CAPTCHA pages have become key enablers for gaining access to targeted systems, which adversaries can use to pursue data theft and ransomware campaigns. In 2024 and 2025, CrowdStrike identified over 1,000 incidents that involved fake CAPTCHA lures affecting Europe-based organizations.North Korea strengthened its alliance with Russia, sending troops to support the war in exchange for advanced defense equipment and electronic warfare systems. The DPRK also expanded cyberattacks against Europe with its financially motivated targeting of defense, diplomatic, and financial entities to steal cryptocurrency and evade sanctions.
The war in Ukraine continued to shape the European cyber threat landscape. Russia-nexus adversaries targeted government, defense, and infrastructure networks with phishing attacks to collect intelligence and undermine Western support to Ukraine. Destructive attacks have continued to impact Ukrainian entities in an effort to disrupt systems and inflict psychological pressure on the Ukrainian population.
A Crowded and Complex Threat Landscape
Europe remains a prime target for global adversaries. Financially motivated eCrime groups continue to target the region as espionage and hacktivism escalate amid geopolitical turmoil stemming from ongoing conflicts.
State-sponsored adversaries from Russia, China, North Korea, and Iran expanded their regional targeting across industries.
Kinetic conflicts in the Middle East, particularly between Israel and Hamas, were the primary drivers of Iran-backed cyber operations and pro-Iran hacktivism toward European entities. Iran-nexus adversaries conducted operations across Europe, including espionage, hack-and-leak, and destructive campaigns. Multiple Iran-nexus threat actors masqueraded as hacktivists to obscure state-sponsored espionage efforts.
- Lucrative targets: Europe contains five of the world’s 10 most valuable companies. As BGH adversaries typically base ransom demands on a victim’s revenue, they likely believe European organizations can pay sizable amounts.
- Political motives: While BGH adversaries are primarily financially motivated, some have expressed political views and threatened politically motivated activity.
- Legal pressure: Adversaries have used the EU’s General Data Protection Regulation (GDPR) data breach penalties to pressure victims into paying; several threat actors have threatened to report entities for regulatory noncompliance via their DLS.
To stop these adversaries, organizations must first understand them. Here, we provide an overview of the report’s key findings and insights.
China-nexus threat actors have continued to target European organizations for intelligence collection, primarily by attacking edge devices and cloud infrastructure. Multiple China-nexus adversaries persistently focused on the government, healthcare, and biotechnology sectors, which were among the most consistently targeted sectors in Europe.
Geopolitical Turmoil Drives Nation-State Activity
The European cybercrime ecosystem remains active and adaptable. Online criminal marketplaces — including BreachForums, operated by threat actors in France and the UK — and encrypted applications connect initial access brokers, malware developers, and ransomware affiliates. Russian and English language forums are hubs where stolen credentials, data, and system access are sold. Telegram is often used to sell phishing kits and stolen login information.
As Europe’s cyber threat landscape continues to evolve, organizations must stay vigilant against a diverse array of adversaries, from cybercriminal groups to state-backed threat actors and hacktivists. With intelligence-driven security strategies, organizations across the region can strengthen their defenses, mitigate risks, and stay ahead of emerging threats.
Read the CrowdStrike 2025 European Threat Landscape Report to gain a full picture of the threats facing regional organizations and learn how to strengthen defenses against them.
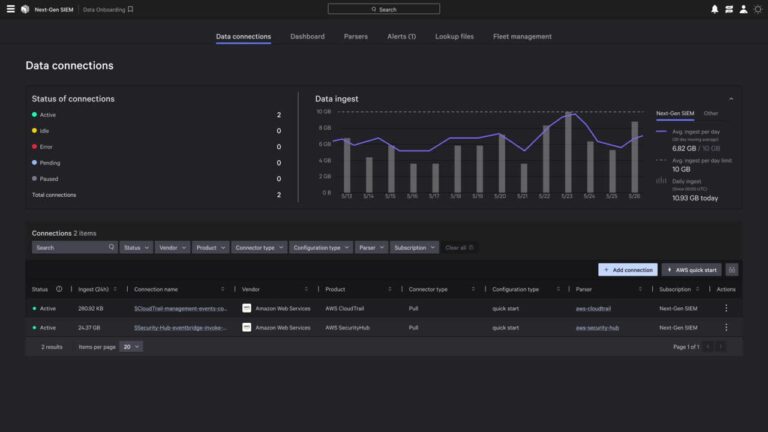
DLS data reveals the most-targeted European nations were the United Kingdom, Germany, Italy, France, and Spain. The most targeted sectors were manufacturing, professional services, technology, industrials and engineering, and retail.
Big game hunting (BGH) activity is prolific across the region. European organizations made up nearly 22% of entities named on dedicated leak sites (DLSs) that CrowdStrike Counter Adversary Operations tracks, making it the second most-targeted region after North America. Since January 1, 2024, BGH threat actors have named approximately 2,100 Europe-based victims on more than 100 data extortion and ransomware DLSs.
The CrowdStrike 2025 European Threat Landscape Report, based on frontline intelligence from CrowdStrike’s elite threat hunters and intelligence analysts, provides a definitive view of adversaries operating within or targeting Europe. It delivers information organizations need to anticipate threats, strengthen their defenses, and stay ahead as adversaries become faster, stealthier, and more destructive.
Entities in Europe are increasingly targeted by BGH adversaries, likely due to the following reasons: