How the Falcon Platform Delivers Fast, CISO-Ready Executive Reports
These reports include:With Falcon Cloud Security data correlated in Falcon Next-Gen SIEM, teams can detect cross-domain…

These reports include:With Falcon Cloud Security data correlated in Falcon Next-Gen SIEM, teams can detect cross-domain…
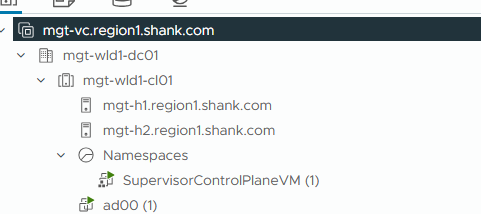
November 7, 2025 vCenter Supervisor Management is Blank Enabling / Disabling Supervisor Management Errors The Issue?…

The “404 Not Found” error during upgrade occurs when your system attempts to download packages from…
This blog includes descriptions of products, features, or functionality that may not be currently generally available….
While these agents can expedite individual tasks, their ultimate potential is realized when they operate in…
Key capabilities:Using the single Falcon sensor, organizations can move from deployment to complete XIoT visibility in…
Debian offers several tools for managing software packages, each serving a specific purpose in the package…
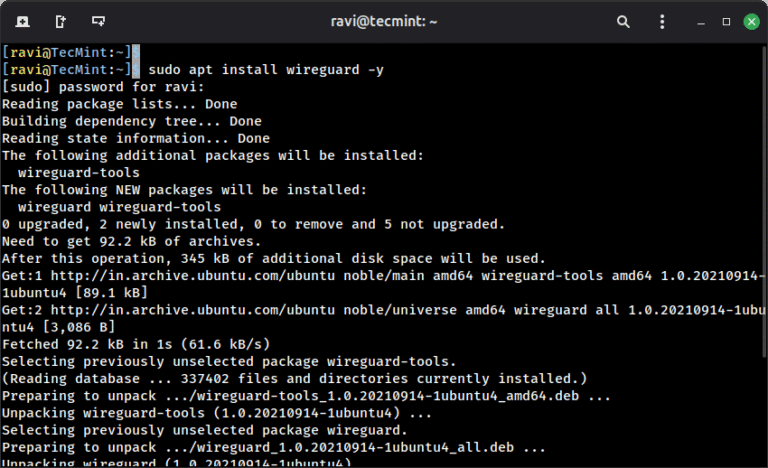
When you connect to a coffee shop’s WiFi or access the internet from any public network,…
In terms of methodology, voice phishing and fake CAPTCHA pages have become key enablers for gaining…

Earlier this year, in testing against ransomware attacks, SE Labs employed realistic scenarios using tactics and…
Frost & Sullivan also praised how CrowdStrike both secures AI agents and leverages agentic AI for…
Coerced Authentication The initial reconnaissance and setup phase requires minimal resources but careful planning. The attack…
AI-enhanced social engineering poses particular challenges. Attackers use generative AI to craft contextually appropriate phishing emails…
This isn’t just about saving time. It’s about enabling every stakeholder to see, understand, and act…
The eCrime threat landscape in the Asia Pacific and Japan (APJ) region is quickly evolving, driven…