How to Run Windows Software & Games on Linux with CrossOver 25
Running Windows software and games on Linux has become increasingly accessible, thanks to tools like CrossOver…

Running Windows software and games on Linux has become increasingly accessible, thanks to tools like CrossOver…
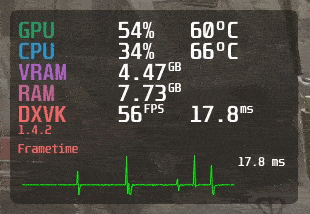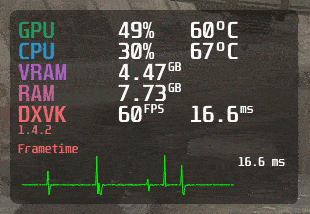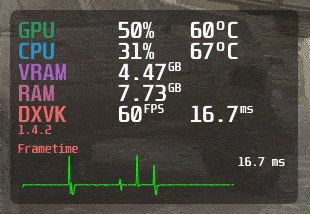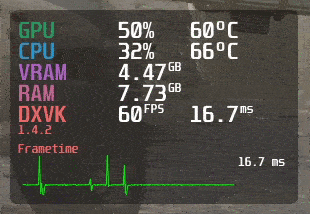
MangoHud is a powerful and lightweight tool designed for gamers, developers, and anyone who wants to…
Subdomain takeovers are not just about visibility — they provide adversaries with a legitimate-looking platform to…
The aforementioned processes would likely take weeks or even months when totaling hundreds of terabytes and…
Actively Exploited Zero-Day Vulnerability in Microsoft Management Console Microsoft Management Console received a patch for CVE-2025-26633,…
One of the biggest contributors to ecommerce waste is excessive packaging. Brands are shifting toward biodegradable,…
“By moving to Falcon Complete, we saw a drop in our operational expense on cybersecurity by…
CrowdStrike researchers have developed a next-gen method to train byte-based Transformer blocks that help models “understand”…
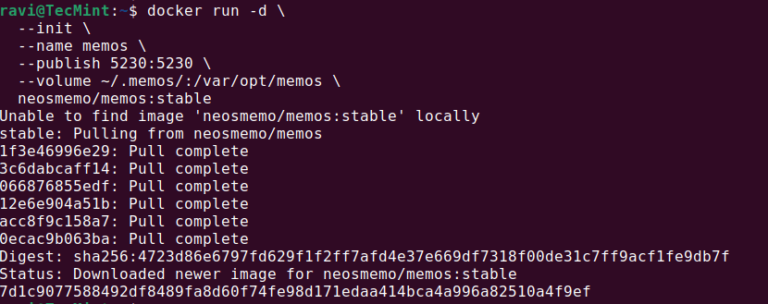
In today’s digital world, taking notes is essential for organizing ideas, keeping track of tasks, and…
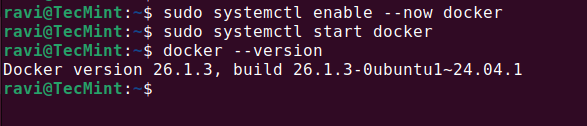
Managing Docker containers using the command line can be challenging, especially for beginners, which is why…
This integration will provide an in-depth understanding of how threats impact interconnected applications and endpoints. In…
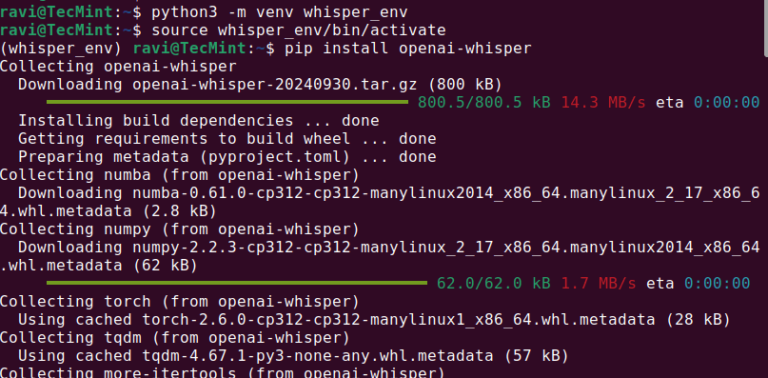
Whisper AI is an advanced automatic speech recognition (ASR) model developed by OpenAI that can transcribe…
They detect techniques across the entire cyber kill chain with out-of-the-box correlation rules mapped to both…
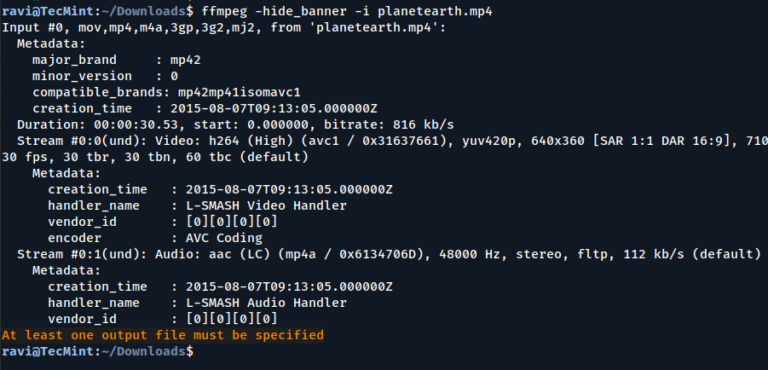
FFmpeg is a powerful command-line tool used for handling multimedia files, including editing metadata, which contains…
1. Initial Entry and Exploitation After gaining initial access, the adversary moved laterally through the network…